See the ConnectWise difference for your cyber and data needs
Consolidate your security stack to cut costs and complexity
Get insights from the only cyber research team dedicated to MSPs
Choose the team that not only reports incidents, but provides incident response
Resources to market, sell, and support your cyber and data protection offering
Access 24/7 monitoring and response from 200+ security experts and analysts
Check the boxes for your MSP to qualify for cybersecurity insurance
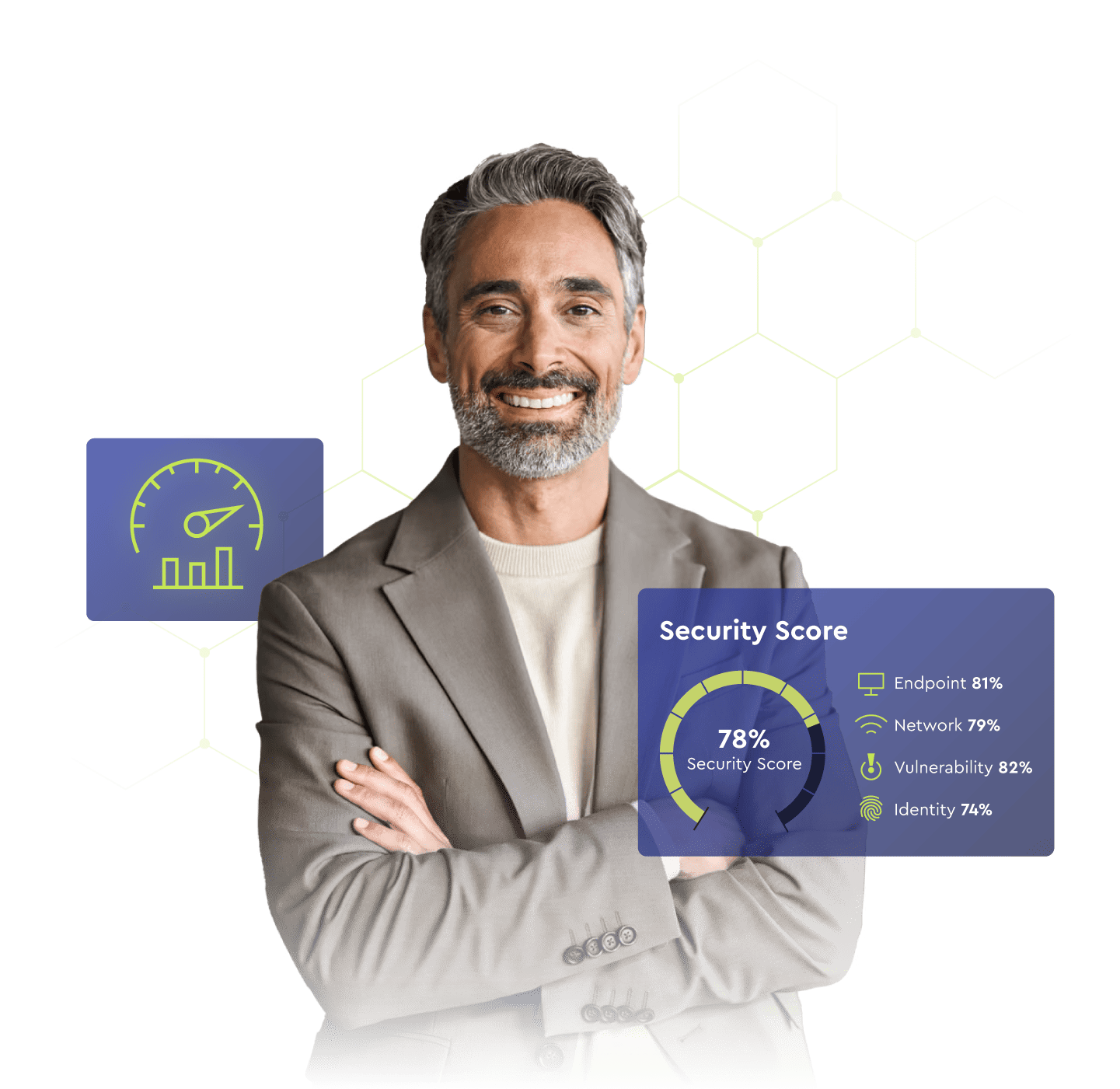
Visibility across all of the cyber solutions you use, ConnectWise or not
Give your clients what they need to qualify for cybersecurity insurance
Now is the time to act when it comes to cyber
You are the frontline for cyber attacks
Your clients are the first and primary targets of cyberattacks. Especially phishing and stolen credential attacks. Your clients need to know they’re safe.
Cyber insurance is top of mind
Cybersecurity insurance providers are converging on a long list of requirements to qualify and pay out in the event of an incident. We help meet these requirements.
Expensive and complex offerings
We can help you keep up with trends, know which products and services to offer, sell and price your packages, and recruit and retain security talent.
Consolidate your stack and increase revenue with ConnectWise Cybersecurity and Data Protection solutions
Advanced cybersecurity and data protection are a necessity for all businesses. But most SMBs can’t manage this in-house, and many MSPs still haven’t figured out how to meet the demand. This is your opportunity to differentiate and scale.
Say goodbye to scattered security solutions and hello to a powerful portfolio of cybersecurity products that will take your business to new heights. Our lineup includes everything you need to keep your clients’ data safe and profits growing. Consolidate your stack and let our cybersecurity solutions supercharge your business!