Protection ends where visibility stops
When MSPs don’t see the full picture, challenges multiply.
Alert noise becomes risk
When everything is urgent, real threats get missed—and technicians burn out.
Security doesn’t scale the way MSPs need
Manual onboarding, fragmented tools, and alert overload block growth.
Reputation risk becomes revenue risk
When customers are the first to notice problems, trust declines and revenue follows.
What sets ConnectWise SIEM apart
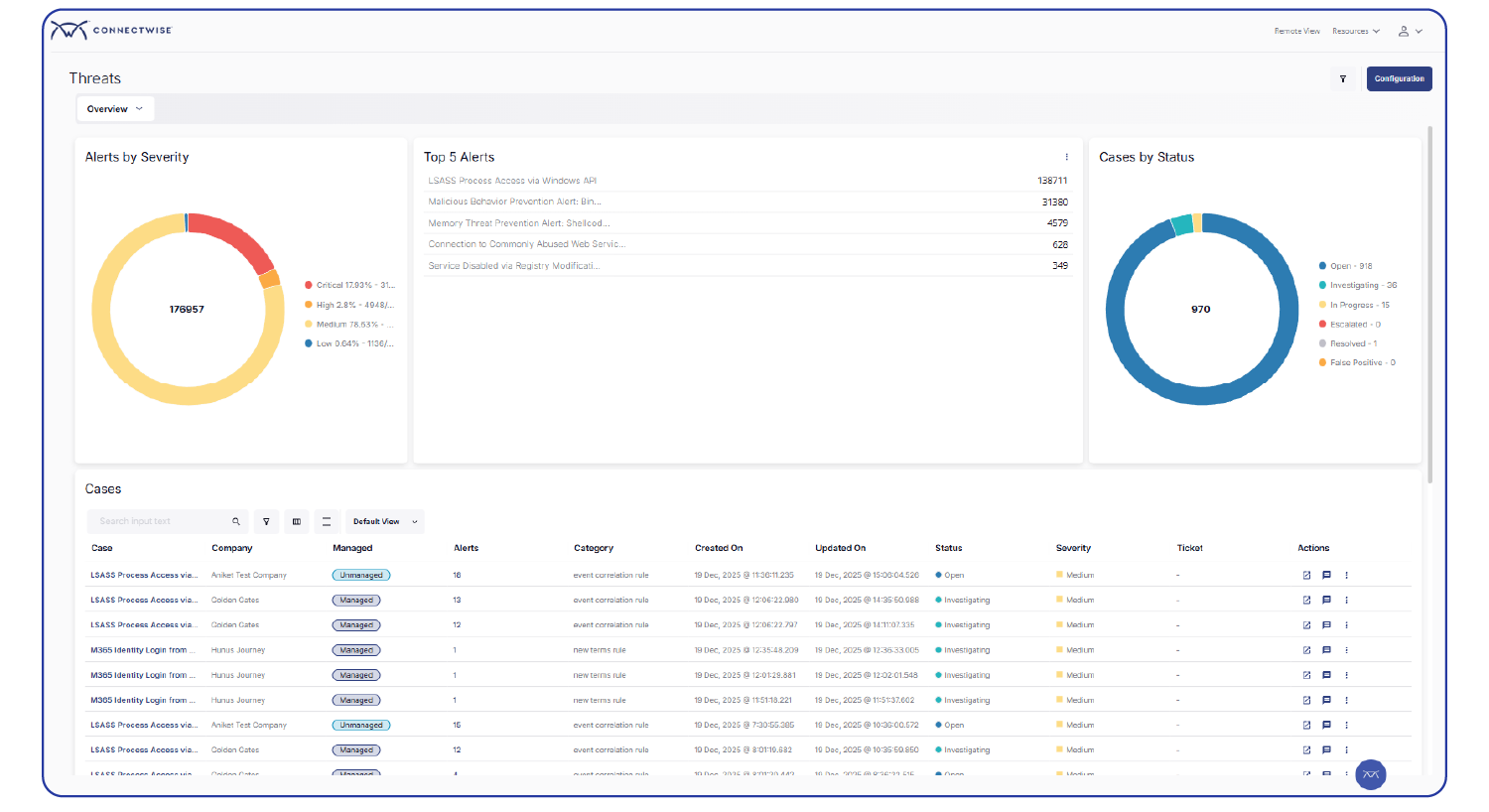
Go live faster with reduced operational friction
- Instant SOC, Day One – Get immediate access to a 24/7/365 ConnectWise SOC—no hiring, training, or ramp-up required. Deliver mature, SOC-backed security from the moment you turn it on.
- Deploy in minutes, not months – Launch SIEM in minutes with a simple, agent-based deployment. No complex builds, long onboarding cycles, or dedicated SIEM expertise required.
- Reduced complexity by design – Simplify day-to-day operations with automated integrations, tuning, and monitoring so your team can focus on responding, not managing tools.
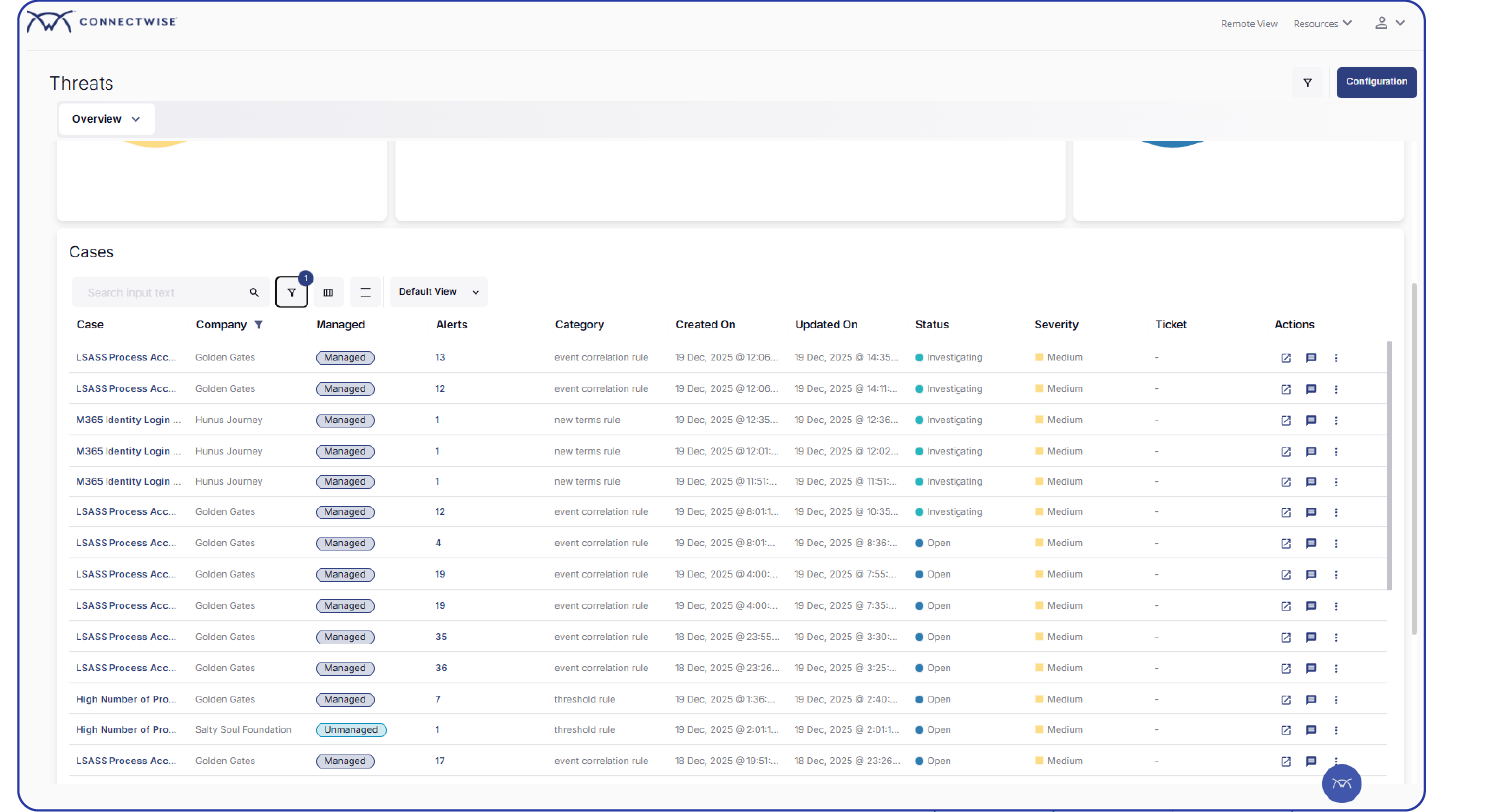
Deliver enterprise-grade security at MSP scale
- Visibility beyond the endpoint – Detect threats across endpoints and networks, and extend visibility into SaaS and identity where modern attacks happen.
- Enterprise-Grade security without enterprise overhead – Deliver SOC-backed, enterprise-level security without adding headcount, burning out your team, or inflating operational costs—while accelerating time to revenue.
- Predictable, per-user pricing – Eliminate unpredictable cost spikes with simple per-user pricing that makes SIEM easy to package, forecast, and scale profitably.
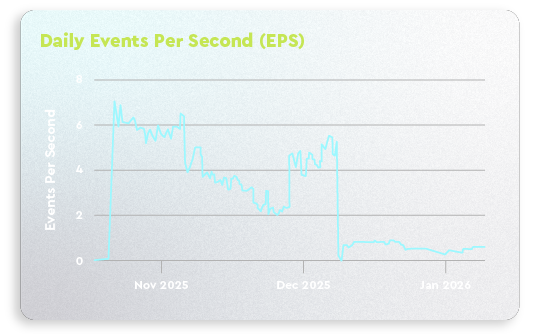
Scalable protection for every environment
Options for every MSP and IT organization, regardless of size or maturity. Explore which one is right for you.
SIEM Essentials: Core security coverage for modern hybrid environments
Deliver fast, effective threat detection for endpoints and Microsoft 365—without the complexity or unpredictable costs of a traditional SIEM solution. SIEM Essentials is designed to help MSPs launch trusted security services quickly and profitably.
- Modern SIEM – Centralize logging, alerting, reporting and correlation.
- Endpoint Protection – Defend against ransomware and malware at the endpoint.
- Identity Protection – Secure your environments with Identity Threat Detection and Response for Microsoft 365.
- Reporting – Surface trends and insights with a 30-day retention window.
- Essential Integrations – Connect seamlessly to Microsoft 365, Elastic Defend, and Windows/Max/Linux endpoint security logs.
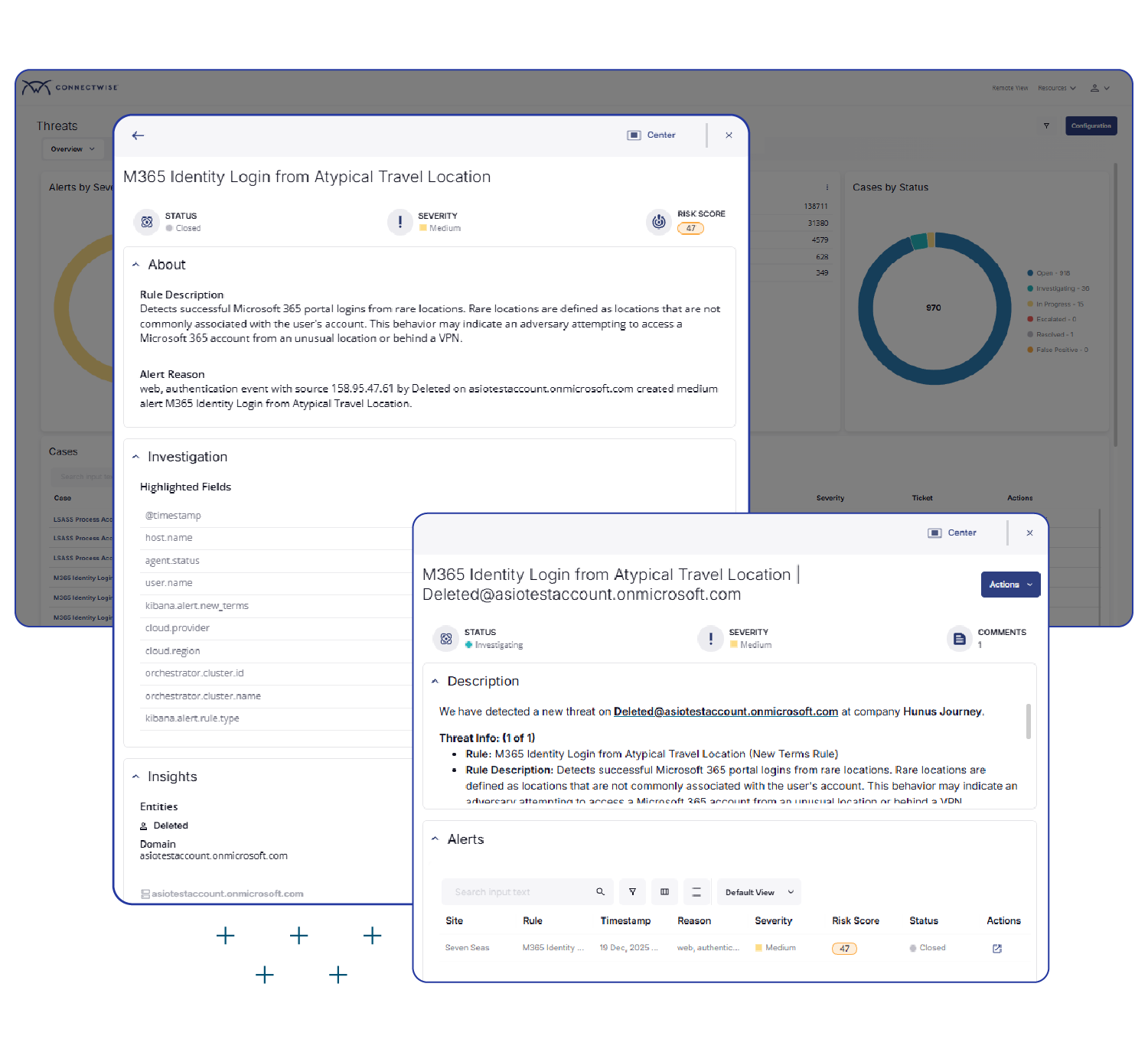
SIEM Pro: When full visibility and rapid response are must-haves
Expand threat detection across complex or regulated environments. With longer data retention and broader integrations, SIEM Pro delivers deeper visibility and control where it matters most.
- Everything in Essentials, plus...
- Endpoint Additions – Provide enhanced endpoint protection, including memory-based threat detection and behavioral attack prevention.
- Dozens of SaaS and Network Integrations – Leverage built-in connections to the most popular and widely used solutions, including Microsoft, Bitdefender, SentinelOne, Meraki, Proofpoint, Slack, and many more.
- Extended Data Retention – Simplify compliance and stay audit-ready with flexible retention from one to seven years.
Extend your visibility with ConnectWise’s robust library of SIEM Pro integrations

Managed SIEM: Scale on-demand with 24/7 SOC support
Built for SIEM Pro and Essentials, manage all clients or just a few so your team can focus on high-value work and revenue generation while the ConnectWise SOC delivers:
- 24/7 threat monitoring, detection, and alerting.
- MSP-specific threat intelligence enhanced with CRU research and reporting.
- Expert-led incident response to contain and neutralize threats quickly.
FAQs & Resources
Learn more about SIEM solutions
Frequently Asked Questions (FAQs)
What is SIEM?
SIEM stands for Security Information and Event Management. It is a cybersecurity technology that combines security information management (SIM) and security event management (SEM) to provide real-time monitoring, threat detection, and incident response capabilities.
What is a SIEM tool?
A SIEM tool is a software solution that collects and analyzes security event logs and data from various sources within an organization's IT infrastructure. It helps in identifying potential security incidents, correlating events, and providing actionable insights to security teams.
How to pronounce SIEM?
SIEM is pronounced either as "sim" or "seem."
How to select the best SIEM software provider for your needs?
When selecting a SIEM provider, consider factors such as their experience in the industry, the scalability of their solution, and their ability to integrate with your existing security infrastructure. Evaluate the features and capabilities of their SIEM solution, including log collection, event correlation, threat intelligence integration, and reporting. Additionally, consider their support services, pricing model, and the level of customization they offer to meet your specific needs.
Is SIEM a firewall?
No, SIEM is not a firewall. While both SIEM and firewalls are important components of a comprehensive cybersecurity strategy, they serve different purposes. A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. On the other hand, SIEM is a technology that collects and analyzes security event logs and data from various sources to detect and respond to security incidents.
What are the key features of a SIEM tool?
Key features of a SIEM tool include log collection and aggregation, event correlation and analysis, real-time monitoring, threat detection and alerting, incident response workflows, compliance reporting, and integration with other security tools and technologies.
How does SIEM work?
SIEM software works by collecting and aggregating security event logs and data from various sources, such as network devices, servers, endpoints, and applications. It then applies correlation rules and algorithms to identify patterns and anomalies that may indicate security incidents. SIEM tools provide real-time monitoring, alerting, and reporting capabilities to help security teams detect and respond to threats effectively.
How do security professionals interact with SIEM tools?
Security professionals interact with SIEM software through a user interface or dashboard provided by the SIEM solution. They use this interface to configure and manage the SIEM system, define correlation rules, monitor security events and alerts, investigate incidents, and generate reports. The SIEM tool provides visualizations, search capabilities, and other tools to facilitate efficient analysis and response to security events.
SOAR vs. SIEM?
SOAR (security orchestration, automation, and response) and SIEM are complementary technologies that serve different purposes. SIEM software focuses on log collection, event correlation, and real-time monitoring for threat detection and response. SOAR, on the other hand, automates and orchestrates security processes and workflows, enabling faster and more efficient incident response. While SIEM provides the foundation for threat detection, SOAR enhances the incident response capabilities by automating repetitive tasks, integrating with various security tools, and facilitating collaboration among security teams.
Related solutions
CONNECTWISE SIEM
Have more questions?
Our sales team and product experts can help. Fill out the form below and someone will reach out shortly.


















