8/4/2023 | 9 Minute Read
Topics:

Security is crucial for organizational performance, and engineering teams are responsible for ensuring it. One of the most challenging obstacles is that many engineering teams leave this duty to a few knowledgeable engineers, who must work through prioritization concerns with product and leadership to get things done. Organizations must prioritize secure development processes, beginning with software engineering, cloud engineering, and security organization. In this blog, we focus on how to create a secure development process and security mindset in engineering teams.
A secure development approach is necessary for companies with diverse product offerings, whether through internal development or acquisitions. Scaling security requires a systematic process rather than relying solely on individual skills. While investing in security may involve trade-offs, such as diverting resources from other areas, the long-term benefits outweigh the short-term sacrifices. Prioritizing security safeguards company integrity and instills customer and stakeholder confidence.
The following sections will go through practices that embed security into requirements, design, coding, testing, and maintenance, as well as some recommended security tools that could expedite the journey.
Organizational security is a concern. Good security is achieved by a well-defined process and culture. The process laid out should be extremely centralized rather than distributed.
Security necessitates specialized knowledge and it’s unrealistic to expect all engineers to become experts in this field. All engineers, however, will develop code. Therefore the process is ultimately what enforces security. To achieve this, there are three main areas you should invest in:
1. Identify or hire a leader to drive security early on
A security leader is a proficient individual who can oversee security operations throughout the engineering department and ensure everyone abides by the protocols established by the organization's CISO. They should be able to:
2. Train employees in security
Security training is key to helping all employees. Open-source and high-level courses are available that cater to both broad and specialized audiences.
There are many ways you can go about encouraging cybersecurity training, including these two methods:
3. Integrate security into the development process
The only way to write secure code is to incorporate security into every stage of the development process. Specs frequently change during development, resulting in inconsistent or inadequate evaluations.
A secure Software Development Life Cycle assists in integrating security checks as early in the SDLC as possible and is divided into five main stages:
Let’s see how you can embed security in each of them.
Product specifications are the starting point for security concerns. Team members like product managers and designers must understand how information flows and what may and cannot occur.
This extends to fundamental aspects, such as ensuring that users can only access their own client information, maintaining privacy and confidentiality.
Moreover, an increased emphasis on compliance requirements in product engineering is necessary, particularly when introducing products to diverse geographical regions.
To increase the presence of cybersecurity in the design phase, it's essential to use a design doc.
The design doc template includes a section about security requirements for the application developed. The sections must cover functional and security requirements. Functional requirements are about what should happen, while security requirements are about what shouldn't.
Here's an example:
When in doubt, escalate to a security leader in your organization for assistance. For large-scale designs, a key part of the design doc is its threat model.
A threat model is a systematic and structured technique used to identify an application's security objectives, threats, and vulnerabilities. This helps to make design and engineering decisions, and determine where to prioritize efforts in designing, developing, and deploying secure applications.
Threat modeling is a series of events to:
You can check the dedicated OWASP page for more details about how to go about it with practical examples. A sample threat tree from OWASP is shown below:

Figure 1: Sample threat tree from OWASP
This is where you make sure the code is well-written from a security perspective. Here are some tactics you can use:
Use a code checklist
When it comes to coding, it's essential to follow common security advice to safeguard your work and protect sensitive information. With tools like CoPilot and AI assisting in code generation, it's crucial to educate your development teams on best practices. Emphasize the importance of not posting any company-related questions or datasets in public domains to avoid potential security breaches. Additionally, ensure that the code generated is thoroughly tested and undergoes the usual testing iterations to maintain its integrity and reliability. Write down a list of the most common security advice you may need while coding. This is useful in many ways, including as a:
Some examples of items that may go into the checklist are:
OWASP has useful guidelines if you'd like more resources to reference.
Use a linter
Linters can intercept basic issues while you are writing code. All popular linters, such as pyLint and ESLint, have security plugins you can use to identify potential issues like unsanitized assignments, XSS, and dubious regular expressions.
You can also connect external tools, such as Sonar, to linter to perform lightweight SAST while you are coding.
Perform static application security testing (SAST)
Static security testing is about intercepting insecure programming patterns. SAST tools analyze the source code and scan for vulnerabilities automatically. Your team should run these tests in your CI/CD pipeline as a mandatory step.
A few of the most popular SAST tools are:
Perform software composition analysis (SCA)
If SAST is used to double-check your code for vulnerabilities, SCA is used to do the same for all of your dependencies.
This is essential given that the vast majority of cloud-based code is open-source. Dependabot is probably the most popular tool to do this, because you can use it natively in GitHub. Also consider that most SAST tools are capable of doing SCA, so you can find plenty of comparisons online such as Dependabot vs Snyk scanning.
Run dynamic application security testing (DAST)
DAST refers to security testing performed on a running application, not a static code. The goal of dynamic application security testing is to find and list security vulnerabilities and misconfiguration. It is a form of black-box testing because it checks your application from the outside, only relying on inputs and outputs, and is agnostic of programming languages and technical implementations.
DAST complements SAST and SCA well by scanning for problems that are outside of the others and vice versa. However, it requires more effort.
It is difficult to automate—it can be added to your CI/CD pipeline, but it is on the far right because the application must be running. It requires manual implementation and maintenance, as opposed to SAST and SCA which occur automatically.
Some of the most recommended DAST tools include Brightsec, Stackhawk, and Invincti.
After your code is in production, there are several other practices that can further help with cybersecurity. This includes:
Implementing good observability
Modern observability tools can help detect breaches and various kinds of attacks. AWS Inspector, Dynatrace, and Datadog are some tools that engineers can use for both security and system monitoring.
Running periodic security sprints and penetration tests
There could be a constant struggle to find time to address security issues. Hence, consider running periodic sprints dedicated to security. You can use them to fix problems in your backlog or to go through controls in a security standard. Keeping the security backlog clean helps engineers to focus on more productive work. Penetration tests must also be run periodically and must be executed by independent entities.
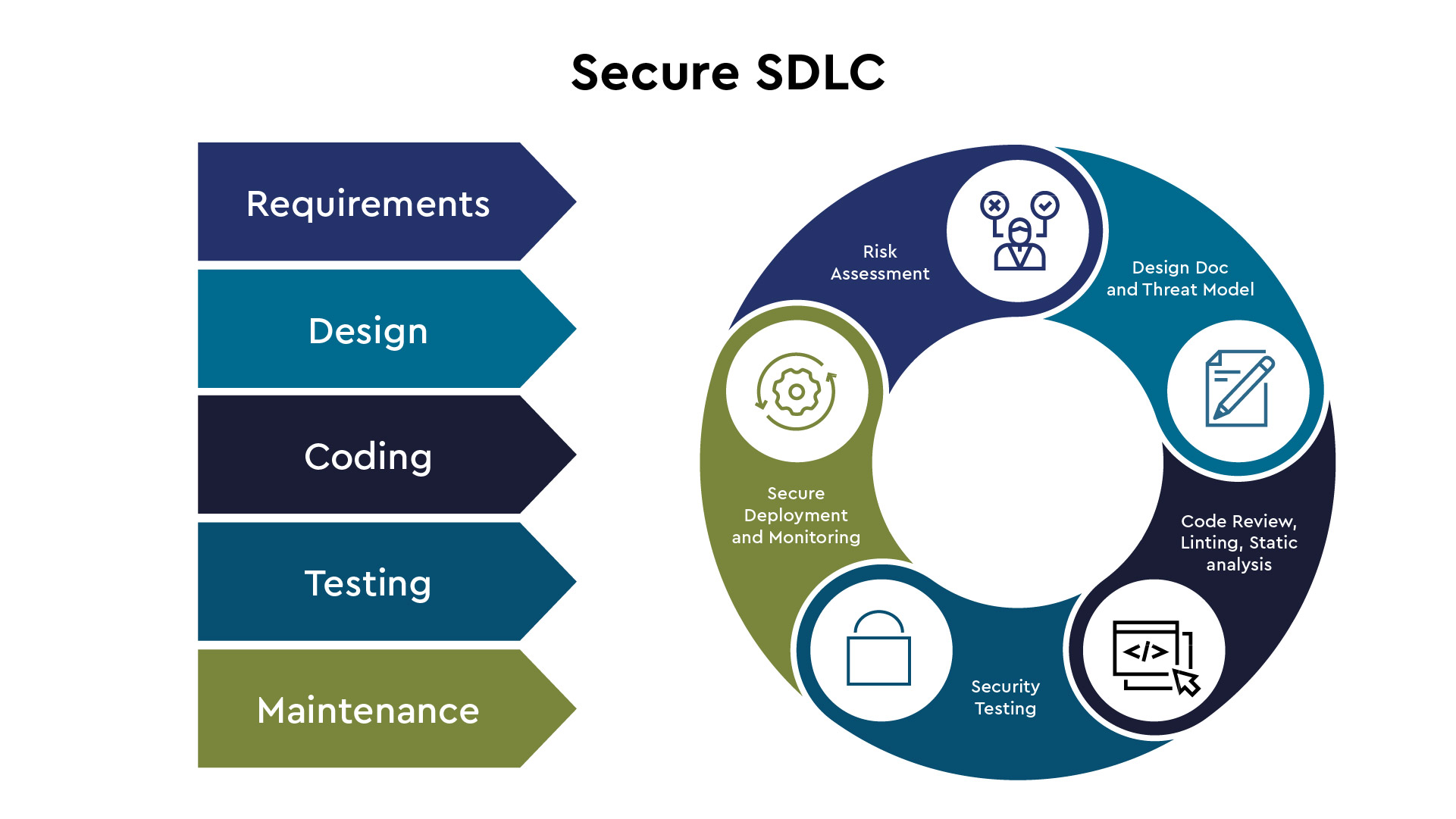
Figure 2: Secure SDLC Chart
At ConnectWise, we place the highest importance on security. The ConnectWise Asio™ Platform is a scalable and secure platform designed to help enhance security efforts. The platform approach toward security enables us to centralize security efforts, establish a well-orchestrated cybersecurity posture, and deliver protection for our partners and their end users.
We train our engineering personnel to follow security best practices. We constantly educate engineers on the importance of shift left mindset with the platform approach. Regularly, our engineering teams and leadership are provided resources and educational material by OWASP, CompTIA, external trainings, and internal security teams. The architecture review board subjects any new product or significant feature updates to a rigorous examination, carefully scrutinizing the threat model and security plans. The reviews ensure the system’s confidentiality, integrity, and availability by implementing proper security measures and practices. This is further incorporated in our products through a unified product release cycle.
However, like any other organization, we are not immune to threats. If a security event occurs, engineering teams ensure adherence to all protocols established by InfoSec. Post-mortem analysis of a security event is of utmost importance to us, and we involve all relevant stakeholders in updating and refining our engineering practices. This could involve superior automation, code, and checklists to comply with industry best practices.
The empowerment of our engineering teams, coupled with a strong security culture, is vital to the delivery of secure products and updates to our partners.