What is a cybersecurity risk assessment?
A cybersecurity risk assessment refers to the process of identifying, estimating, and prioritizing information security risks. These assessments cover everything from policies, processes, employee training, and technologies used to protect an organization’s users and data. Cybersecurity risk assessments often leverage third-party cybersecurity frameworks, compliance, or regulatory standards to compare an organization's security controls and posture against time-tested industry standards and best practices.
A complete cybersecurity risk assessment should evaluate an organization’s IT infrastructure as well as its security-related policies and procedures. For example, this might include:
- Existing cybersecurity mechanisms
- Compliance with industry regulations
- Total value of the company’s digital assets
- Descriptions of potential threats
Ultimately, a cybersecurity risk assessment is a launching point that helps an organization better understand the current state of their cybersecurity efforts while identifying areas for improvement. These areas can be prioritized based on how they align to the organization’s business objectives; whether they need to be addressed as soon as possible, in the near future, or somewhere down the line (i.e., replacing a tool that gets the job done but could be upgraded with new features).
Cybersecurity risk assessments involve three essential elements: a network assessment, a security assessment, and a vulnerability assessment.
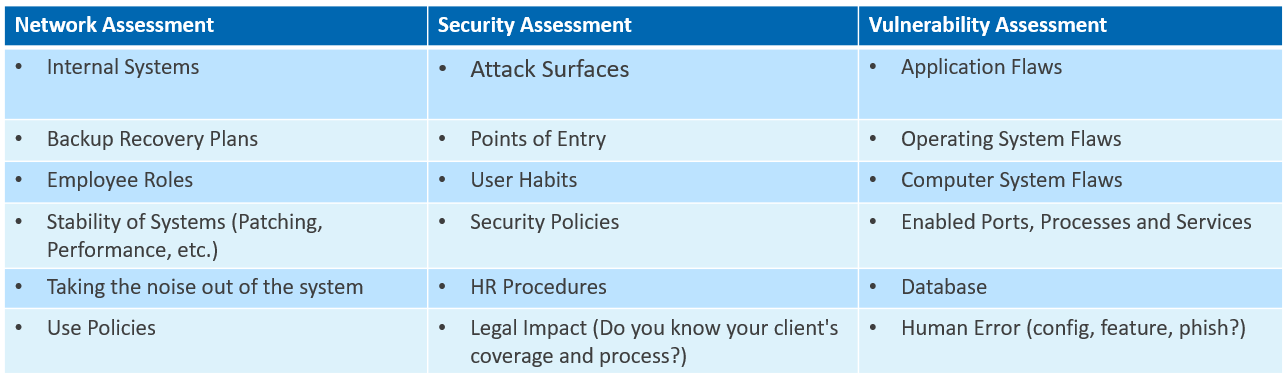
Network assessments
A network assessment refers to the process of evaluating an organization’s networks and internal systems to identify opportunities for improvement and reducing risk. Today, top MSPs are using automated network assessment tools to save time and win more business. For example, such a tool can be used to identify unknown devices on a given network such as unmanaged/hidden switches, private access points, and unauthorized wireless devices.
In addition to finding ways to increase system stability, organizations should also use this as an opportunity to develop a recovery plan to restore and return any compromised hosts, applications, or networks back to normal operations. This includes defining actions needed to rebuild infected systems, replace compromised files, reset passwords, patch systems, and secure network perimeters.
Security assessments
While network assessments involve diagnosing issues that are degrading network performance and causing downtime, security assessments focus more specifically on identifying potential points of entry for threat actors and reducing an organization's overall exposure to cyber risk. A security assessment helps an organization understand whether or not they have the proper security mechanisms in place to protect their services and ensure that their attack surfaces are minimized. Ultimately, a security assessment will result in a plan of action and milestones (POAM), a documented plan that indicates the specific measures an organization will take to correct the deficiencies found during the assessment.
Vulnerability assessments
Once an organization has a good idea of their current security posture, they can focus on assessing vulnerability more explicitly. Vulnerability assessments often leverage automated tools to identify application and operating system issues such as problems with injection, cross-site scripting, outdated libraries, broken authentication, exposed data, and more. To be clear, vulnerabilities encompass more than simple system and application patching – they include flaws in design (hardware, software, and architecture), coding (operating systems, applications, firmware), and process (missed steps, insecure procedures).
Many vulnerability assessments also include penetration testing, a series of white hat hacking attempts designed to help reveal an organization’s vulnerabilities before an actual threat actor can exploit them. All identified vulnerabilities should be fixed as soon as possible or surrounded with mitigating controls.
The MSP role in cybersecurity risk assessments
As more SMBs recognize the need to assess their overall cybersecurity posture and identify opportunities to reduce risk, there are several ways that MSPs can earn trust and increase business.
Provide cybersecurity education
In order to have fruitful conversations about cybersecurity, it’s essential for MSPs and their clients to speak the same language. That’s why MSPs should consider educating and training clients on topics such as data breaches, malware, phishing, and more. This allows clients to better understand the results of a cybersecurity risk assessment, plus an engaged client is more likely to add security services onto their existing contract.
Small and midsize businesses (SMBs) especially have a need in this area: The State of SMB Cybersecurity in 2021 survey conducted by Vanson Bourne and commissioned by ConnectWise found that 43% of SMB do not implement any form of cybersecurity awareness or training, down only slightly from 45% in 2020.
Risk assessments
By offering strategic risk assessments, MSPs can establish themselves as trusted cybersecurity advisors, ultimately resulting in opportunities to recommend products/services that can be used to fill gaps in clients’ cybersecurity posture. For example, a comprehensive risk assessment tool can leverage the NIST CSF to provide actionable recommendations that MSPs can use to identify, detect, and respond to security risks within clients’ businesses. In-depth risk assessments cover:
- Network vulnerabilities
- Insufficient device management
- Data compliance issues
- Internal threats
- Potential impact of an incident
- And more
Finally, risk assessments should include a list of remediation recommendations so clients know exactly what they have to do to strengthen their cybersecurity posture.
Dark web risk assessments
A specific category of risk assessment, dark web risk assessments help MSPs alert their clients to leaked or compromised data by searching hidden databases and internet pages for sensitive information related to their organization. This might include:
- Usernames and passwords
- Answers to security questions
- Customer, operational, and/or financial data
- Personally identifiable information (PII)
- Intellectual property or trade secrets
To streamline the process of dark web scanning and presenting the findings to clients, many MSPs prefer to use a vulnerability scanner tool capable of producing easy-to-digest reports. This enables clients to easily understand what they need to do and why it’s important.




