Cybersecurity compliance is a critical element in maintaining trust, ensuring data protection, and preventing your clients’ data against cyberthreats. For managed service providers, following proper cybersecurity governance is paramount to operating a successful security practice.
With the constantly evolving state of cybersecurity compliance, it can be challenging for MSPs to develop robust and consistent solutions. In this chapter, we’ll unpack the most important elements of developing a cybersecurity compliance program and the critical regulations you should be familiar with.
The importance of cybersecurity compliance for MSPs cannot be overstated. Whether you work with clients in industries that are highly-regulated or you’re looking to attract more clients in these sectors, cybersecurity regulations can be complex.
Because cybersecurity compliance management can be overwhelming for companies, MSPs have a unique opportunity to include cybersecurity compliance management as part of your cybersecurity offerings.
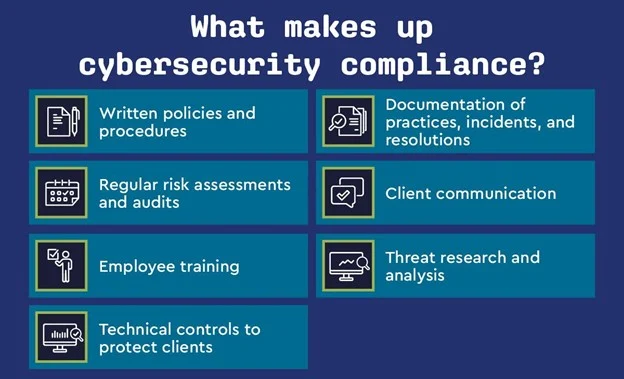
For most clients, managing cybersecurity compliance entails several key components, including:
Cybersecurity regulations play a pivotal role in shaping your organization’s daily operations. From building trust with your clients to following certain industry-specific regulations, cybersecurity compliance should be built into the foundation of your organization.
This commitment is also a commitment to business longevity, truth-building, and reputational management. Clients are far more likely to choose MSPs that demonstrate a strong commitment to cybersecurity and an ethical obligation to compliance and transparency.
However, when an organization adheres to a strict compliance regimen, it can pose certain challenges for MSPs. Because each sector and industry often has unique—and complicated—regulatory requirements, MSPs must stay abreast of trends, rules, and regulations to effectively serve clients.
Additionally, cybersecurity compliance is an inherently complicated topic and often comes with a proliferation of extra paperwork, documentation, and reporting. When supporting your clients with cybersecurity compliance, be aware of the additional energy and time that may be required for success.
Non-compliance with cybersecurity standards can result in grave consequences for your company and your clients. The implications range from legal penalties and loss of business reputation to much more serious consequences.
Common consequences for non-compliance with security standards include:
Because of the growing increase in conversation about cybersecurity and its importance to businesses, news stories about non-compliance tend to gain traction in the news cycle. Some of the most common examples of non-compliance consequences include:
Beyond the financial and reputation repercussions of non-compliance with cybersecurity standards, MSPs have a legal and ethical obligation to be compliant. Staying compliant with cybersecurity standards ensures that your MSP is operating within the bounds of the law—which reduces the risk of unexpected legal challenges or financial losses.
In today’s digital world, understanding cybersecurity regulations and standards plays a crucial role in protecting your clients’ data privacy and protection. As your client’s trusted caretaker of their IT infrastructure and data, being well-versed and effective with these regulations is key.
Common cybersecurity regulations and standards include:
In addition to these more common cybersecurity standards, there are different industry-specific requirements for MSPs to become acquainted with:
Region-specific protections are also important for MSPs to understand:
While cybersecurity is a global effort, each region has specific and tailored cybersecurity strategies to protect businesses and develop a safer, more secure digital world. When approaching each cybersecurity challenge, understanding the country-level nuance will provide great clarity and insight.
With a deeper understanding of the importance of cybersecurity compliance for your clients, you’re ready to create a cybersecurity compliance program for your organization. Doing so will help ensure alignment with regulatory requirements, protect sensitive information, and foster trust with your clients and stakeholders.
The most common components of a cybersecurity compliance program include:
As you begin to implement a cybersecurity compliance program, embrace a strategic step-by-step process. Start by identifying the right team member to form a compliance team. While you don’t need an entire department dedicated to compliance activities, it is optimal to leverage the expertise of an information security analyst responsible for tracking compliance requirements.
With the ever-evolving cybersecurity landscape, knowing where to start when building a cybersecurity program can be difficult. Gain the foundational knowledge you need to build resilient cybersecurity offerings in our recent eBook, The Ultimate Operations Guide for MSP Cybersecurity.
Cybersecurity compliance is a cornerstone of trust with your clients—and one that requires a continuous dedication to improving daily processes and bolstering client satisfaction. Consider the following steps to improve your organizational cybersecurity governance.

One of the most effective opportunities to boost cybersecurity compliance is to map requirements to your offered services. By systematically addressing compliance requirements within your service portfolio, you can provide robust cybersecurity while demonstrating your commitment to compliance.
Begin by identifying which regulations are most applicable to your current clients. For example, if you primarily serve healthcare clients, HIPAA is your priority. On the other hand, those in the financial sector might focus on GLBA or PCI DSS.
For each identified regulation, map out how your unique service offerings align. For example, because HIPAA mandates the encryption of data at rest, then your data storage and backup services must inherently include encryption features.
Next, evaluate your service offerings against each regulatory requirement. If gaps are found, consider adjusting your services or incorporating new ones to meet your clients’ needs. Here are some key service offerings that are foundations of any compliance program:

Lastly, maintain clear and organized documentation that details how each service adheres to specific regulatory requirements.
Data privacy and protection have become focal points in the digital age, driven by an increasingly interconnected world and the rise of cyberthreats. One single breach of data can irreparably damage a company’s public image, leading to lost trust and lost revenue.
With regulations like GDPR, CCPA, and HIPAA, data privacy is not just a best practice—it’s a legal obligation. When serving your clients, consider the following best practices and solutions for protecting data:
In addition, following data breach notification requirements is key. Stay informed about any specific data breach notification requirements in the jurisdictions where your clients operate. Requirements vary widely—from the definition of a breach to the timeline and method of the notification.
Third-party vendors and service providers often play a supportive role in the operational efficiency of your business. However, these providers can also introduce potential vulnerabilities in your organization’s infrastructure—posing risks to your company as well as your clients.
Managing third-party compliance should be an indispensable component of your overarching cybersecurity strategy. Any vulnerability introduced by a third-party can lead to breaches that impact multiple clients, multiplying potential damage.
Plus, if you’re leveraging third-party tools and solutions into your service stack, the complexity of the IT environment increases. This has the potential to introduce new vulnerabilities or compliance patch management.
When hiring third-party vendors, make sure to incorporate the following steps:
Many compliance regulations hold companies accountable for breaches—even if the source was a third-party vendor. Failure to ensure third-party compliance can result in hefty fines and reputational damage.
While third-party compliance management is essential, your internal compliance framework is equally crucial. Monitoring, reporting, and regular audits are necessary for your organization.
Because cybersecurity is an inherently complex topic, regular training and education with your team is the cornerstone of a resilient defense. While tools and technologies are helpful, the team members who operate these tools are just as critical.
Provide regular training sessions focusing on the importance of cybersecurity compliance, the reasons behind certain regulations, and the implications of non-compliance. By contextualizing the day-to-day operations of upholding cybersecurity compliance, team members will feel empowered and confident in their ability to play a role in securing clients’ confidential data.
Cybersecurity is a consistently evolving field—and as it continues to shift, new threats, technologies, and best practices will become available. To best protect businesses, regulations will also evolve in tandem.
As an organization, staying ahead of these evolving regulations ensures business longevity and upholds trust with your clients. To achieve this, consider the following actions:
For more resources to help MSPs stay on top of these changes, this blog is a great starting point to learn about the main regulations to focus on for your business. To take this step even further, our Cyber Research Unit helps identify new vulnerabilities and threats to help make sure you’re always at the forefront of areas like data privacy and protection.
In addition, as AI becomes commonplace with many organizations and industries, new cybersecurity regulations will likely follow suit. From AI-powered threats and data privacy concerns, to bias and decision-making, expect AI security to warrant new regulations and policies to protect users and businesses.
Compliance in cybersecurity is far more than just a quick checklist to follow. Instead, it’s an integral and transformative component that shapes the ethos of your company. Mastering the cybersecurity compliance process not only safeguards your company’s reputation but it fortifies client trust.
Many modern cybersecurity solutions empower MSPs while developing a cybersecurity compliance practice:
Cybersecurity tools also empower teams with a scalable solution—so as your client base grows or as services expand, compliance standards remain consistent. For MSPs, this means less time spent grappling with compliance challenges and more time spent delivering outstanding service for clients.
At ConnectWise, we understand that navigating the nuance of cybersecurity solutions can be overwhelming and complicated. That’s why our comprehensive cybersecurity suite offers MSPs a number of critical tools to streamline daily tasks, streamline compliance reporting, and offer real-time monitoring and alerts.
Watch a demo of our cybersecurity suite today or learn about our Cybersecurity Research Unit (CRU) for up-to-date threat intelligence and cybersecurity resources for MSPs.
Knowing which cybersecurity regulations apply to your business is dependent on your industry and sector. Healthcare businesses, for example, must follow regulations such as HIPAA, mandating the protection of patient health information. On the other hand, financial institutions must comply with different regulations, such as the Gramm-Leach-Bliley Act or the PCI DSS. Partnering with a cybersecurity expert with experience in your specific industry is the quickest way to gain a clear sense of what cybersecurity regulations apply to your needs.
Non-compliance with cybersecurity regulations can have a broad spectrum of consequences. The severity of these penalties and risks depends on several contributing factors and can include fixed or tiered penalties, daily penalties, cease and desist orders, loss of licensing and certification, loss of trust and negative press, or loss of clients or reputation damage.
Training employees on compliance best practices is crucial for ensuring that regulations and standards are consistently upheld. Implement a structured and comprehensive training program by developing a curriculum that covers general compliance principles, role-specific training, and updates as regulations evolve.
With the dynamic nature of cybersecurity, regulations change quickly. To stay up to date with compliance standards, subscribe to regulatory newsletters and alerts, join professional associations, attend workshops and seminars, invest in compliance management software, and regularly consult with your legal counsel.
Leveraging automation can significantly reduce manual effort, minimize human errors, and maintain consistency. Many compliance management platforms help by consolidating compliance data in one place, making it easier for team members to manage, monitor, and report. Automated data collection and reporting is also a helpful way to automate daily processes.