Innovative hacker TTPs that cause disastrous data breaches are constantly covered in the news. While it’s important to protect against these outside threats, all this focus on said outside threats may leave the health of your clients’ internal system components themselves to slip through the cracks.
Subsequently, processes like OS hardening become critical to optimizing the effectiveness of your cybersecurity efforts. For that reason, we’re going to take an in-depth look at OS hardening and why it’s an indispensable component of your MSP business.
What is OS hardening, and why does it matter for MSPs?
OS hardening is the process of using patching and other security measures to improve the security of a server’s operating system. This advanced cybersecurity protocol comes in the form of a software application that MSPs or IT admins need to run on the system to install these crucial updates.
Oftentimes, data protection and OS hardening are discussed simultaneously, but both are very different procedures. OS hardening focuses on increasing the protection of a system’s software and hardware assets while data protection simply focuses on having a robust backup procedure in place to replace lost, damaged, or corrupted data in the wake of a cyberattack.
The most efficient way to run OS hardening procedures is to have them implemented automatically by your client’s system. Typically, OS providers will include native notifications within their system to remind users to make these all-important updates.
While OS hardening itself is vitally important, this software is actually just a small part of the overall system hardening process. Savvy MSPs know that their client’s IT estate needs to be protected from every angle, and combine OS hardening with other techniques and updates like:
- Application Hardening – improving the security of internal and third-party applications
- Server Hardening – securing server ports, permissions, functions, and components
- Database Hardening – Installing updates and other advanced security measures to secure the information within a database, as well as a system’s entire database management framework
- Network Hardening – Updating and protecting the transmission of data or communication among computers and other various devices on a client’s network
Each of these processes plays its own role in protecting the sum of your client’s IT assets — and is necessary in its own way. But, making sure to include these in your client’s overall protection plan is only half the battle.
Additionally, you’ll need to deftly manage the patches for each facet of your client’s system to ensure seamless integration. Download our free Patch Management Best Practices eBook or contact us to get the most out of the patch and update process you use to serve your clients.
Why is OS hardening important for MSPs?
As an MSP, your end goal should be to make your client’s system bulletproof. Each item on your overall OS hardening checklist should be geared toward maximizing system protection at every level.
Configuring your client’s OS to the highest level of protection, executing system updates punctually and efficiently, implementing policies and procedures to help securely govern their system, and removing unnecessary apps and platforms are all part of the process. Ultimately, a foolproof OS hardening procedure is meant to minimize the exposure of the system’s backbone – the operating system – and stay ahead of any risks or problems before they start.
What are the different types of OS hardening?
As mentioned earlier, OS hardening is just a small part of your complete system hardening process. To gain the true benefit of what OS hardening is, you’ll need to implement it in conjunction with:
- Application hardening
- Server hardening
- Database hardening
- Network hardening
Application Hardening
Application hardening is the process of updating all your client’s internal and third-party software apps. This process aims to leverage software-based security measures to increase the overall security of the server and network.
Some steps to consider implementing during your application hardening process are:
- Using a firewall
- Selecting automatic software updates and patches whenever possible
- Installing antimalware and antivirus software
- Implementing a third-party app (like LastPass) to store and encrypt login credentials
- Create an intrusion prevention system (IPS) or intrusion detection system (IDS)
Server hardening
The data, ports, everyday functions, and components of your client’s servers can also be exposed to threats. Since servers are arguably the most critical component of any IT system, protecting them at every level is an essential part of cybersecurity.
The server hardening process is designed to protect a system’s servers at the software, firmware, and hardware level. Some techniques to consider implementing during this process include:
- Staying up-to-date on server patches and updates
- Requiring multi-factor authentication for users
- Disabling USB ports immediately upon startup
- Leveraging any advanced cybersecurity suites available based on OS – i.e., antivirus and firewall protection, memory encryption, firmware resilience technology, and more.
- Implementing strict password policies for users. Make sure their password credentials are longer and more complex
- Locking user accounts if they fail a certain number of attempted logins
- Creating and adhering to an update schedule for third-party apps
- Removing any third-party apps that threaten cybersecurity standards
- Using self-encrypting drives to store any highly-sensitive data
Database Hardening
Allowing a hacker access to just one database of information can be a veritable gold mine for them – and a nightmare for your clients.
Securing these valuable databases and the overall management system controlling them generally involves three steps:
- Controlling access to information based on user accounts
- Shutting down any unnecessary functions that could be used as an infiltration point
- Adding an extra layer of protection by encrypting these files
Several effective techniques could be used to handle each of these three aspects. Here are a few options available to help boost your clients’ database protection:
- Routine patching and updating of database management applications
- Disabling unnecessary database and database management functionality
- Require stronger, more complex passwords from users accessing database information
- Immediately lock down databases if the system detects suspicious logon activity
- Limit database access based on users’ roles
- Appointing only a small group of users as system admins
- Encrypting database information that is both resting and being transmitted
Network hardening
To protect data in transmission, MSPs need to focus on protecting the network – the structure responsible for an IT system’s communication. The two most effective ways of accomplishing this are through either an intrusion detection system (IDS) or an intrusion prevention system (IPS).
An IDS or IPS is a software application that will scan your client’s network for suspicious activity. And while these applications are incredibly effective, they’re at their best when paired with other network hardening practices.
In addition to using an IDS or IPS, MSPs should also be:
- reviewing and updating network access rules
- improving network firewalls
- disabling unused protocols or ports
- layering traffic with encryption
- auditing permissions
All of these supplementary tactics go a long way toward bolstering the performance of an IDS or IDP and, ultimately, hardening and protecting your clients’ networks.
What are the benefits of OS hardening?
The benefits of OS hardening are as broad and far-reaching as your client’s network itself. Because all departments are leveraging a company’s IT assets, protecting those assets can have a hand in improving all aspects of a business.
Some of the benefits your clients can expect to receive from your OS hardening protocols are:
- Stronger cybersecurity – hardening will reduce opportunities for hackers and minimize your clients’ vulnerability to breaches, attacks, or data leaks. You’ll also be able to stop the spread of any attacks that do happen to infiltrate the system.
- Better system performance – By staying up-to-date on patches and updates, removing unnecessary software, and disabling unnecessary functions, your clients will be left with a truly streamlined digital presence. Fewer applications and fewer peripherals mean less chance of operational and user error.
- Cost Improvements – Using less hardware and software, reducing the number of patches and updates necessary, relying less on malware removal, and freeing up system memory are all benefits of hardening that allow your clients to optimize cost efficiency on multiple fronts.
While some clients may hesitate to take the leap and incur the extra expense of your OS hardening services package, outlining these benefits is an easy way to show them how worthwhile it can be in the long run.
How does OS hardening differ between operating systems?
When it comes to the three main operating systems – Windows, Linux, or macOS – they each can accommodate varying levels of cybersecurity. One of the reasons for this is that each platform has its own OS hardening standards.
Windows is widely considered the least secure of the three. Experts cite a lack of innovation and security standards on the part of Microsoft as one of the main culprits. Additionally, enterprise-level Windows systems tend to leave organizations with heavy exposure to digital attacks and large attack surfaces.
As we move up the spectrum toward more secure options, MacOS is next. This is due, in part, to the fact that the overwhelming majority of computer users chose Windows for decades. However, in recent years, Apple’s share of the market has been growing. As a result, digital threat actors are beginning to set their sights on Mac targets more often.
Another reason for Mac’s increased security is that Mac devices come out of the box with very few network services connected. Therefore, Mac computers in their default state are very secure. But, this may change once users power them on, personalize them, and connect peripheral network services.
Finally, we have Linux. Linux OS is different than Windows or macOS in that it’s open-source. While you might think this exposes it to more vulnerabilities, it’s actually the opposite.
Since Linux is open-source, its community of users contributes to its cybersecurity. With a community of millions of users reviewing Linux code and constantly issuing Linux patches and updates, the Linux OS remains highly secure and stays ahead of the newest hacker trends and techniques.
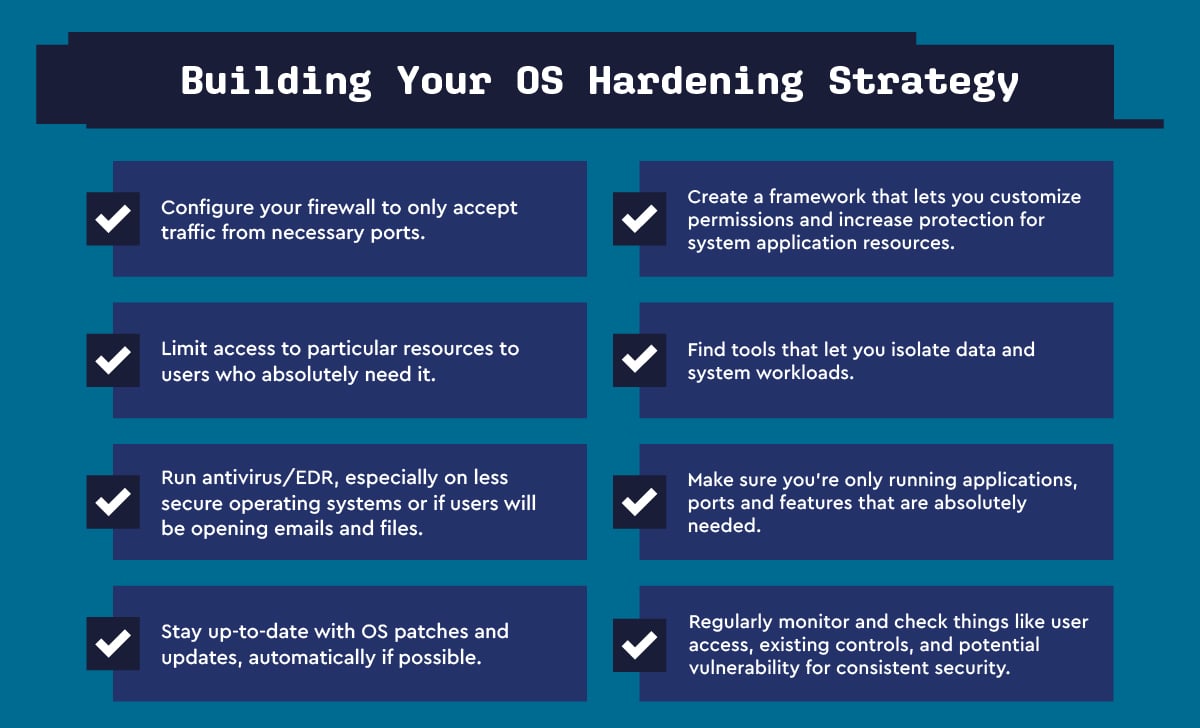
Your OS hardening checklist
Now that you understand the importance of OS hardening, it’s time to implement a foolproof hardening process for your managed IT service clients. Here is a brief OS hardening checklist to get you started:
- Configure firewall – set up the firewall to only accept traffic from necessary ports only.
- Limit access – Take advantage of defined user roles within your client’s system. Only grant access to particular resources to users who absolutely need it. In addition, be sure to create user policies so your entire team knows their role and access level.
- Don’t skip antivirus/EDR – On less secure systems – like Windows or macOS, running antivirus can add a layer of protection. This especially applies if users on these systems will be opening files and emails. In the face of modern threats, antivirus may not even be enough. We recommend endpoint direction & response (EDR) solutions for best-in-class OS hardening.
- Patches and updates – stay up-to-date with OS patches and updates. Be sure to elect to have your clients’ OS automatically install them whenever possible.
- OS hardening frameworks – Certain operating systems will allow you to customize permissions and increase protection for system application resources.
- Isolation tools – Isolate data and system workloads from each other as much as possible. This can be done by hosting databases or running applications inside different virtual machines or servers. By leveraging isolation, you’ll minimize the potential damage a hacker can do if they were to infiltrate a client’s system.
- Run only what’s necessary – eliminating unnecessary data ports, software apps, and more can free up system resources and minimize exposure to digital attacks. Any hardware peripherals, software applications, or OS features not being used should be shut down.
- Be vigilant – From establishing baselines and checking them regularly to reviewing user access at least every month, regularly monitoring the security of your OS is essential for long-term protection.
ConnectWise is here to help. Feel free to contact us with any questions you have regarding MSP services. We have you covered from basic to advanced needs, and our suite of cybersecurity tools is bound to have something that’s easy to implement and gives your clients all the cybersecurity protection they need.
















