9/21/2022 | 5 Minute Read
Topics:

The “Configure Microsoft Office Macro Settings” component of the Australian Cyber Security Centre (ACSC) Essential Eight is focused on hardening the Microsoft Office macro environment. This is achieved by controlling the location where macros can be run and ensuring they are trusted, so as to significantly minimise risk. To do this, we need to understand if macros are truly a business requirement and how to best manage the requirement without overly impacting the user.
Users of Microsoft Office applications will have macros or “program code” that they have been provided with by an internal or external source. Alternatively, they may have written the macro themselves. Typically, the aim of the macro is to automate regular tasks and processes, resulting in significant productivity gains. However, they can also be misused in a manner that can result in unauthorised access to sensitive information or even a ransomware event.
Unlike other controls, hardening of Office macro security will not have a major impact on all users. However, there may be some areas where it can cause a major challenge. Interestingly, these can often be in critical parts of the organisation such as finance, which also makes them more important to secure. To be clear, maintaining security here is not about preventing them from using macros if needed—it is about ensuring that they only run verified macros from trusted sources.
Users may insist that there is no reason to only run macros from a curated trusted source. However, many incidents are caused by adversaries manipulating users into running malicious macros. Thus, it is essential to control it.
We covered the broader context of the Essential Eight at the start of this series. In summary, the ACSC Essential Eight is a prioritised set of eight “essential” mitigation strategies or controls for building cyber resilience and protection from cyberattacks.
Please remember that while the Essential Eight establishes a fundamental set of mitigation measures, it is likely that an organisation may require additional mitigation strategies. More information can be found in the ACSC Strategies to Mitigate Cyber Security Incidents framework and the ACSC Information Security Manual (ISM).
When securing office macros, we are defining which macros are going to be trusted. While this can be performed by defining the trusted documents feature, it is a better practice to use trusted locations, as this provides greater flexibility in balancing business and security requirements.
When implementing management of trusted macros, a key element is how you decide which macros to trust and place into the trusted location.
We can start by simply preventing macros from untrusted sources (such as the internet) and preventing users from changing macro settings (this stops users from being manipulated into running malicious macros). Beyond this initial set of controls, these are the next steps we should take:
The key to this implementation being successful is ensuring that only authorised representatives can place the approved macros in the trusted location for use by approved users.
As always when considering which maturity level to target and controls to implement, we need to consider the impact within the customer environment.
The following table summarises not only the business impact and implementation difficulty, but also the security benefit of each control.
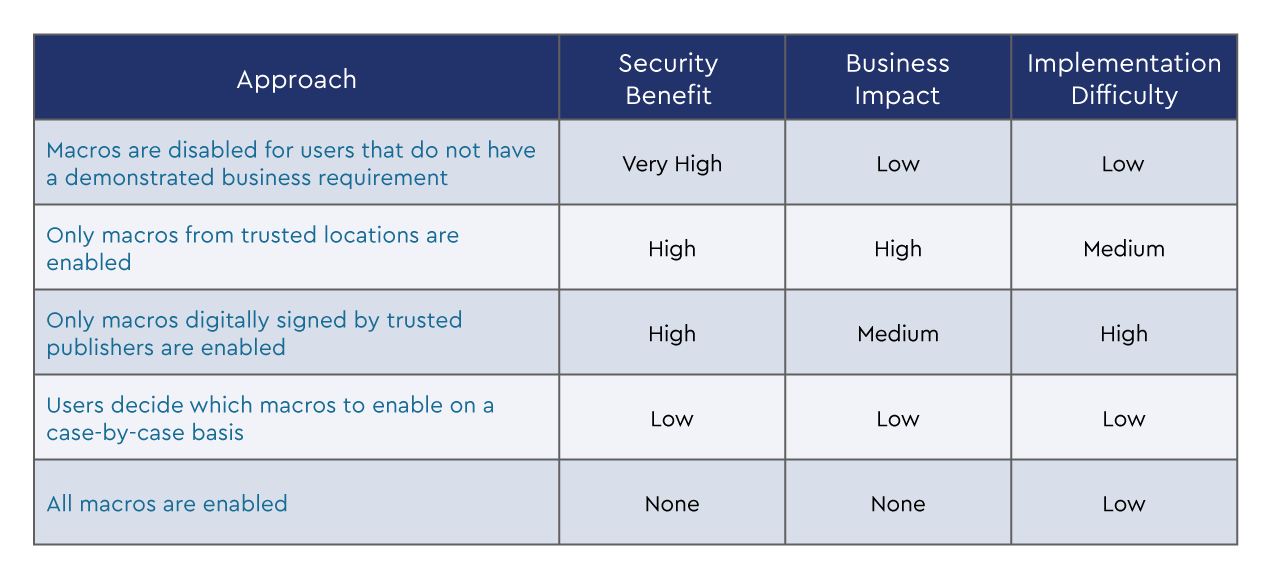
More details on these strategies including specific group policy settings for specific Microsoft Office applications can be found on the ACSC site at Microsoft Office Macro Security.
As you plan to implement the Essential Eight within an organisation, you will need to determine which level of maturity should be targeted. To assist with this identification, the ACSC has defined indicative risk profiles for each maturity level.
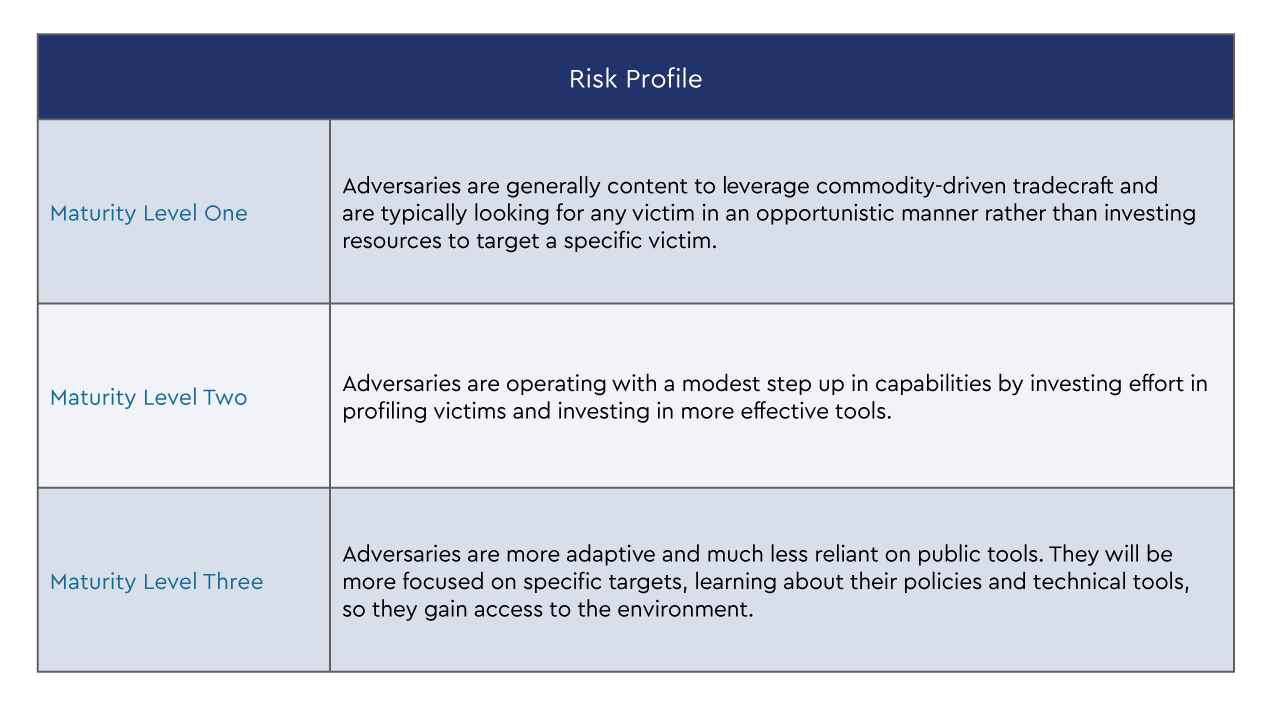
As you design your implementation strategy, keep in mind that you will need to ramp up each of the “Eight” before progressing to subsequent maturity levels. With “configure Microsoft Office macro settings,” this is particularly noticeable as each level builds on the previous one.
The strategies below are taken directly from Essential Eight Maturity Model.
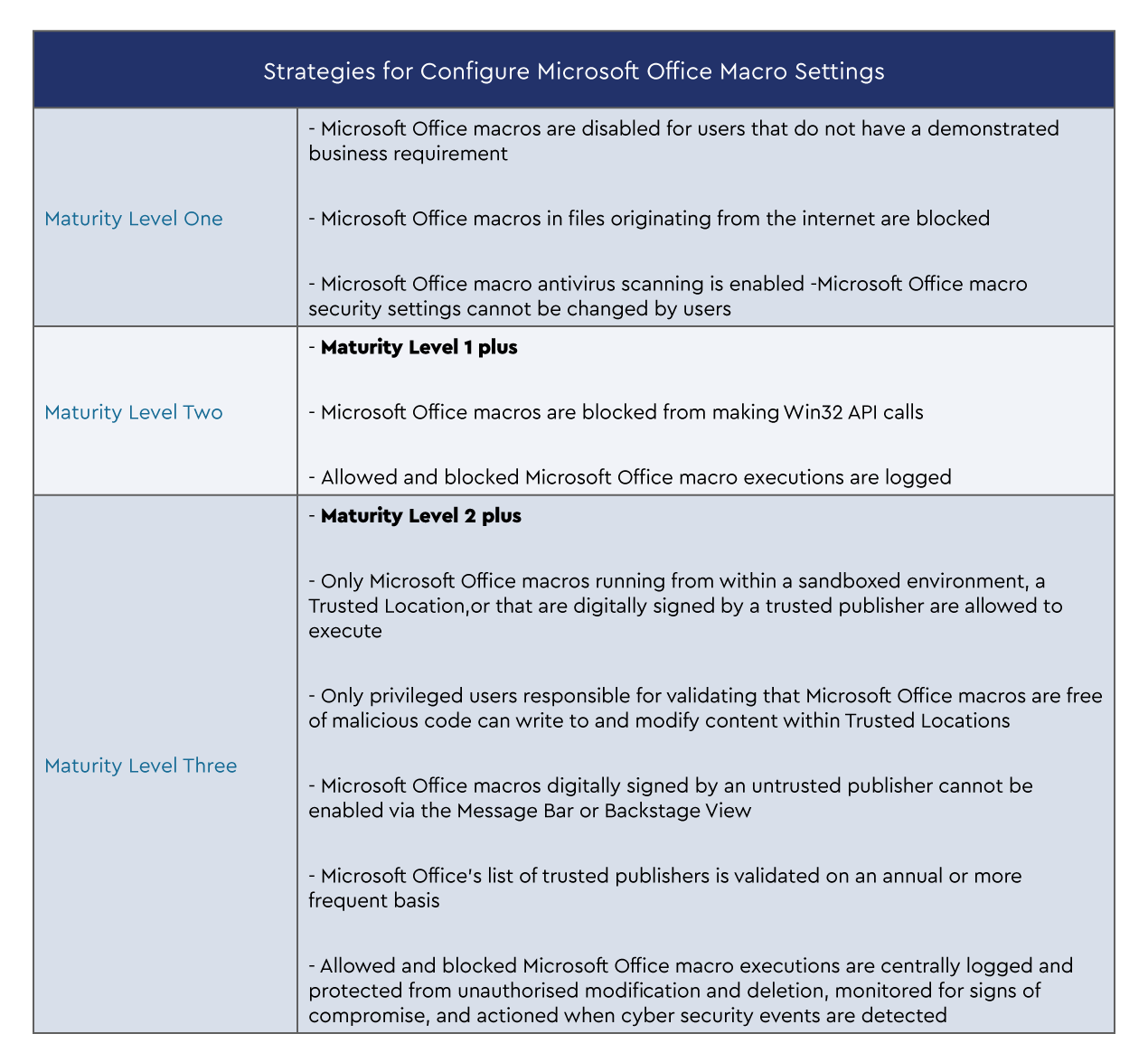
Please ensure you are referring to the complete original documentation from the ACSC when you are building out your processes to harden “configure Microsoft Office macro settings.” They have many extremely helpful resources to assist you.
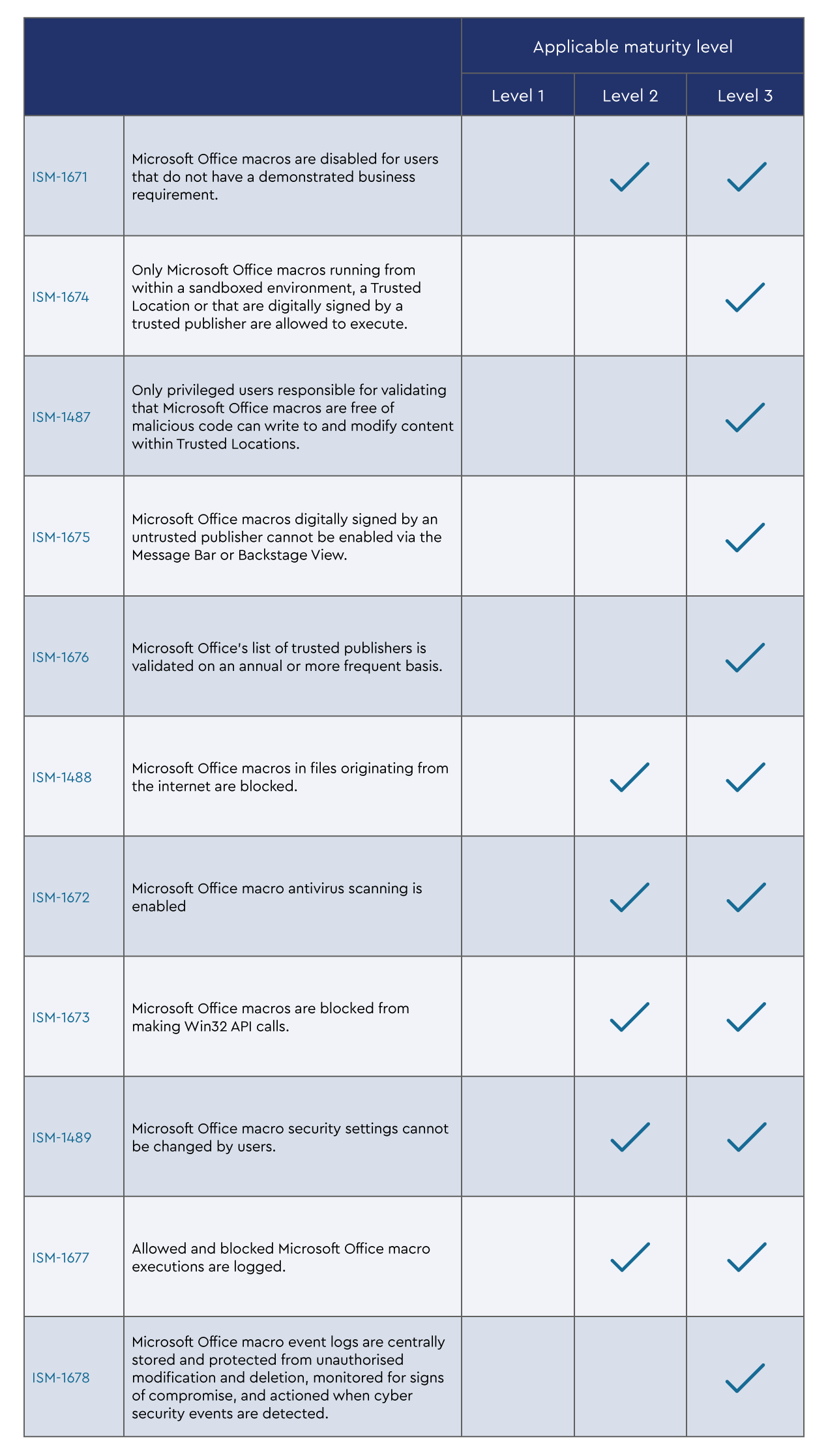
The ACSC uses the ISM to outline a cybersecurity framework using a risk management framework. As your security posture using the ACSC Essential Eight evolves to level two and level three maturity, the Essential Eight can be mapped to elements of the ISM. This mapping can assist with understanding how the Essential Eight fits within your security framework.
As is often the case, achieving Essential Eight level 1 maturity will not actually map to the ISM. You will need to achieve a level 2 maturity level to start mapping to the ISM.
We are seeing increasing activity around the use of malicious macros to compromise the operating environment of both small and large businesses. To bypass standard settings, adversaries have become fluent in manipulating users through social engineering.
Thus, when it comes to macros, it is essential for organisations to be clear on two things—what business requirement the macro fulfils and who needs to use it. With the right controls in place, users will not be put in a position where they have to decide what macros to trust.
While “Configure Microsoft Office Macro Settings” is identified as a separate set of controls in the ACSC Essential Eight Maturity Model, it also closely aligns with the next strategy—User Application Hardening. In the next part of this series, we will explore User Application Hardening and how these two strategies align to increase cybersecurity.