3/8/2023 | 9 Minute Read
Topics:

Tom Brady. Serena Williams. Tiger Woods. Simone Biles. Christiano Ronaldo. LeBron James. All championship winners in their specific fields, but how did these titans of sport come to dominate their fields? Practice.
Just like a sports team, your cybersecurity team won’t reach its full potential without regular practice. But rather than hitting the gym, cybersecurity teams work out using red team vs. blue team cybersecurity drills.
So how do these drills work? What can managed service providers (MSPs) gain from regularly running red vs. blue exercises?
A healthy practice schedule is vital to the success of your clients’ cybersecurity protection, so read on to learn how to put your security infrastructure to the test.
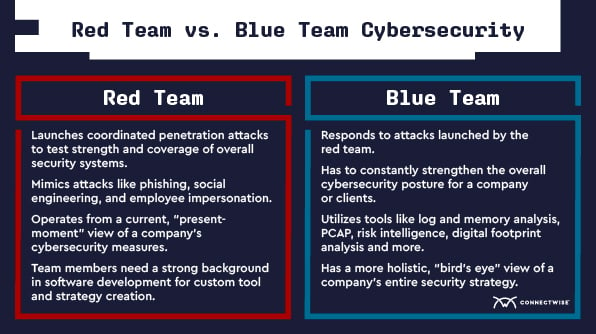
Keeping with the sports analogy, the red team acts as an opposing team’s practice squad. Red teams include ethical hackers, system administrators, and forensic experts who use penetration testing (or “pentesting”) to test the target system’s resilience and look for any potential vulnerabilities malicious attackers could exploit.
The purpose of the red team’s cybersecurity exercises is to test and challenge existing security protocols from an attacker’s point of view.
During an exercise, an IT professional will assume the role of threat actors to see what loopholes or vulnerabilities could pose a major threat by being exploited during a real-world attack. The goal here is not to hold anything back. Successful red team vs. blue team operations require the “practice attacks” to mimic real-world attacks as closely as possible.
With this in mind, many organizations use external actors instead of internal teams to test their systems when conducting red team vs. blue team cybersecurity drills. Bringing in external actors allows organizations to test their systems with fresh eyes and unbiased opinions.
Red team members should be able to:
Here are a few of the main attack types red team members will employ when testing systems:
Red teams play an integral role in testing the functionality of your clients’ cybersecurity strategy. These exercises provide invaluable data and insights into a system’s effectiveness and are crucial to identifying a system’s vulnerabilities.
If we think of the red team as the attackers in these simulated drills, think of the blue team as the defenders. The blue team is the internal security staff that works to detect, defend, and respond to attacks as they come up.
Blue teams are generally composed of IT professionals, network engineers, and cybersecurity experts tasked with running the cybersecurity infrastructure of the organization. Their job is to ensure the network and systems are secure against malicious activities and threat actors.
The blue team is responsible for reinforcing the cybersecurity posture of their clients on a regular basis. Not only must they be vigilant against attacks from the red team, but they also need to remain alert and aware of any unusual or suspicious activity.
Since members of the blue team are approaching cybersecurity from the defensive perspective, effective blue team members should be able to:
Although both blue and red cybersecurity teams possess their own skills and do their own jobs, cybersecurity is most effective when they work together.
Blue team cybersecurity squads will employ one or more of the following tools:
Running regular red team vs. blue team exercises offers a variety of advantages to your cybersecurity posture. They can help you:
Proper blue team cybersecurity helps MSPs gain a holistic cybersecurity perspective. Seeing what loopholes and vulnerabilities your red team can exploit is just one piece of the puzzle. Threat detection and threat response are just as important—if not more important—and blue team cybersecurity measures help strengthen your clients’ systems to that end.
Want to see how these and other tools can boost your cybersecurity efforts? Check out our cybersecurity center for more information.
Red team vs. blue team cybersecurity exercises should be a routine component of your security posture. Cybersecurity attacks and threats can go undetected if not tested for, and research shows that the average dwell time for threat actors reached 21 days in 2022. This means that, without red team vs. blue team cybersecurity drills, your clients’ network infrastructure or sensitive customer data is vulnerable to attack.
As the threat landscape has evolved, so has the need for different kinds of cybersecurity teams. To combine these various responsibilities into a single team, the concept of the “cybersecurity color wheel” was born. The goal of the cybersecurity color wheel is to create an integrated security team that goes beyond red and blue team capabilities.
Here are the four additional teams that comprise a full cybersecurity color wheel:
Red team vs. blue team cybersecurity drills are essential for improving an organization’s security posture. By putting your organization’s security infrastructure to the test, you can find and fix vulnerabilities before they pose a threat.
As an MSP, it’s important to understand the roles and responsibilities of each team in a cybersecurity-colored wheel, as well as when you should be running red team vs. blue team exercises. With the right approach, you can keep your organization well-protected and ready to respond quickly and effectively in the face of any kind of attack.
Equally as important as building effective teams is making sure they have the tools they need to test and address cyber vulnerabilities. Request a live demo of our cybersecurity solutions to see how the ConnectWise cybersecurity suite can help evolve your cybersecurity offerings.
The red team’s goal is to expose any potential vulnerabilities or loopholes in an organization’s cybersecurity by thinking like a threat actor. They do this by launching ethical cyberattacks that mimic those seen in the real world in an effort to boost the organization’s cybersecurity.
The blue team’s goal is to secure and strengthen an organization’s cybersecurity defenses. They are responsible for responding to the threats launched by the red team, constantly monitoring long-term cybersecurity protocols, and improving overall threat response.