Welcome to the May 2025 edition of the ConnectWise Cyber Research Unit™ (CRU) Monthly Threat Brief. This report provides a comprehensive look at the most significant cybersecurity developments impacting the MSP and SMB landscape. We break down the month’s top stories, critical vulnerabilities, and prevalent malware families to help you stay informed and prepared in an evolving threat environment.
The SERPENTINE#CLOUD campaign represents a sophisticated abuse of Cloudflare’s tunnel infrastructure to deliver remote access trojans through advanced evasion techniques. Attackers initiate infections via phishing emails containing malicious Windows shortcut files disguised as invoice documents, which trigger a multi-stage execution chain leveraging WebDAV shares hosted on Cloudflare tunnel subdomains. The attack employs Early Bird APC injection (T1055.004) to execute Python-based shellcode loaders that create suspended notepad.exe processes and inject malicious code before security hooks can intercept it.
The campaign's technical sophistication lies in its memory-only execution model using the donut framework to load PE files entirely in memory, bypassing signature-based detection and file integrity monitoring. Final payloads typically consist of AsyncRAT or RevengeRAT, providing full command and control capabilities. The infrastructure choice of Cloudflare tunnels (trycloudflare.com) provides encrypted HTTPS transport, legitimate domain reputation, and ephemeral subdomains that complicate takedown efforts while avoiding the need for attackers to maintain their own infrastructure.
What this means for MSPs
MSPs face significant operational challenges as they cannot implement blanket blocking of trycloudflare.com due to legitimate client dependencies on Cloudflare tunnels for development and remote access. The memory-only execution model creates detection gaps for cost-effective security stacks typically deployed in MSP environments, as most EDR solutions focus on file-based indicators rather than behavioral analysis of in-memory threats.
The invoice-themed social engineering directly exploits business workflows common across MSP client bases, particularly targeting finance teams who regularly process external payment requests, making user education insufficient as a primary defense. MSPs must prioritize advanced email security controls with behavioral analysis capabilities and memory scanning features, especially for finance-sector clients, while implementing detection strategies that focus on process injection patterns and suspicious memory allocation behaviors rather than traditional file-based signatures.
Microsoft patched four critical remote code execution vulnerabilities in Office applications during June (CVE-2025-47162, CVE-2025-47164, CVE-2025-47167, CVE-2025-47953) that exploited fundamental memory management flaws, including heap-based buffer overflow, use-after-free conditions, and type confusion errors. All four of these vulnerabilities leveraged preview pane exploitation, enabling zero-click attacks that required only email receipt or document access without user interaction. Microsoft tagged all four CVEs with "Exploitation More Likely" ratings, with three scoring 8.4 on the CVSS scale, indicating both high severity and active threat potential.
The preview pane attack vector in these vulnerabilities creates significant security challenges by bypassing user training controls and eliminating social engineering dependencies for successful exploitation. MSP clients running Office preview functionality face heightened risk exposure, particularly in email-heavy business environments where these vulnerabilities provide viable initial access paths for potential attackers.
The combination of high CVSS scores and zero-click exploitation capabilities requires MSPs to accelerate patch deployment schedules and evaluate temporarily disabling preview pane features for critical client environments until remediation is complete, fundamentally altering standard Office security risk assessments for managed environments.
This section leverages the Diamond Model of Intrusion Analysis to structure the examination of recent malware activity, providing a clear analytical framework that links adversary, capabilities, infrastructure, and victimology. By applying the Diamond Model, we can better contextualize malicious behavior, identify patterns across campaigns, and highlight the relationships between threat actors, tools, and targeted entities.
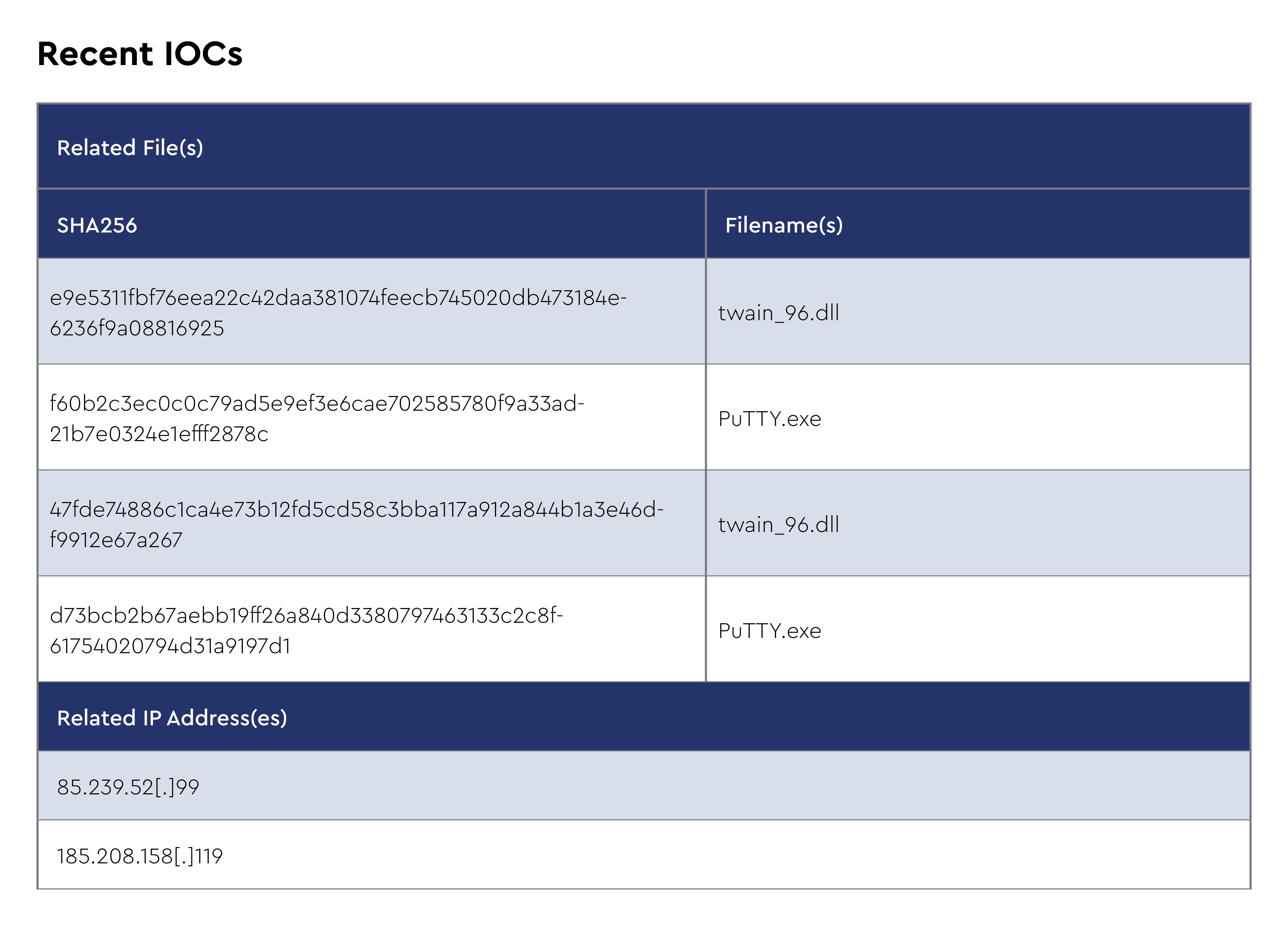
Oyster is a C++-based backdoor malware first discovered in July 2023, though IBM researchers first documented it in September 2023. The malware enables remote sessions, file transfers, and command-line operations, allowing attackers full control over infected systems through communication with hard-coded command-and-control servers.
Oyster has been consistently used by various threat actors to support ransomware operations, including documented use by the Rhysida ransomware group in attacks against academic institutions. What distinguishes Oyster from other backdoors is its evolution from requiring a dedicated loader component to direct deployment via trojanized legitimate software installers, particularly targeting popular applications such as Microsoft Teams, Google Chrome, and WinSCP.
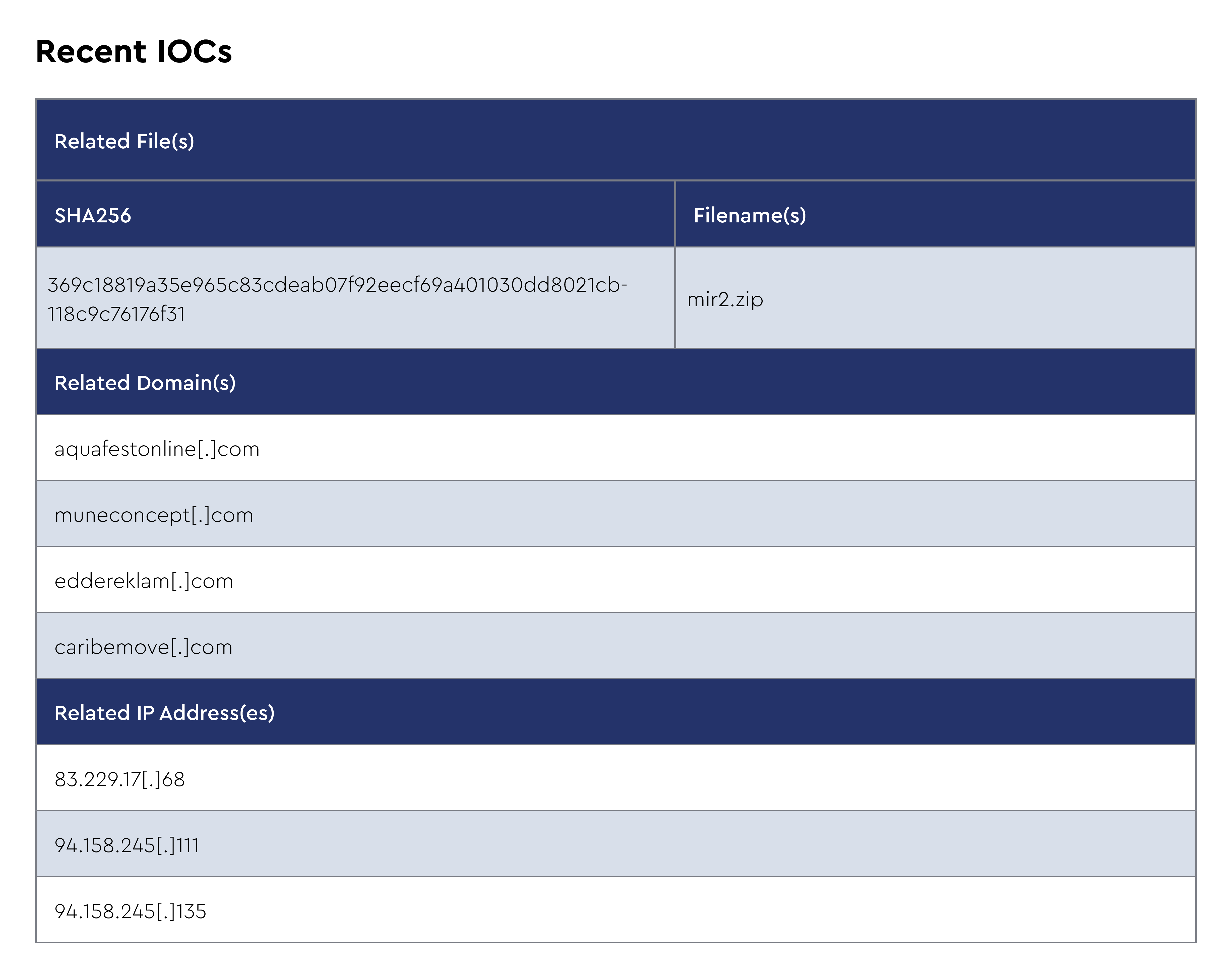
In June 2025, the ConnectWise CRU spotted a campaign where malware masquerading as PuTTY was delivering Oyster as a backdoor. This represents a continuation of the malvertising and SEO poisoning tactics targeting legitimate IT tools that the CRU has been tracking and highlighting for some time. The campaign leverages persistence through scheduled tasks running every three minutes, executing malicious DLLs via rundll32.exe using DLL registration mechanisms, demonstrating the continued evolution of Oyster's distribution methods targeting IT professionals through commonly used administrative tools.
Aliases
Infrastructure
Victimology
Capabilities
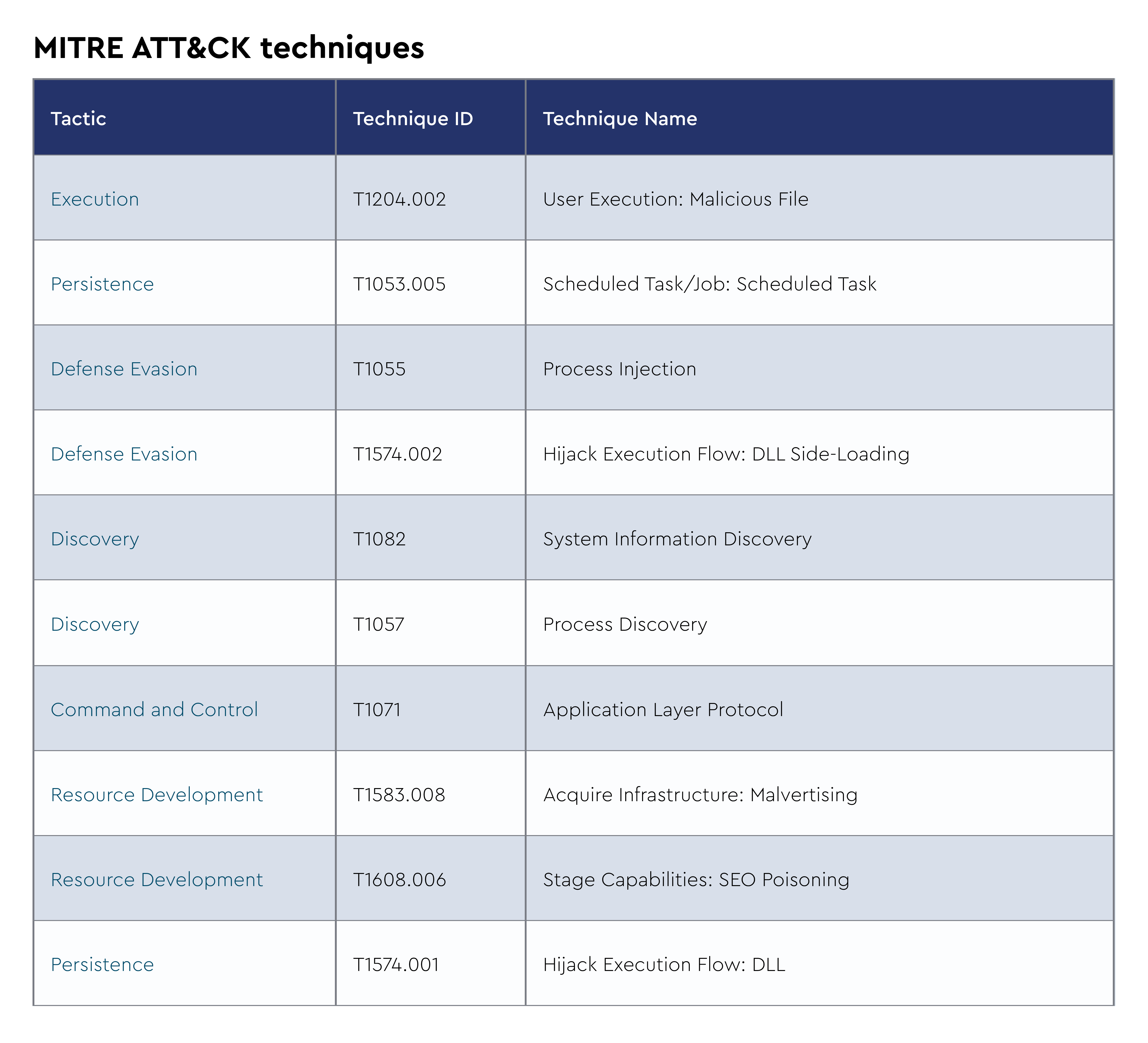
Stealc is an information stealer first advertised by its presumed developer, Plymouth, on Russian-speaking underground forums on January 9, 2023, and sold as a malware-as-a-service. According to Plymouth's statement, Stealc is a non-resident stealer with flexible data collection settings, and its development relies on other prominent stealers: Vidar, Raccoon, Mars, and Redline. Written in C, Stealc comes with capabilities to steal data from web browsers, crypto wallets, email clients, and messaging apps, and also boasts of a "customizable" file grabber that allows its buyers to tailor the module to siphon files of interest. What sets it apart is its efficient approach: with each data allocation, Stealc directly transmits the information to the C2 server, bypassing the need to write it to a raw file, enhancing both its data exfiltration capabilities and its ability to maintain a low profile.
In March 2025, the developer released StealC v2, marking a major upgrade with a focus on stealth and versatility, introducing a streamlined JSON-based command-and-control protocol, expanded payload delivery options, and a redesigned web control panel with a built-in builder. Recent campaigns observed by the CRU have shown Stealc incorporating NetSupport RAT as a secondary payload for remote access capabilities, while maintaining its signature evasion techniques, including process injection, ETW bypass mechanisms, and sophisticated obfuscation of PowerShell and command-line activities. The malware continues to establish persistence through autorun registry modifications and leverages legitimate tools like cmd.exe, csc.exe, and PowerShell to blend with normal system operations.
Infrastructure
Victimology
Capabilities
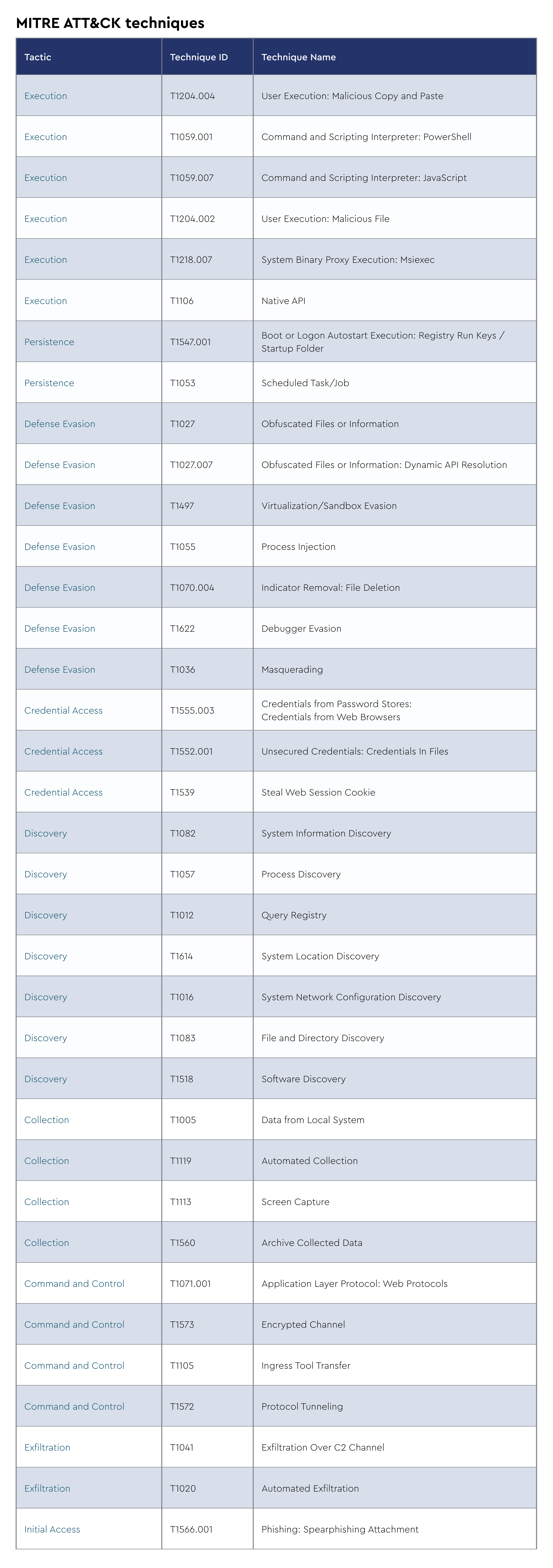
Akira ransomware emerged in March 2023 as a ransomware-as-a-service (RaaS) operation that quickly established itself as a formidable threat actor, with researchers identifying links to the defunct Conti ransomware group through code similarities and operational patterns. Based on trusted third-party investigations, Akira threat actors have been observed deploying two distinct ransomware variants against different system architectures within the same compromise event, including the Windows-specific "Megazord" ransomware and a novel variant of the Akira ESXi encryptor, "Akira_v2".
The Akira v2 encryptor is an upgrade from its previous version, written in Rust with additional functionalities, including the ability to insert additional threads for more granular control over CPU cores, increasing encryption speed and efficiency. Akira uses double-extortion ransomware techniques, in which data is exfiltrated from the environment before it is encrypted with threats to publish this data if a ransom is not paid.
Akira has risen in popularity, claiming the number one spot as the most active ransomware group targeting MSPs in 2025, based on incidents reviewed by the CRU. The group operates with flexible ransom demands ranging from $200,000 to millions of dollars and offers victims the option to selectively pay for specific services such as decryption assistance, data deletion guarantees, or security vulnerability reports. While no specific June 2025 incidents were identified in current reporting, Akira's continued evolution with enhanced capabilities and persistent targeting of critical infrastructure organizations maintains its position as a top-tier ransomware threat.
Aliases
Infrastructure
Victimology
Capabilities
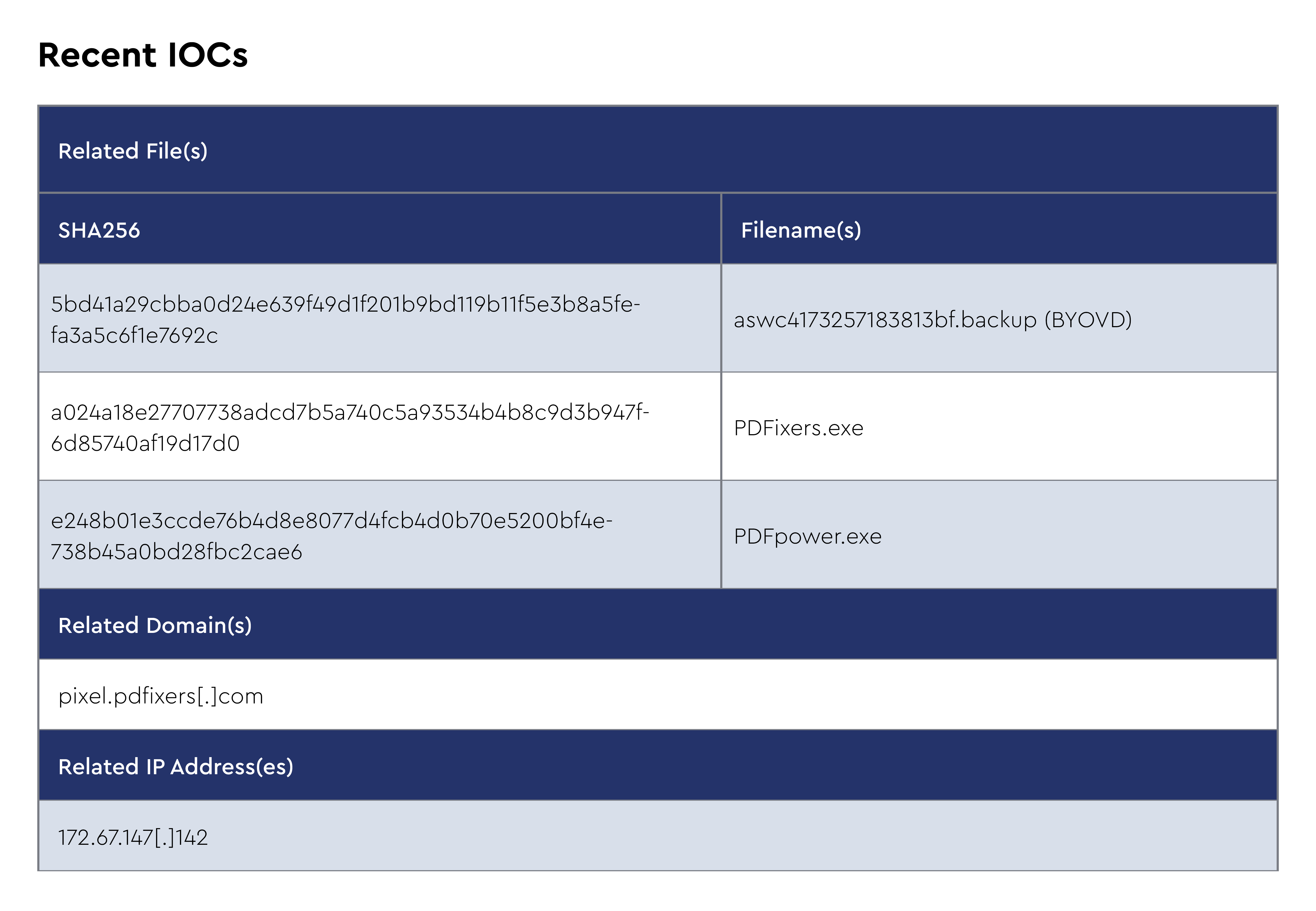
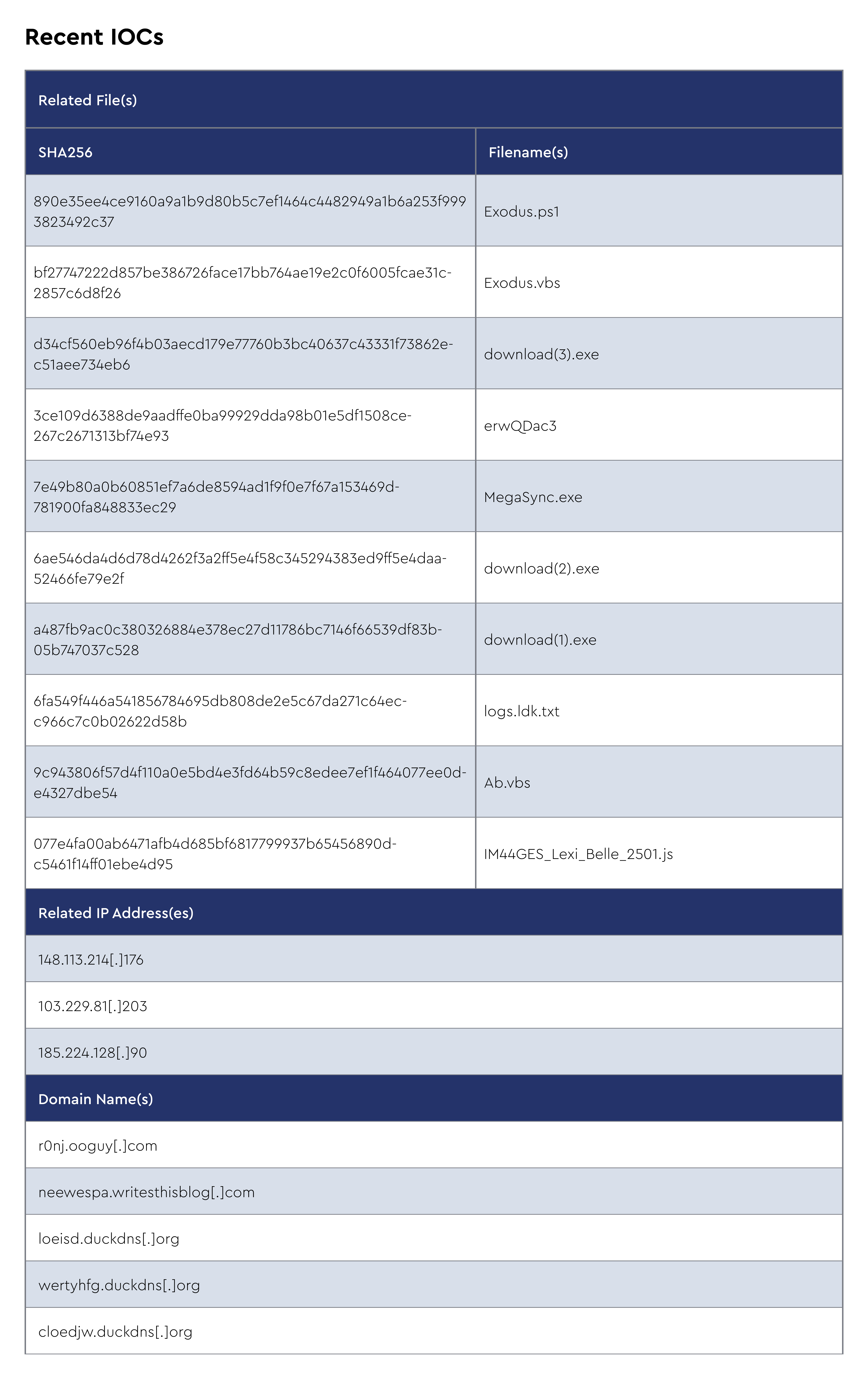
AsyncRAT is a sophisticated remote access trojan (RAT) that has maintained significant presence in the threat landscape since its initial emergence around 2019-2020. Originally developed as an open-source project, AsyncRAT provides attackers with comprehensive remote control capabilities over compromised systems, including keylogging, screen capture, file manipulation, cryptocurrency theft, and the ability to deploy additional payloads.
What distinguishes AsyncRAT from other RATs is its modular architecture, active development community, and readily available source code, which has enabled threat actors to easily customize and deploy variants tailored to specific campaigns. The malware typically establishes persistence through registry modifications and scheduled tasks, while employing various evasion techniques, including process hollowing and encrypted command-and-control communications to avoid detection.
Based on CRU analysis of recent incidents, AsyncRAT continues to demonstrate tactical evolution in its delivery and execution methods. Our observations reveal threat actors leveraging diverse initial access vectors, including VBScript files masquerading as legitimate applications (Exodus.vbs), trojanized cloud storage applications (MegaSync.exe), and social engineering lures using adult content themes in JavaScript attachments.
The malware exhibits sophisticated evasion techniques such as XML-based payload extraction, PowerShell-based .NET assembly loading directly into memory, and multi-stage download processes that retrieve and decode remote assemblies. These incidents demonstrate AsyncRAT's continued adaptation to bypass modern security controls while maintaining its core remote access capabilities.
Infrastructure
Victimology
Capabilities
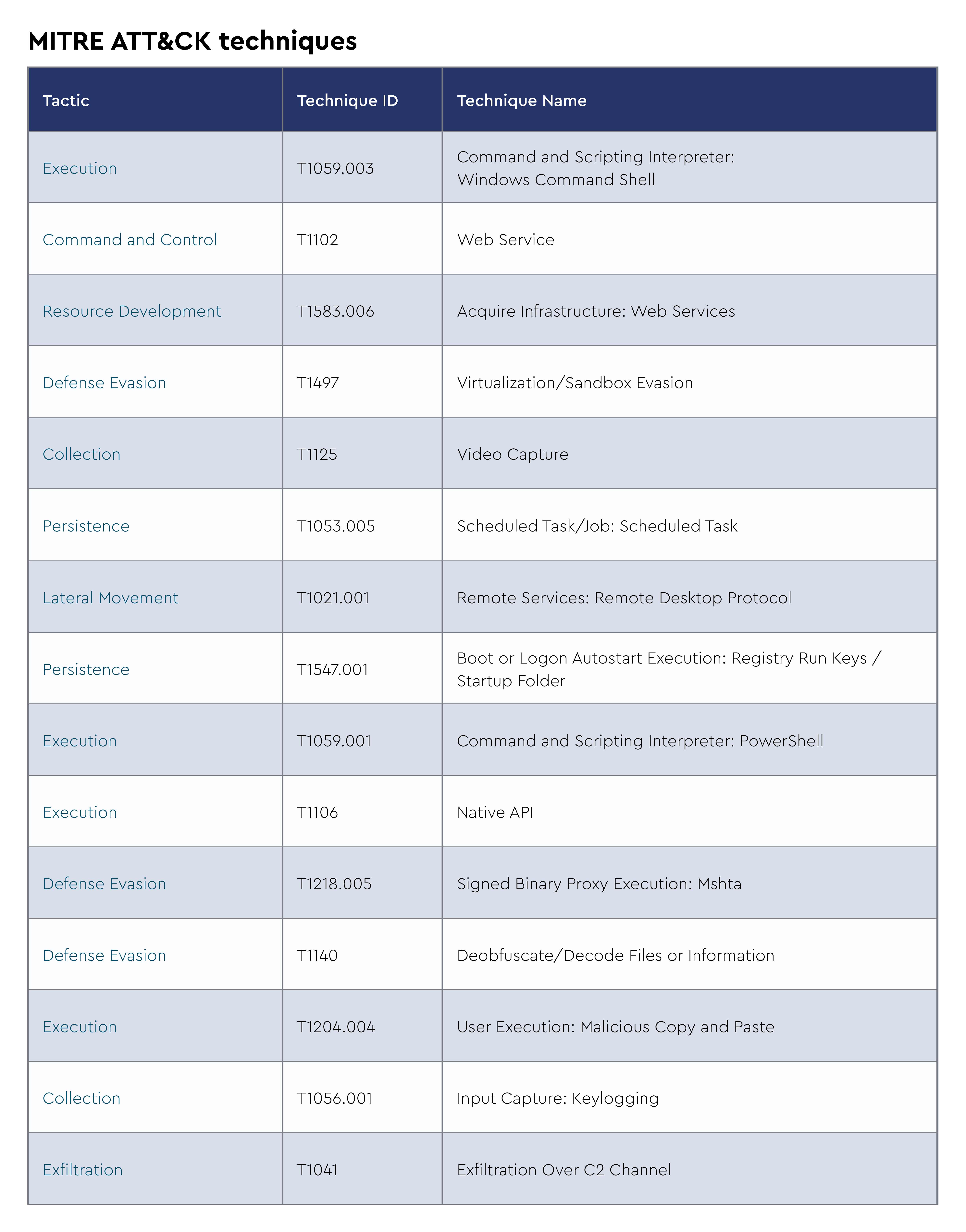
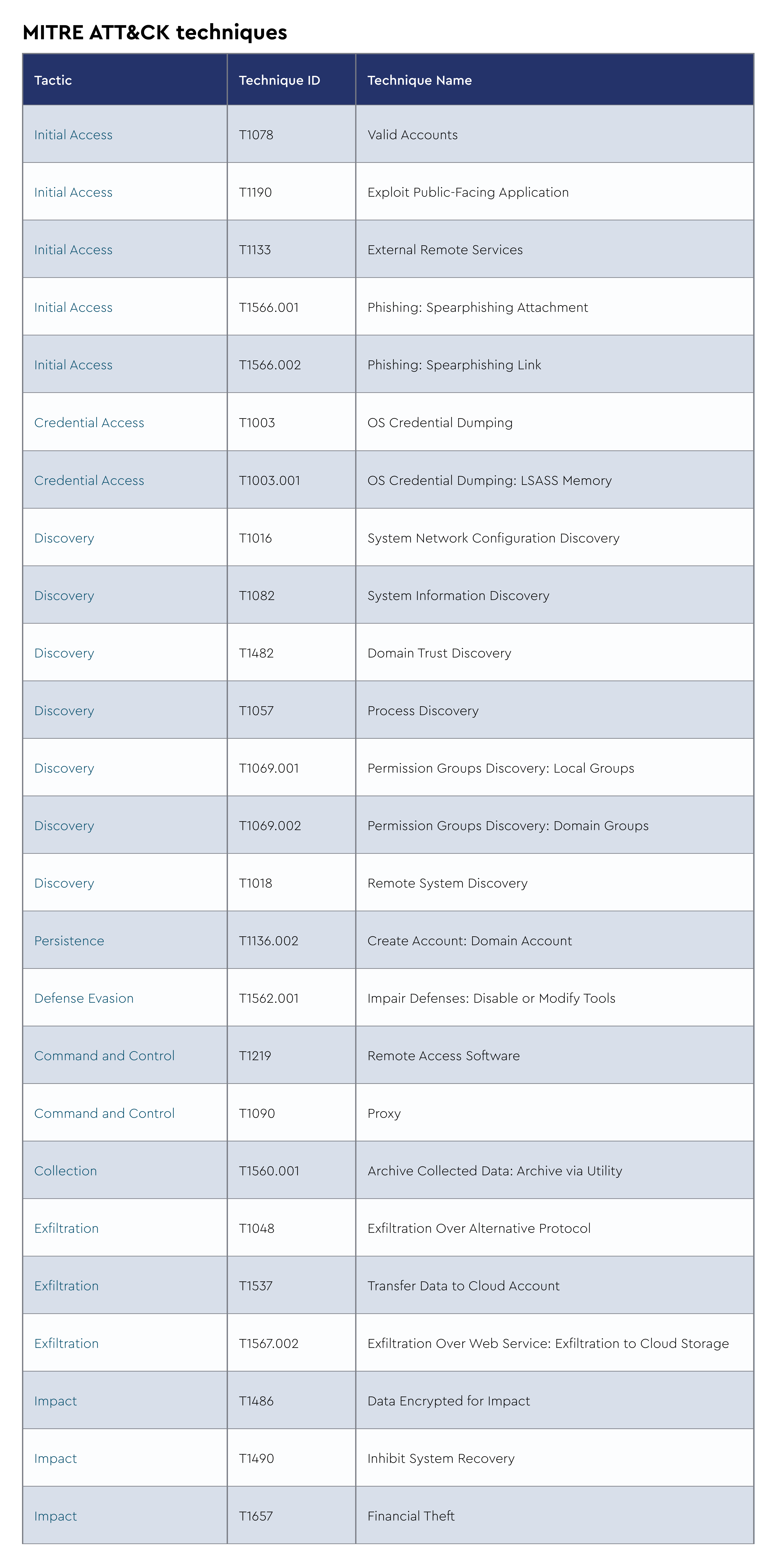
Interlock is a relatively new ransomware group that first emerged in September 2024, conducting big-game hunting and double extortion attacks. Cisco Talos assesses with low confidence that Interlock ransomware is likely a new diversified group that emerged from Rhysida ransomware operators or developers, based on similarities in tactics, techniques, and procedures (TTPs) and in the ransomware encryptor binaries.
The ransomware affects both Windows and FreeBSD platforms, encrypting files with the ".interlock" extension and dropping ransom notes titled "!README!.txt". What distinguishes Interlock from other ransomware families is its hybrid approach and cross-platform capabilities, along with its use of Azure Storage Explorer and AZCopy to exfiltrate victim data to attacker-controlled Azure storage blobs. The group has evolved to incorporate novel techniques such as SocGholish malware delivery and human verification social engineering elements, while experimenting with ClickFix techniques in early 2025 that use deceptive CAPTCHAs to trick users into running malicious PowerShell commands.
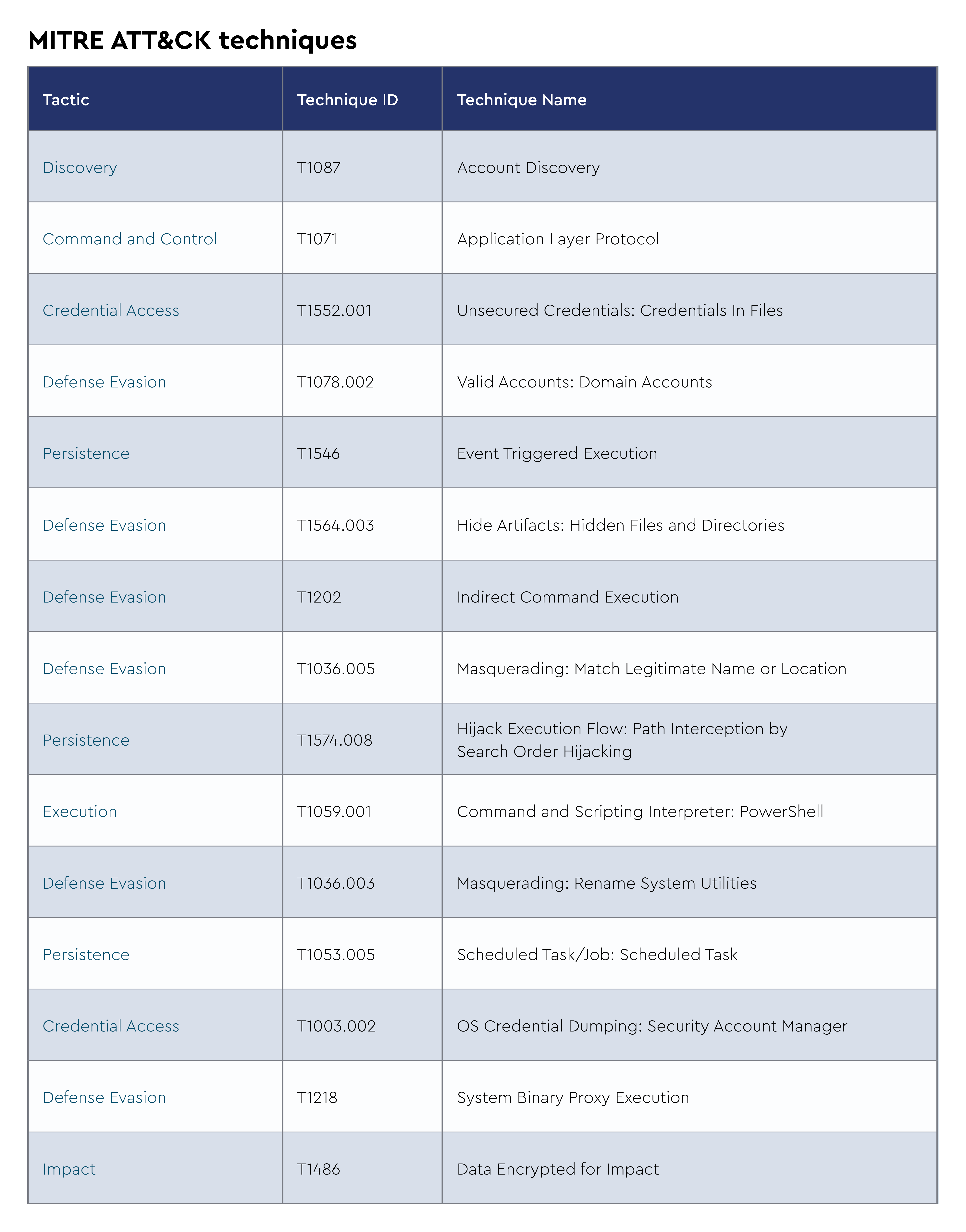
Intelligence from early 2025 shows Interlock incorporating new data theft utilities, including BerserkStealer and LummaStealer, while their ClickFix campaigns were last observed in February 2025, suggesting experimental tactics that may have been abandoned due to limited effectiveness. The group continues operating their "Worldwide Secrets Blog" data leak site, maintaining pressure through double extortion tactics while demonstrating adaptability in their technical arsenal and targeting methodologies. In the most recent Incidents, we’ve also observed threat actors running commands that access the SAM database, an indicator that they may also be stealing password hashes.
Infrastructure

Victimology
Capabilities