Latest Advisories
From time to time, ConnectWise will provide communications on broader security related topics that may not be linked to a specific ConnectWise product or vulnerability, but are still of importance to our partner community.
December 18, 2025: ConnectWise Best Practice Advisory – ScreenConnect™ Certificate Signing Extension Handling
ConnectWise is committed to the ongoing security and hardening of our products. As part of this commitment, we conduct regular architecture reviews and participate in coordinated vulnerability disclosure programs.
As a result of these efforts, recent enhancements strengthen the extension framework by improving how extension configuration values are processed and handled. These changes ensure that configuration data is managed entirely on the server side and is no longer rendered or exposed through client-facing components.
This framework-level hardening includes specific improvements to the Certificate Signing extension. With the updated extension, configuration values associated with the signing workflow are handled exclusively within the server environment, preventing encrypted configuration data from being returned to unauthenticated users.
In scenarios where extensions are misconfigured or customized outside recommended practices, the likelihood of unintended behavior may increase. Updating the Certificate Signing extension to version 1.0.12 or higher introduces server-side controls designed to mitigate this class of issue, and partners are encouraged to review extension configurations as part of routine maintenance.
This advisory is provided to offer partners visibility into these architectural improvements and to share best-practice guidance related to extension configuration handling in ScreenConnect.
What Partners Should Know
- Recent updates to the ScreenConnect extension framework improve how extension configuration data is handled and protected.
- ScreenConnect cloud environments are automatically updated as part of standard operations and already include these enhancements; no action is required for cloud-hosted partners.
- On-premises partners should ensure the Certificate Signing Extension is updated to version 1.0.12 or higher to address this issue and benefit from the latest security improvements.
- All partners are encouraged to keep ScreenConnect extensions up to date as part of routine maintenance.
Best Practice Guidance
As part of our ongoing security advocacy, partners are encouraged to:
- Keep all ScreenConnect extensions up to date to ensure the latest security hardening and quality improvements are applied.
- Review and manage extension usage, installing only those extensions required for operational needs.
- Limit access to administrative and configuration interfaces to authorized personnel and regularly review access activity.
- Follow good credential hygiene practices for integrations and service accounts, including avoiding long-lived credentials, rotating secrets on a regular schedule, and managing credentials through a documented and monitored process.
Support and Resources
Partners are encouraged to ensure the ScreenConnect Certificate Signing Extension is updated to version 1.0.12 or higher to address the behavior described in this advisory.
- For additional information related to extension configuration and management, please reference the following documentation:
Certificate Signing - ConnectWise
If you have questions or need assistance related to ScreenConnect or any security matter:
- Visit ConnectWise Home to open a case, connectwise.com/chat, or email help@connectwise.com for additional support.
- To stay informed about the latest security updates and information, we strongly recommend that all partners regularly visit and/or subscribe to our Security Trust Page and RSS alerts.
September 25, 2025 Salesloft+Drift/Salesforce: ConnectWise Response
August 25, Salesloft announced a breach impacting their customers with the Salesforce-Drift integration, allowing unauthorized access to customers’ Salesforce data. Drift is an AI chat agent. ConnectWise was impacted along with hundreds of other organizations. No ConnectWise products or services were impacted. A limited number of business contact fields were accessed; no sensitive data was involved.
System(s) impacted
Salesforce (ConnectWise enterprise tool)
What we know
ConnectWise was impacted along with hundreds other organizations.
Our response
As soon as we learned of the event, our security team launched an investigation, and we followed the prescribed recommendations. Our investigation confirmed:
- this event was isolated to Salesforce;
- no ConnectWise products or services were impacted;
- in ConnectWise's Salesforce data, no proprietary data, sensitive information, or PII was compromised. Only a small number of business names and publicly available contact details were accessed.
We take this situation seriously and are monitoring the situation. If further analysis determines sensitive data was accessed or misused, we will notify any affected individuals or organizations consistent with our contractual obligations and applicable regulatory requirements.
If you have concerns or need additional support, please contact ConnectWise support.
Remediation
None
June 9, 2025 Code Signing Certificate Rotation for ScreenConnect, ConnectWise Automate and RMM
The security of our partners and trust in our products are paramount to ConnectWise. We are updating the digital signing certificates used in ScreenConnect, ConnectWise Automate, and ConnectWise RMM due to concerns raised by a third-party researcher about how ScreenConnect handled certain configuration data in earlier versions. In addition to issuing new certificates, we are releasing an update to improve how this configuration data is managed in ScreenConnect.
This issue does not involve a compromise of our systems or certificates (including the event described in our May 28, 2025 Security Advisory). However, based on recent requirements from our technology partners, we are required to rotate our certificates by Friday, June 13 at 8:00 p.m. ET (June 14, 12:00 a.m. UTC). ConnectWise received this extended deadline Monday evening.
We had already planned enhancements to certificate management and product hardening, but these efforts are now being implemented on an accelerated timeline. We understand this may create challenges and are committed to supporting you through the transition.
On-Premises Solutions
Customers using on-premises versions of ScreenConnect or Automate must update to the latest build and validate that all agents are updated before June 13 at 8:00 p.m. ET (June 14, 12:00 a.m. UTC) to avoid disruptions or degraded experience.
- Automate on-premises build is available now.
- ScreenConnect on-premises build is available now.
Please visit our ConnectWise University page for download links, version details, and step-by-step instructions.
Cloud Solutions
We are in the process of automatically updating certificates and agents across all cloud instances of Automate and RMM. These updates are being deployed progressively. We recommend validating that your agents are running the latest version prior to the June 13 deadline to ensure continued service.
For ScreenConnect cloud instances, we are finalizing the updated build, which will also be deployed automatically once ready.
Resources and Support
For product-specific instructions, agent version information, and a FAQ, please visit the ConnectWise University page. This page will be continuously updated with the latest guidance and answers to common questions.
If you need additional assistance, please contact our support team via live support chat.
We appreciate your continued partnership and are committed to addressing this matter with urgency and care to ensure minimal impact to your business.
May 28, 2025 Security Event Advisory
ConnectWise recently learned of suspicious activity within our environment that we believe was tied to a sophisticated nation state actor, which affected a very small number of ScreenConnect customers. We have launched an investigation with one of the leading forensic experts, Mandiant. We have contacted all affected customers and are coordinating with law enforcement. As part of our work with Mandiant, we implemented enhanced monitoring and hardening measures across our environment. We have not observed any further suspicious activity in any customer instances. The security of our services is paramount to us, and we are closely monitoring the situation and will share additional information as we are able.
Frequently Asked Questions
In addition to our statement provided on May 28, 2025, please find below frequently asked questions for reference.
What happened
- ConnectWise recently learned of suspicious activity within our environment that we believe was tied to a sophisticated nation state actor, which affected a very small number of ScreenConnect customers. We immediately launched an investigation with assistance from the leading forensics experts, Mandiant.
- As part of our work with Mandiant, we implemented enhanced monitoring and hardening measures across our environment.
- We issued a patch and have not observed any further suspicious activity in ScreenConnect cloud instances since the patch was implemented.
- We have contacted all affected customers.
Which of your products were affected?
- At this time, our investigation indicates that activity was isolated to ScreenConnect. We have not observed any additional suspicious activity in ScreenConnect cloud instances since the patch was released on April 24. Our investigation is ongoing, and we will share additional information as we are able.
Is ScreenConnect safe to use?
- We have not seen any suspicious ScreenConnect activity since releasing the patch on April 24.
What about on-premise ScreenConnect customers?
- Please see the April 24th Security Patch Advisory below for instructions to update on-premise ScreenConnect servers to a patched release.
Am I impacted?
- We have contacted all affected customers.
How many customers were impacted?
- It is a very small number.
- We have completed initial outreach to all affected customers.
Was the compromise due to a vulnerability in ScreenConnect?
- We are currently focused on ensuring that the impact to partners and partner-facing systems is identified and remediated. The patch that we issued and the additional monitoring we put in place addresses the previously mentioned activity. Our investigation is ongoing, and we will share additional information as we are able.
Was ransomware involved?
- No, it has been determined that this was not a ransomware attack. The suspicious activity has been tied to a nation state threat actor that is known for intelligence collection.
Is this related to last year’s vulnerability?
- No, this is not related. The suspicious activity has been tied to a nation state threat actor that is known for intelligence collection.
April 24, 2025 ScreenConnect Security Patch Advisory
What we know
In December 2024, Microsoft Threat Intelligence detected misuse of publicly available ASP.NET machine keys to inject malicious code and deploy a post-exploitation framework. Microsoft found that publicly accessible keys were being utilized to perform malicious actions on servers generally. It is important to note that to obtain these machine keys, privileged system level access must be obtained. Reference: https://www.microsoft.com/en-us/security/blog/2025/02/06/code-injection-attacks-using-publicly-disclosed-asp-net-machine-keys/ .
We are taking proactive steps to mitigate any potential impact on partners regarding this identified ASP.NET weakness. In line with our commitment to Secure by Design, ConnectWise is releasing a patch to reduce the risk of ViewState abuse and further harden the attack surface.
What are ViewState code injection attacks?
According to Microsoft, ASP.NET Web Forms utilize ViewState to maintain page and control state, storing data in a hidden field encoded with Base64. To protect against tampering, ASP.NET employs machine keys like ValidationKey for creating a message authentication code (MAC) and DecryptionKey for encryption. If these keys are compromised, attackers could craft a malicious ViewState using the stolen keys, sending it via a POST request to the website. When processed, the ASP.NET Runtime decrypts and validates the ViewState with the correct keys, enabling the execution of malicious code in the server's memory and granting threat actors remote code execution capabilities on the ASP.NET framework. Reference: https://www.microsoft.com/en-us/security/blog/2025/02/06/code-injection-attacks-using-publicly-disclosed-asp-net-machine-keys/
Our response
Our cross-functional teams conducted comprehensive assessments of all our Cloud instances to identify any potential areas of risk. Additionally, we have implemented enhanced monitoring measures to actively track any changes or suspicious activities related to this issue. Meanwhile, our engineering team effectively identified and implemented a product level patch in the ConnectWise ScreenConnect Cloud. Partners who are on premises must patch their ScreenConnect instance immediately.
Remediation
Cloud partners
No action is required. ScreenConnect servers hosted in “screenconnect.com” cloud (standalone and Automate/RMM integrated) or “hostedrmm.com” for Automate partners have been updated to remediate the issue.
On-premises partners
On-premise: Active maintenance
If you are on active maintenance, we strongly recommend upgrading to the most current release of 25.2.4. Using the most current release of ScreenConnect includes security updates, bug fixes, and enhancements not found in older releases.
To upgrade to version 25.2.4, please note there is a specific upgrade path that must be followed:
22.8 → 23.3 → 25.2.4
For instructions on how to upgrade your on-premise installation click here .
On-premise: Off maintenance
We recommend renewing maintenance and upgrading to the newest release, 25.2.4. Please see the above instructions for how to upgrade to the newest version of ScreenConnect and to check your maintenance status.
If you elect not to renew maintenance, we have released free security patches for select older versions dating back to release 23.9. Versions of ScreenConnect can be downloaded from the ConnectWise website: https://screenconnect.com/download/archive . The updated releases will have a publish date of April 22nd, 2025, or later. Partners on a version older than 23.9 will be able to upgrade to 23.9 at no additional charge.
For help with upgrading visit ConnectWise Chat to open a case or email help@connectwise.com for additional support.
For questions regarding maintenance, please contact screenconnectsales@connectwise.com or call +1-813-514-8400.
If you have additional questions, please contact security@connectwise.com. To report a security or privacy incident, please visit the ConnectWise Trust Center.
January 30, 2025 Phishing Alert: Staying Vigilant Against Phishing Attempts
As part of the broader trend of increased phishing activity during tax season, we have seen attempts to impersonate legitimate ScreenConnect login alerts. These emails are designed to look authentic, encouraging recipients to click on malicious links. While phishing remains a common cybersecurity challenge, attackers continuously refine their tactics, making awareness and proactive security measures more important than ever.
To help protect against these attempts, we recommend verifying URLs before clicking on any links and following defense-in-depth security best practices.
A key detail to remember: Legitimate ScreenConnect login alerts never include a "click here" link. If you receive an email with such a link, it is not from ConnectWise.
Below is an example of a phishing email designed to appear as an official login alert.
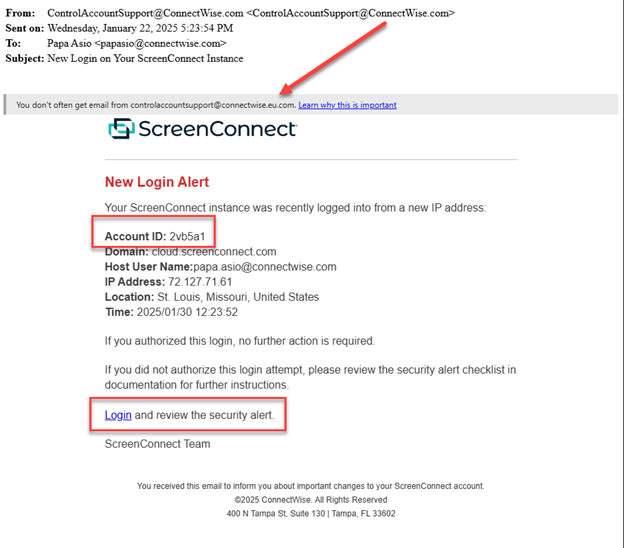
Please note, ScreenConnect does send legitimate new login alerts via email as shown in this screenshot. ConnectWise alerts do not have a “click here” link for any login notifications. If you see a link in your notification, it is not legitimate. It is also important to note that the Account ID will never match your actual account ID. Either of these two indicators is a clear giveaway to the phishing campaign.
What should you look for?
We encourage our partners to stay vigilant in looking for clues to avoid mistakenly clicking on nefarious content. Before clicking, make sure content reflects:
- Verify the Sender: Always check the sender's email address. Ensure the domain matches a trusted source. Be wary of slight variations in spelling or unusual top-level domains (e.g., screenconect.net or screenconnect.com.eu).
- Inspect Links: Hover your mouse over any links without clicking to see the actual URL. Verify that it points to a legitimate ConnectWise domain (e.g., cloud.screenconnect.com). Be extremely cautious of shortened URLs or links that redirect to unfamiliar sites. This is especially important during tax season when many phishing emails use tax-related keywords in the URL.
- No Links in Login Alerts: As mentioned above, legitimate ScreenConnect login alerts will never contain clickable links. Any email claiming to be a login alert with a link should be treated as suspicious.
- Defense in Depth: Beyond email security, ensure you have strong passwords, multi-factor authentication (MFA) enabled wherever possible, and up-to-date antivirus software. These measures are crucial year-round, but particularly important during periods of increased phishing activity like holidays and tax season.
What to Do If You Suspect a Phishing Attempt:
- Do Not Click: Do not click on any links or open any attachments in suspicious emails.
- Report It: Copy the email as an attachment and send it to Security@ConnectWise.com. Additionally, report it internally leveraging existing processes (Report Phish, Forward to IT, etc.) to ensure it is blocked appropriately.
If you are concerned that you may have been compromised, please follow the steps in this security alert checklist. We also recommend reviewing the ScreenConnect security guide and best practices for further securing your instance, as well as verifying that links, your account ID, and your domain are accurate.
If you have questions, suspect you received a phishing attempt, or need to report a security or privacy incident, please visit our ConnectWise Trust Center. You can report both a non-active security incident, report a security vulnerability, or call our Partner InfoSec Hotline at 1-888-WISE911.
March 21, 2024 Unauthenticated Access to Legacy AWS Server Located in the EU Region
We want to notify you of a security incident that we are currently investigating. Our team was notified by a security researcher of a vulnerability to a single AWS server in our EU environment. This server hosts a legacy service that we had targeted for deprecation. While our investigation is ongoing, we wanted to inform you of the potential risk associated with this incident.
Incident Details
Date and time: The vulnerability was initially reported on March 17. On March 18, we mitigated the vulnerability and subsequently, on March 20, we discovered there was unauthorized access to the AWS server.
Nature of access: The access appears to be unauthenticated, indicating a potential security breach.
Server location: The compromised single server is a legacy system in the AWS EU region.
Data at risk: Preliminary investigations suggest that the information viewable to an unauthorized party would be limited to the email addresses for a subset of individuals who had authenticated into the EU environment.
Actions Taken
Immediate response: Upon detection, our security team initiated immediate response protocols to contain the incident and mitigate any further potential risks.
Investigation: Our InfoSec team, working alongside an external forensics firm, have launched a thorough investigation into the incident to ascertain the extent of the unauthorized access and any potential malicious activity.
Potential Impact
We are treating this incident seriously and are thoroughly investigating with our InfoSec team as well as an independent external forensics firm. We believe that there was a finite amount of information available to be viewed by an unauthorized party (e.g., email address) and that an unauthorized party would not be able to expand access beyond the single AWS server.
The service in question is consumed by our legacy Continuum environments, however this issue is constrained to our EU implementation only. This service is not consumed by any of the other product lines such as PSA or Automate.
Throughout the day on March 21, the teams are running additional scans and tests and partners may experience some intermittent slowness or authentication issues during those times. We will do our best to limit the partner impact.
Next Steps
We will continue to share updates on the progress of our investigation and communicate directly to the small number of partners in the EU who may have been impacted.
Support
If you need any assistance or have additional questions, please go online to ConnectWise Home and open a case with our support team or email help@connectwise.com.
We appreciate your continued partnership.
March 4, 2024 Important Update: Hardening Guidelines for ConnectWise ScreenConnect CVE-2024-1708 (Path Traversal)
ConnectWise published a security bulletin and multiple communications regarding vulnerabilities found in ConnectWise ScreenConnect™ (CVE-2024-1709, CVE-2024-1708). As a reminder and as part of the remediation process for on-prem partners—whether you have patched your server or still need to—it is critical to assess your systems for signs of impact while upgrading and before bringing any systems back online.
If you possess enhanced Windows event logs or endpoint detection and response (EDR) solutions, thorough investigation should be conducted to identify any suspicious activity, including evidence of commands run from webshells or other indicators of compromise.
In the event file anomalies or other indicators of compromise are identified, it is highly recommended to seek assistance from external response companies specializing in incident response and digital forensics. These companies possess the expertise necessary to effectively investigate and remediate security concerns.
Cloud partners
Cloud partners are remediated against both vulnerabilities reported on February 19. No further action is required from any cloud partner (“screenconnect.com” cloud and “hostedrmm.com”).
On-premise partners
Whether you have patched your server or still need to, it is critical to assess your systems for signs of impact while upgrading and before bringing any systems back online.
Review file system, enhanced Windows event logs, or EDR solutions for suspicious activity, such as webshell commands or other compromise indicators.
Seek assistance from specialized incident response and forensics firms if potentially impacted files are identified.
To assist in the remediation and hardening process, we encourage partners to review and follow the ConnectWise ScreenConnect Remediation and Hardening Guide by Mandiant for additional protection.
Within the Mandiant-provided hardening guide, you will find additional mitigation and steps to check for signs of compromise, such as:
- Auditing rogue users, malicious extensions, and additional checks for indicators of compromise
- Enabling baseline audit and privacy logs
- Proxy server and load balance configurations
- Restricting Egress
- Additional details for restricting permissions
These steps should be reviewed and implemented after you have upgraded to a patched version of ScreenConnect.
We strongly urge all users of ScreenConnect to prioritize the installation of the latest patch and follow the recommended mitigation and hardening measures outlined in the provided resources to safeguard their systems against potential security risks.
February 21, 2024 ConnectWise ScreenConnect Vulnerability CWE-288: What Should I Do?
February 29, 2024 update:
Cloud partner summary:
Cloud partners are remediated against both vulnerabilities reported on February 19. No further action is required from any cloud partner (“screenconnect.com” cloud and “hostedrmm.com”).
On-prem partner summary:
On-prem partners are advised to immediately upgrade to the latest version of ScreenConnect to remediate against reported vulnerabilities.
Active maintenance:
If you are on active maintenance, we strongly recommend upgrading to the most current release of 23.9.8 or later. Using the most current release of ScreenConnect includes security updates, bug fixes, and enhancements not found in older releases.
Off maintenance:
ConnectWise has provided a patched version of 22.4.20001 available to any partner regardless of maintenance status as an interim step to mitigate the vulnerability. If you are not currently under maintenance, please upgrade your servers to version 22.4.20001 at minimum or to your latest eligible patched version that includes the remediation for CVE-2024-1709.
Upgrade ScreenConnect to a patched version immediately:
1. To upgrade to version 23.9.8 or later, please note there is a specific upgrade path that must be followed:
2.1 → 2.5 → 3.1 → 4.4 → 5.4 → 19.2 → 22.8 → 23.3 → 23.9.8+
2. If you are not on maintenance and upgrading to 22.4.20001 (or your latest eligible version), please follow this specified upgrade path:
2.1 → 2.5 → 3.1 → 4.4 → 5.4 → 19.2 → 22.4.20001
For instructions on how to upgrade your on-premise installation, click here.
Addressing license errors
If a license error arises during the upgrade, please stop the four ScreenConnect services (Session Manager, Security Manager, Web Server, Relay), move the “License.xml” file from the installation folder: C:\Program Files (x86)\ScreenConnect\App_Data\License.xml to another location such as Desktop, and proceed with the upgrade. After the upgrade is complete, the license key will need to be re-added by stopping the four services and dropping the file back into the App_Data folder.
February 21 original advisory:
If you suspect you have been compromised related to the recent ConnectWise ScreenConnect™ vulnerability (CWE-288), please follow the mitigation steps below.
1. Upgrade ScreenConnect to the current 23.9.8 version immediately
- Please note, there is an upgrade path that must be followed:
2.1 → 2.5 → 3.1 → 4.4 → 5.4 → 19.2 → 22.8 → 23.3 → 23.9 - Click here to upgrade your on-premise installation
2. If you receive a license error when upgrading, it may be due to a technical problem on the server, or the license key itself may need to be renewed.
If the upgrade cannot be completed, please delete the SetupWizard.aspx file from the installation folder:C:\Program Files (x86)\ScreenConnect\SetupWizard.aspx
Please see the February 29, 2024 advisory update to review the amended upgrade path and instructions on how to address licensing errors.
3. Identify the issue
- When compromised, the User.xml file on the ScreenConnect instance is reset and replaced with a new file that contains only information about one new user:
C:\Program Files (x86)\ScreenConnect\App_Data\User.xml - This file can be restored from a backup to get the original users back (if applicable)
- If you don’t have a user backup, the user file can be reset again by following the process outlined here.
4. Once you are able to log in, check for malicious commands/tools or connections.
- Install the Report Manager extension from Admin > Extensions > Browse Extension Marketplace
- Launch Report Manager from Admin > Extras menu (4x boxes lower left corner) > Report Manager
- Use pre-built reports to export data as CSV (default: last 30 days)
- Host Session Connections — shows all connections made to devices
- Queued Commands Example — shows all remote commands run against devices
- Queued Toolbox Items Example — shows all toolbox items that were queued up
Support
If you need any assistance or have additional questions, please go to ConnectWise Home and open a case with our support team or email help@connectwise.com.
Report a Security Incident
If you have questions or need to report a security or privacy incident, please visit our ConnectWise Trust Center. You can also call our Partner InfoSec Hotline at 1-888-WISE911 to report a non-active security incident or a security vulnerability.
February 20, 2024 Patch Immediately — Critical ScreenConnect Vulnerability
Update:
Indicators of Compromise
Indicators of compromise (IOCs) help identify malicious activity or threats. These indicators can be incorporated into your cybersecurity monitoring platform to help stop a cyberattack in progress. They can also help detect and prevent ransomware, malware, and other cyberthreats before they cause data breaches.
We received updates of compromised accounts that our incident response team has investigated and confirmed. The following IP addresses were recently used by threat actors and are being shared for protection and defense:
- 155.133.5.15
- 155.133.5.14
- 118.69.65.60
We will continue to update with any further information as it becomes available.
Original Advisory:
Summary
At ConnectWise, our top priority is upholding our commitment to deliver and maintain secure products for our partners. Our team has been working around the clock to ensure your protection from the issues affecting the latest ConnectWise ScreenConnect™ vulnerability that was responsibly reported to us through our vulnerability disclosure process.
Product(s) Impacted
ConnectWise ScreenConnect™, including ScreenConnect instances co-hosted on ConnectWise Automate™ cloud servers.
What We Know
Vulnerabilities were reported on February 13, 2024, through our vulnerability disclosure channel via the ConnectWise Trust Center. There is no evidence that these vulnerabilities have been exploited in the wild, but immediate action must be taken by on-premise partners to address these identified security risks.
Our Response
We have been following our escalated vulnerability response process, and thanks to the efforts of our teams, a patch was made available on February 19, 2024.
Remediation
It is strongly recommended that our on-premise partners not wait for a maintenance window to patch but immediately update to the latest ScreenConnect version 23.9.8.
More information on this vulnerability and detailed instructions on patch availability and how to mitigate the vulnerabilities can be found in this security bulletin.
Report a Security Incident
If you have additional security-related questions, please contact security@connectwise.com. To report a security or privacy incident, please visit the ConnectWise Trust Center. You can report both a non-active security incident, report a security vulnerability, or call our Partner InfoSec Hotline at 1-888-WISE911.
February 9, 2024 FortiSIEM Critical Vulnerabilities Affecting ConnectWise Co-Managed SIEM Powered by StratoZen
Fortinet has recently disclosed two critical vulnerabilities in its FortiSIEM platform: CVE-2024-23108 and CVE-2024-23109. These vulnerabilities affect the ConnectWise Co-Managed SIEM powered by StratoZen. Fortinet recommends upgrading to FortiSIEM version 7.1.3. All hosted StratoZen environments are protected by firewalls that block access to the vulnerable service. However, ConnectWise is proactively upgrading all hosted environments, and co-managed partners are strongly advised to upgrade as well.
What We Know
The vulnerability lies in an API used for communication between FortiSIEM components. Collectors do not use this API and are not impacted. ConnectWise environments do not expose this API externally, so the vulnerability cannot be exploited remotely.
Our Response
All hosted FortiSIEM instances are protected by firewalls that block the vulnerable port and service. Additionally, ConnectWise is upgrading all hosted FortiSIEM instances to version 7.1.3 over the next week.
Remediation
Hosted StratoZen Partners – No immediate action is required. All FortiSIEM instances are protected by firewalls and will be upgraded automatically.
Co-Managed StratoZen Partners – If you are a co-managed partner, please upgrade your FortiSIEM instance to version 7.1.3 immediately. Also, review your firewall settings to ensure only necessary ports are open. For assistance, contact supportdesk@stratozen.com.
Report a Security Incident
If you have additional security-related questions, contact security@connectwise.com. To report a security or privacy incident, visit the ConnectWise Trust Center or call the Partner InfoSec Hotline at 1-888-WISE911.
January 22, 2024 Brute-Force Attempts on ConnectWise ScreenConnect
What We Know
Our team recently noticed malicious activity by bad actors attempting credential-stuffing and brute-force attacks targeting some ConnectWise Automate partners with ConnectWise ScreenConnect instances. We are pleased to report that there is no evidence of any unauthorized access, and the security measures we have in place worked as intended to prevent any breach.
What Should You Do?
If you receive an email notifying you that you or someone in your company has been locked out of your ScreenConnect account, do not click on any suspicious links and reach out to our support team immediately for assistance in verifying the legitimacy of the lockout email and restoring access securely. To contact support, go to ConnectWise Home and log in to open a support ticket.
Preventative Security Measures
With the evolving sophistication of cyberattack attempts on the rise globally, it is critically important to maintain a security-first focus, remain vigilant, and follow best practices to ensure the ongoing safety and security of your information and systems.
- Multi-factor Authentication (MFA)
Implement MFA to add an extra layer of protection. This significantly reduces the risk of unauthorized access, even if login credentials are compromised. Learn more about enabling MFA: here and here. - Regular Password Policy Reviews
Enforce strong password policies for all users. Regularly review and update passwords to ensure they meet current security standards. Click here to edit user password requirements and configurations. - Employee Training and Awareness
Conduct regular security awareness training for your team to recognize phishing attempts and other social engineering tactics. Employees play a crucial role in maintaining a secure environment. - Incident Response Plan
Develop and regularly update an incident response plan. This ensures a swift and coordinated response in the event of a security incident, minimizing potential damage.
By following these best practices and promptly contacting our support team when needed, we can collectively strengthen our defenses against potential threats.
Report a Security Incident
If you have questions or need to report a security or privacy incident, please visit our ConnectWise Trust Center. You can also call our Partner InfoSec Hotline at 1-888-WISE911 to report a non-active security incident or a security vulnerability.
October 18, 2023 Beware the Hook: Malicious Actor Phishing Email Targeting ScreenConnect Users
What We Know
Recently, our ConnectWise Information Security team has identified an increase in phishing campaigns that attempt to exploit ConnectWise ScreenConnect™ by mimicking new login alerts to deceive users into sharing their login credentials. These phishing emails are designed to appear as genuine login alerts to gain unauthorized access to legitimate ScreenConnect instances.
We know email phishing attacks continue to get more sophisticated, mirroring authentic messages and web content, so we want to ensure you are informed about this threat and know how to protect your data and privacy.
A sample of this phishing email is shown in the screenshot below and contains a “click here” link to a malicious site.
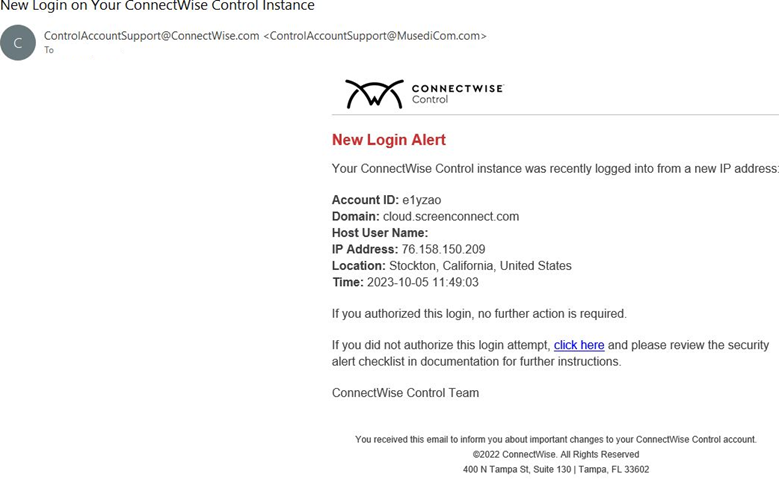
Please note, ScreenConnect does send legitimate new login alerts via email as shown in this screenshot. ConnectWise alerts do not have a “click here” link for any login notifications. If you see a link in your notification, it is not legitimate.
Our Response
With the evolving sophistication of phishing attempts on the rise, a combination of awareness and vigilance is needed. We encourage you to refresh your users with some of the standard phishing attack indicators. We also recommend staying vigilant in looking for clues to avoid mistakenly clicking on nefarious content. Before clicking, make sure content reflects:
- Email domains owned by trusted sources
- Links go to places you recognize
What Should You Do?
If you are concerned that you may have been compromised, please follow the steps in this security alert checklist. We also recommend reviewing the ScreenConnect security guide and best practices for further securing your instance, as well as verifying that links, your account ID, and your domain are accurate.
If you have questions, suspect you received a phishing attempt, or need to report a security or privacy incident, please visit our ConnectWise Trust Center. You can report both a non-active security incident, report a security vulnerability, or call our Partner InfoSec Hotline at 1-888-WISE911.
October 4, 2023 WebP/libwebp Zero-Day Vulnerabilities
*This advisory has been updated to include the impact to ConnectWise PSA.
Security researchers disclosed two vulnerabilities related to maliciously formed WebP images, which could be used to exploit browsers and the libwebp library. The libwebp library is widely used by operating systems and applications to render .WebP images.
What We Know
The vulnerability, initially tracked as CVE-2023-4863, was disclosed by Google as affecting its Chrome browser. Further investigation revealed the issue originated in the open-source libwebp library, prompting updates from multiple vendors.
A related vulnerability, CVE-2023-5129, was initially registered with a critical CVSS score of 10 but has since been withdrawn as a duplicate of CVE-2023-4863. The latter now includes the broader impact on the libwebp library.
Our Response
Our cross-functional teams immediately began comprehensive assessments of all applications and systems to identify potential risks. We also implemented enhanced monitoring to detect any suspicious activity related to this vulnerability.
Remediation
All identified products have either completed remediation or are actively undergoing it. For third-party products, we are monitoring vendor updates to apply fixes as they become available.
Remediation to date:
- ConnectWise ScreenConnect™ v23.7.8 has been released, disabling the use of libwebp
- ITBoost™, a ConnectWise solution, has been remediated and released into production
- SLI 3.0 and SLI Insights have been remediated and released into production
- Remediation efforts for ConnectWise PSA™ are ongoing. In the meantime, we recommend using the web client instead of the thick client to reduce exposure risk
- Reports and Dashboards (formerly BrightGauge™), SmileBack™, ConnectWise CPQ™, ConnectWise Automate™, Asio™ platform, and security services are not directly impacted
While we continue addressing this issue across our product suite, we recommend partners ensure their applications are up to date, regularly check for updates, and install them promptly.
If you have additional questions, please contact security@connectwise.com. To report a security or privacy incident, visit the ConnectWise Trust Center or call our Partner InfoSec Hotline at 1-888-WISE911.
April 14, 2023 <4:00pm ET> Microsoft Message Queuing Vulnerability
We have been made aware of a vulnerability affecting Windows Operating Systems running the Microsoft Message Queuing (MSMQ) service, impacting on-premise ConnectWise PSA partners. PSA cloud partners remain unaffected.
This vulnerability allows adversaries to exploit TCP port 1801 within ConnectWise PSA and execute remote code without authorization. While no immediate threat has been detected, we strongly recommend you take the following actions immediately to mitigate this vulnerability:
- Follow the steps outlined in Microsoft’s mitigations
- Update with the latest Microsoft patches
- If you are unable to update with the latest Microsoft patches, as a temporary mitigation:
- Disable the external connection for port 1801
If you have additional questions, please contact security@connectwise.com.
December 20, 2022 <6:52 PM ET>: Best Practice Reminder – Download from Trusted Sources
Researchers from ReversingLabs have identified malicious Python packages on the Python Package Index (PyPI) posing as a software development kit (SDK) from SentinelOne. The package mimics the legitimate SDK offered by SentinelOne but includes backdoor and data exfiltration features.
The full article, including the write-up and IOCs (data exfiltration IPs and package SHA1 hashes), can be found at this link. The ConnectWise Security Operations Team received the following statement from SentinelOne:
"SentinelOne is aware of the report from ReversingLabs regarding malicious packages uploaded to the PyPI (Python Package Index) repository misrepresenting themselves as SentinelOne SDK.
A malicious Python package was first uploaded to PyPI on Dec 11, 2022, and as of Dec 13, 2022, the package had been updated 20 times. The report advises that the package contains a malicious backdoor with a programmatic delay before activation. We have confirmed that our customers are safe and have not seen any evidence of compromised clients due to this incident.
Packages posing as legitimate software and leveraging the PyPI repository are becoming more common and are part of a trend toward integrating threats into software supply chains and development pipelines.
We recommend only using SDK packages provided through the SentinelOne management console.
PyPI has removed the malicious package, and we are working to investigate further."
As an industry best practice, ConnectWise recommends partners download content (SDKs, executables, installation packages, etc.) directly from the vendor to minimize risk and always verify script content prior to execution.
December 13, 2022 <11:21 PM ET>: SentinelOne/Aikido Vulnerability – Action Required
Vulnerability Type: Time-of-check Time-of-use (TOCTOU) Race Condition
Vulnerability Details
SafeBreach Labs researcher Or Yair uncovered vulnerabilities in several leading EDR and AV solutions, including SentinelOne. The issue allows a non-privileged user to create NTFS reparse points, which redirect file paths. The SentinelOne agent uses Windows functionality to retrieve file paths for mitigation. A malicious actor could exploit this to redirect the agent to a privileged file, potentially turning the agent into a data wiper.
Products Impacted
Microsoft Windows systems running SentinelOne agents prior to version 22.2.4.558 are vulnerable.
SentinelOne agents are used in the following ConnectWise products:
- ConnectWise SentinelOne Control
- ConnectWise SentinelOne Complete
- ConnectWise MDR with SentinelOne
- ConnectWise MDR Premium with SentinelOne
This exploit was also tested and found to affect Defender, Defender for Endpoint, TrendMicro Apex One, Avast Antivirus, and AVG Antivirus.
Mitigation
To be protected, install the latest SentinelOne policy override in version 22.2 SP1 (22.2.4.558) on your Windows agent endpoints. ConnectWise SOC teams have already updated all ConnectWise SentinelOne EDR and MDR consoles with this version.
After deployment, verify in the SentinelOne console if your machine requires a reboot to complete the installation.
If you have any questions about the update process, please contact our security support team at securitypartnersupport@connectwise.com.
November 29, 2022 <4:00 PM ET>: Remaining Vigilant Against Email Phishing Attempts
We are aware of a phishing campaign that mimics ConnectWise Control New Login Alert emails and has the potential to lead to unauthorized access to legitimate Control instances. Email phishing attacks continue to grow in sophistication, often mirroring legitimate email and web content.
A sample of this phishing email is shown in the screenshot below and contains a “click here” link to a malicious site. ConnectWise has issued takedown requests for the malicious site and associated domains.
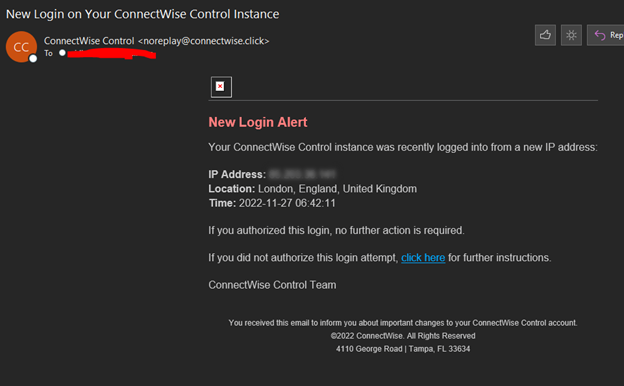
If you are concerned that you may have been compromised, please follow the steps in this security alert checklist. We also recommend reviewing the Control security guide and best practices for further securing your instance, as well as verifying that links, your account ID, and your domain are accurate.
Of note, Control does send legitimate New Login Alerts via email as shown in this screenshot. The legitimate “click here” link references the aforementioned security alert checklist that exists as a knowledge base article on our site.
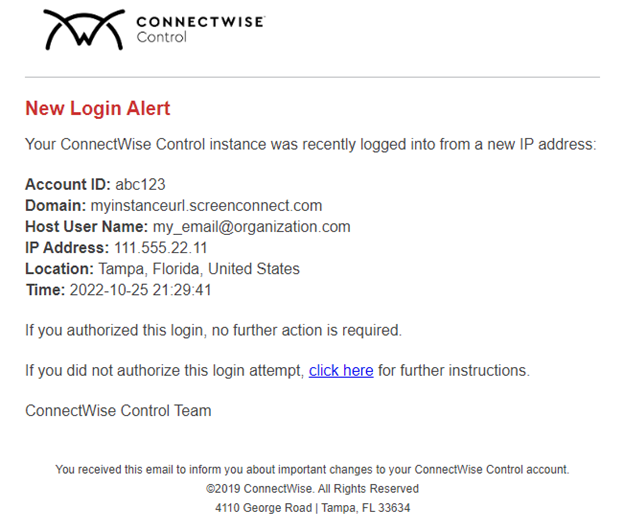
This is a more sophisticated attempt — some of the standard phishing attack indicators aren’t present, such as misplaced graphics or spelling inconsistencies. We encourage our partners to stay vigilant in looking for clues to avoid mistakenly clicking on nefarious content. Before clicking, make sure content reflects:
- Email domains owned by trusted sources
- Links that go to places you recognize
If you have questions, suspect you received a phishing attempt, or need to report a security or privacy incident, please visit our ConnectWise Trust Center. You can report both a non-active security incident, report a security vulnerability, or call our Partner InfoSec Hotline at 1-888-WISE911.
May 5, 2022 <11:00 AM ET>: Email Security Best Practices
We want to provide reminders to our partners about email security best practices.
Phishing remains a significant attack vector in many high-profile security incidents. It is imperative that organizations implement email security controls to prevent impersonation and spoofing of users and domains. SPF, DKIM, and DMARC work together to authenticate email and help ensure that the sender is who they claim to be.
SPF, DKIM, and DMARC Defined
- SPF (Sender Policy Framework) is an email validation protocol designed to detect and block email spoofing. It allows mail exchangers to verify that incoming mail from a domain comes from an IP address authorized by that domain’s administrators.
- DKIM (DomainKeys Identified Mail) uses cryptographic signatures to allow mail service providers to verify the authenticity of the sender.
- DMARC (Domain-based Message Authentication, Reporting & Conformance) aligns SPF and DKIM and allows organizations to apply policies regarding unauthorized use of email domains.
For more information on how to set up and configure SPF, DKIM, and DMARC, refer to the following resources:
- SPF: https://www.proofpoint.com/us/threat-reference/spf
- DKIM: https://www.proofpoint.com/us/threat-reference/dkim
- DMARC: https://www.proofpoint.com/us/threat-reference/dmarc
Security is a top priority at ConnectWise. Our goal is to provide robust, secure products and services to our partners. We also recognize that no technology is perfect, and we believe working with skilled security researchers and partners is crucial to identifying and resolving vulnerabilities.
If you believe you've found a security issue in our product or service, we encourage you to notify us through our Vulnerability Disclosure Program. We welcome the opportunity to work with you to resolve the issue promptly.
We are proud to be part of a community that remains equally committed to secure practices.
January 31, 2022 <8:00 PM ET>: ConnectWise Virtual Community Update
We apologize to our partners for the disruption in service last week pertaining to our virtual community. It is now online, and our product and other teams look forward to engaging with you.
Like many ConnectWise experiences (e.g., our University), our virtual community platform uses SSO to authenticate users and ensure only authorized partners engage in the community. Our SSO mechanism functioned as intended—only allowing verified ConnectWise partners to register, accept the terms and conditions, and use the platform. There was no malicious attack on our SSO capabilities.
Last week, a valued partner (via our VDP and MSPGeek community admins) raised concern about information our virtual community search was displaying to registered members. While directory search was working as intended in most cases, a configuration issue allowed non-registered partners to appear in search results. This included "first name", "last name", "company name", and in some cases, "business title". Although this information is publicly accessible (e.g., via LinkedIn), it raised understandable concern.
Only 15 registered partners conducted searches since the community launch. While we couldn’t validate the exact search results due to vendor API limitations, we confirmed that only 18 non-registered partner profiles were viewed. We remediated the issue within hours and took the site offline for a full review per our InfoSec policy. No malicious activity was discovered, no data was lost, and no data privacy actions were triggered in any jurisdiction.
What We Did
- Reconfigured the platform to consume only basic information about registered users who accept the terms of service.
- Limited default directory search fields to first and last name.
- Enabled the member directory for registered users, but default privacy settings now show only first name, last name, and profile photo (if uploaded) to non-approved contacts.
- Allowed registered members to adjust their privacy settings to control what information is shared with others.
As a courtesy, we are notifying the 18 individuals whose profiles were viewed and reaching out to the 15 partners who conducted searches to ensure the information is not used beyond community networking.
We learned that our 30-day beta testing (internal and with partners) did not expose this configuration issue. As a result, we’ve implemented additional multi-layered testing and quality control mechanisms.
Transparency benefits our community. We thank the partner who reported this and those who collaborated with us. If you have questions, please contact security@connectwise.com.



