6/13/2025 | 15 Minute Read

Maintaining a strong cybersecurity posture requires more than just applying the occasional software update.
According to research from the World Economic Forum (WEF), 72% of organizations expect cyber risks to increase in 2025, with ransomware ranking as the most pressing concern.
The aftermath of a security incident can be far more expensive than investing in preventive measures. Cleanup costs. Regulatory fines. Reputational damage. Lost contracts. Increased insurance premiums. It all adds up. In fact, the average cost of a data breach reached nearly $4.9 million in 2024.
As attacks increasingly target known vulnerabilities, two critical strategies—patch management, and vulnerability management—have become essential for reducing risk and maintaining IT security. But while these terms are often used interchangeably, they serve different, though complementary, functions.
So what’s the difference between patch management vs vulnerability management? And how can organizations effectively use both to stay secure and compliant?
In this blog, we’ll break down:
Whether you're part of an in-house IT team or a Managed Service Provider (MSP) looking to strengthen client defenses, understanding the distinction between these two processes is key to building a resilient, future-ready security strategy.
While patch management and vulnerability management are closely related—and often work together—they serve distinct purposes within an organization’s cybersecurity strategy. Understanding their differences is critical for allocating resources, selecting the right tools, and building a layered defense.
Below is a breakdown of the primary differences:
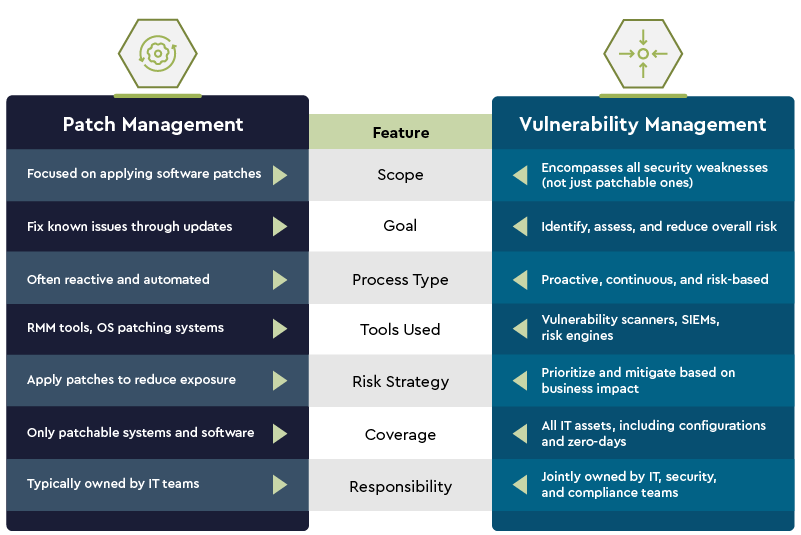
Patch management is the process of identifying, acquiring, testing, and deploying software updates—also known as patches—to fix known vulnerabilities, improve system performance, and introduce new features. These updates might come from third-party vendors (like Microsoft or Adobe) or from internal development teams, and may apply to operating systems, applications, firmware, or third-party software used across your IT environment.
The primary goal of patch management is to reduce security risks by closing gaps that could be exploited by attackers. However, effective patching also ensures system stability and compliance with industry regulations.
Patch management typically involves:
Many IT teams and MSPs use patch management software to automate patch deployment across large, distributed environments. These tools help ensure patches are applied consistently and securely, without requiring manual effort for each device.
Ultimately, vulnerability patch management helps businesses stay ahead of evolving threats, protect sensitive data, and avoid the costly aftermath of a breach. Attackers move fast, and patching faster makes all the difference. With this said, it's important to understand that it's just one part of a larger vulnerability management strategy.
Vulnerability management is a broader, continuous cybersecurity process that involves identifying, assessing, prioritizing, and remediating security weaknesses across an organization’s entire IT environment. While patching known software flaws is one part of this strategy, vulnerability management covers all potential exposures—not just those that can be fixed with a patch.
It’s a continuous lifecycle that includes:
Unlike patch management, which is often automated and task-specific, vulnerability management is strategic and risk-driven. It requires coordination between security teams, IT operations, and even compliance stakeholders to ensure the most critical vulnerabilities are addressed first.
For example, a vulnerability may be discovered for which no patch currently exists. In that case, a good vulnerability management strategy will still recommend interim actions—like disabling services, applying virtual patches, or increasing monitoring—to reduce exposure.
In short, vulnerability management provides a holistic view of your organization’s attack surface, while patch management focuses on fixing a subset of those risks with available updates.
While patch management and vulnerability management serve different functions, they are most effective when used together as part of a unified cybersecurity strategy. One is not a replacement for the other—in fact, they complement each other to reduce risk across your IT environment.
Effective vulnerability and patch management begins with visibility. You can’t fix what you don’t know exists, so the first step is identifying vulnerabilities across your environment.
Here’s how the relationship works:
Patch management is one of the key remediation actions within a larger vulnerability management program. After vulnerabilities are identified and prioritized through scanning and assessment, patching is often the first and most direct way to eliminate a known threat.
Here’s a closer breakdown of this process:
Step 1: Spot the cracks with vulnerability scanners
Everything starts with vulnerability scanners, which automatically search systems and devices for known weaknesses. They compare the organization’s environment against a constantly updated database of Common Vulnerabilities and Exposures (CVEs) and flag issues based on severity.
Scanners help build a clear inventory of what needs patching and where the biggest risks lie.
Step 2: Monitor endpoints
Endpoint agents take things a step further. Installed on individual devices, they monitor for missing patches, misconfigurations, and outdated software in real time. They provide granular visibility into the health of each endpoint and can be configured to trigger automated patch deployment, reducing manual work for IT teams.
Step 3: Watch for signs of trouble
Automated solutions can also draw information from a variety of logging systems. If a particular system is repeatedly targeted by abnormal traffic, it could indicate an unpatched vulnerability. This raises a red flag indicating that urgent attention is needed.
Step 4: Test to uncover vulnerabilities
Penetration tests simulate real-world attacks. Unlike automated scans, pen tests consider the creative tactics a real attacker might use, identifying vulnerabilities and blind spots that scanners may miss.
Step 5: Prioritize the threats
Once vulnerabilities are identified, the process continues with prioritization. The most critical risks must be addressed first and without delay. This stage is key to avoiding unnecessary downtime and ensuring business continuity.
Step 6: Test before deployment and verify
Next comes testing. Before deployment, validate patches in a staging environment to prevent compatibility issues or disruptions to core systems. After testing, deploy them using centralized patch management tools that track compliance and automate rollouts.
Finally, verification ensures that patches were installed correctly and that systems are secure.
Not all vulnerabilities can be resolved through patching:
In these cases, vulnerability management teams take alternative actions such as:
For optimal results, patch and vulnerability management efforts should:
Together, these processes ensure that:
Both vulnerability management and patch management come with distinct challenges that can delay remediation and leave systems exposed to risk.
Here’s where efforts often stall:
These challenges are not insurmountable, but they require visibility, clear processes, and the right tools to overcome. Following best practices for patch management and vulnerability testing can remove or reduce the barriers discussed above.
Many organizations struggle with effectively implementing both patch management and vulnerability management—not because of the complexity of the tools, but due to misunderstandings about what each process does (and doesn't do). Clarifying these misconceptions is crucial for developing a mature, risk-aware security program.
Here are some of the most common myths:
Patching is only one method of remediation. Vulnerability management goes far beyond applying updates—it includes identifying new threats, prioritizing based on risk, and mitigating vulnerabilities that have no available patch. Confusing the two leads to incomplete risk coverage.
While automated patch management tools are essential for scale and consistency, they can’t identify or prioritize risks on their own. Patching without vulnerability scanning means you may miss critical exposures—especially in misconfigurations, legacy systems, or non-patchable assets.
Delaying the application of critical security patches can leave your organization exposed to known, actively exploited vulnerabilities. Threat actors often exploit these flaws within days of public disclosure. A well-defined patch management policy ensures timely action aligned with business risk.
Effective vulnerability management is a cross-functional effort. While security teams may lead the process, IT operations, compliance, and even business unit leaders must collaborate to ensure:
Vulnerabilities also exist in:
Limiting patch management to OS updates leaves significant gaps in your attack surface.
By debunking these misconceptions, MSPs and IT teams can build a stronger, more integrated patch and vulnerability management strategy—one that truly protects critical systems and data.
To effectively and consistently reduce risk, organizations need a clear, scalable process that covers both the discovery of vulnerabilities and the deployment of fixes. Patch management is a critical part of this, but it must be integrated within a broader vulnerability management strategy.
Here are best practices that apply across the full vulnerability lifecycle, from identification to remediation:
By combining these best practices, organizations can strengthen both their proactive defense posture and their response capabilities, significantly reducing the risk of breaches due to unpatched vulnerabilities or mismanaged risk. For more information on setting up an effective patch management system, download our eBook, Patch Management Best Practices.
To effectively implement both patch management and vulnerability management, you need the right tools—ideally ones that can work together or integrate seamlessly within your existing IT environment. The right solutions will not only automate routine tasks but also provide visibility, prioritization, and control over your entire attack surface.
Here’s what to consider when selecting tools:
Look for tools that allow you to:
Patch management software like ConnectWise RMM, offers robust patch scheduling, policy enforcement, real-time alerts, and integrated support for Windows and third-party software updates.
Choose solutions that:
ConnectWise Risk Assessment offers a pre-sales endpoint vulnerability assessment tool that identifies security gaps, highlights dark web exposure, and equips MSPs with actionable insights to strengthen client security posture.
To reduce overhead and improve response time:
If you’re managing environments at scale—as an internal IT team or MSP—seamless integration between patch management, vulnerability assessment, and threat response ensures faster, more reliable outcomes with less manual intervention.
ConnectWise cybersecurity and data protection solutions are an enterprise ready tech stack trusted by MSPs of all sizes. From proactive vulnerability assessments and dark web monitoring with ConnectWise Risk Assessment, to automated patching and real-time compliance tracking with ConnectWise RMM, and advanced threat detection through ConnectWise SIEM and SOC services, ConnectWise delivers the tools MSPs need to protect, detect, and respond—at scale.
As cybersecurity threats become more sophisticated and frequent, organizations can no longer afford to treat patch management and vulnerability management as interchangeable—or optional. Each plays a unique and essential role in minimizing risk.
When used together, these two processes help ensure a proactive, risk-based approach to IT security that protects your infrastructure, maintains compliance, and strengthens business continuity.
ConnectWise RMM leverages automation and intelligent monitoring and alerts to deliver real-time visibility into your IT environment, making patch management more efficient and reliable while saving your techs time from manual patching. Automating patch management via RMM helps IT proactively manage potential threats and vulnerabilities across multiple endpoints at scale, helping to mitigate risks and deliver a more secure IT environment for your clients.
Put our software to the test with a free 30-day trial of ConnectWise RMM and experience firsthand how automated patch management can help elevate your IT operations.
Patch management involves applying software updates to fix known issues, while vulnerability management includes identifying, assessing, and mitigating all types of security weaknesses—whether or not a patch exists.
Both are essential. Start with a strong patch management process to address known threats quickly, but build toward a broader vulnerability management strategy for continuous risk assessment and long-term security.
No. Vulnerability scanning identifies weaknesses, while patching is one method of remediation. Scanning is part of vulnerability management; patching is a follow-up action to fix discovered flaws.
Typically, IT professionals handle patch management, while security teams oversee vulnerability management. However, effective programs require collaboration between IT, security, compliance, and leadership.
IT teams use scanners and penetration tests to assess severity and exposure. Critical issues, especially those that bad actors actively exploit, are prioritized for immediate action.
Delays increase the chance of breaches, data loss, system downtime, regulatory fines, and reputational damage. Timely patching with modern automated tools can keep all these risks at bay.