As the Greek philosopher Heraclitus once said, “Change is the only constant in life.” Everything in the universe is constantly in flux, and nowhere is this truer than in our digital IT universe.
Companies and their networks are constantly growing and changing. As an organization’s network expands to take on more devices and more employee endpoints, it’s a good idea to run network assessments continually.
Network assessment tools help MSPs and other IT professionals take this intricate process and make it more manageable at scale as their own MSP customer networks change. These assessments cover a broad spectrum which includes individual assessments of multiple network components. To cover such a scope, MSPs truly need to understand how these assessments work, and also rely on tools, procedures, and systems to guide their overall process.
MSPs leverage network assessments as a part of their larger cybersecurity risk assessment, to evaluate the performance and condition of a client’s digital infrastructure. There are various factors to consider when conducting a network assessment, like bandwidth resources, bandwidth usage, and any potential network updates your client should consider.
In the modern workplace, the network assessment process is even more challenging. With employees working remotely and accessing a company’s primary network over less-secure home Wi-Fi connections, MSPs must take additional precautions regarding the devices accessing the network.
Occasionally, remote workers will receive equipment from their company. The internal IT department scans and configures these laptops or desktop PCs. This process limits network vulnerabilities since IT and cybersecurity staff directly control and monitor the process.
However, if employees have to use their own devices from home, things can get much more nebulous. Network security can be significantly compromised. As a result, companies need to consider their bring-your-own-device (BYOD) policy when conducting a vulnerability assessment.
Below are the steps you should follow when conducting a network vulnerability assessment. Use this checklist to ensure you’re considering all the important facets of vulnerability management best practices. The list also contains an update to help you cover our new BYOD remote work environment.
You’ll need to create formal policies for BYOD practices if your clients have remote team members. This might include setting minimum security policies for their at-home office, issuing patching and updating schedules, or planning routine remote sessions for maintenance.
Ultimately, the goal is to minimize any risk or exposure from employees accessing company files over insecure networks. Evaluating policies you have in place or mapping a policy from the ground-up will give you insights into which devices cause network issues and who are responsible for them. You’ll also be able to spot any unauthorized third-party apps or unknown hardware and shut them down before they cause significant damage to your client’s infrastructure.
Vulnerabilities can exist across various platforms within the network. They can come from hardware, software, and the surrounding environment. Hackers are constantly attempting to exploit these vulnerabilities for their own gain, compromising your client’s entire system in the process.
Creating and constantly re-evaluating your client’s BYOD policy goes a long way toward reducing vulnerabilities. Other vulnerabilities are inherent in digital networks beyond employees, their devices, and their insecure networks, though.
Some of the most widespread threats to look for on client networks are third-party apps, weak passwords, or poor patch management. Passwords should be complex enough not to be guessed and regularly changed. An accurate record and schedule of software patches and updates should also be kept to ensure your clients are always running up-to-date applications.
Unless your client’s organization has the luxury of unmetered bandwidth, only a finite amount of bandwidth is available to their team members. A specific amount of bandwidth resources might be great to start out. But what happens as your client’s business grows?
Continuous evaluation of bandwidth resources provides insight into which devices and applications are pulling the most bandwidth. It can also tell you if the current bandwidth is adequate or if you need to talk to your client about expanding their resources.
Your client’s network infrastructure encompasses all the hardware and software they use daily. Examining bandwidth and making any necessary fixes helps to strengthen network infrastructure. But there are other sources of issues that may cause a network framework to fail.
It’s a good idea to work with your clients on creating a network map. Consulting the map of the overall system can help you spot any load balancers or abandoned firewalls. MSPs must locate and resolve these weaknesses for their clients as they can cause major problems later.
You must understand how your clients handle their data and files to make them truly secure. How do they share, access, and store their important files?
Once you understand how they use data, you can more easily secure invaluable digital assets for them. This is an essential part of your role for 2 reasons. First, data is important. Ensuring its purity and safety is a no-brainer. But secondly, insecure data is one of the leading causes of network breaches.
Your data strategy should encompass a plan to safeguard your client’s data, but it should also cover any compliance requirements and a mitigation plan should any of these compliance regulations get accidentally violated.
At the very least, you should grant file or data access on a permission basis. Any folders within your client’s network that still have “public” settings should be re-configured. Adopt the principle of “least privilege” and only give as much access as is necessary not to hurt productivity.
Visit the ConnectWise cybersecurity center to dive deeper into key cybersecurity concepts like “least privilege” and more.
This is the point of the checklist where “the rubber meets the road.” After assessing all aspects of your client’s network, it’s now time to decide. Is an upgrade necessary?
Sometimes, it may not be time for an upgrade, but other actions should be taken. It’s up to you, as an MSP, to analyze the findings in your network vulnerability report and suggest an appropriate next course of action. That may be as small as adding or removing endpoints, making software upgrades, or streamlining network policies.
One popular cause of network issues is software or hardware upgrades. Unfortunately, these cyber events could be avoided by focusing more effort on regular maintenance. Implementing network tools that offer features like automated patch management is an easy way to rectify this issue.
A network assessment’s true power comes from its ability to synthesize and report on everything happening within a company’s infrastructure. This means quite the large-scale gathering and computing of information, even for the smallest businesses.
Network assessment tools help aggregate and organize this data. MSPs with network assessment tools can spot trends and make data-driven decisions that help keep their clients ahead of the competition and sophisticated cybercriminals.
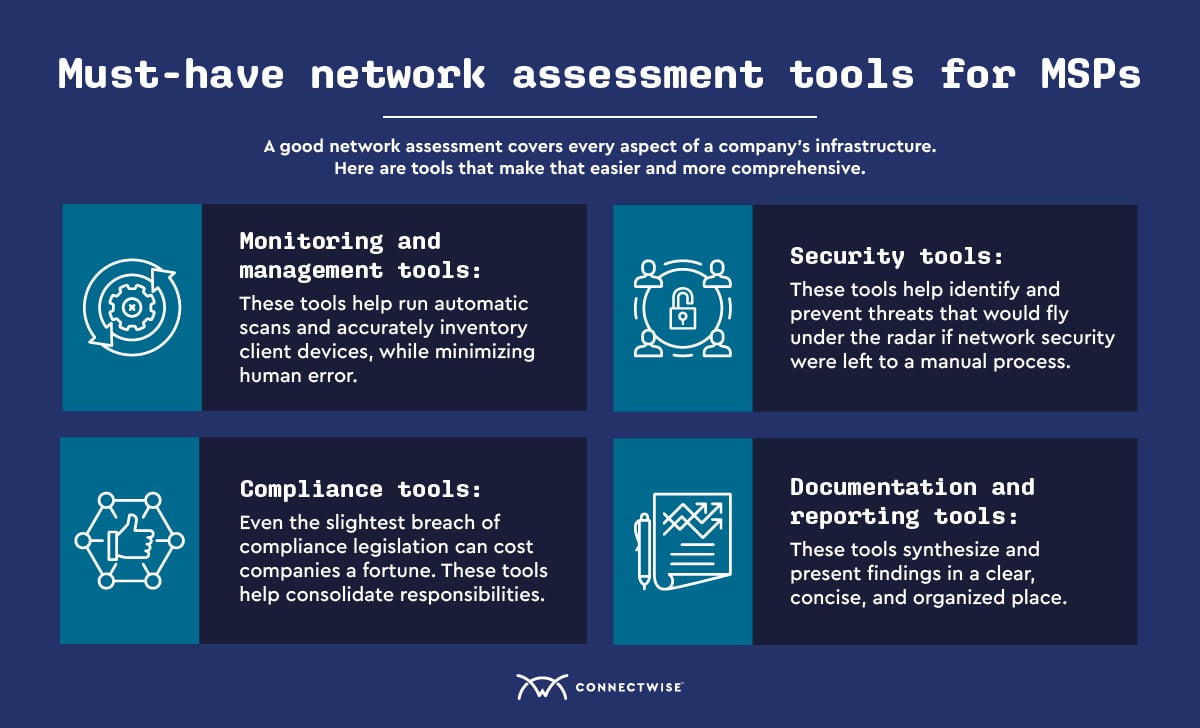
Every MSP should have some essential tools that help strengthen the accuracy of your network assessment. Here are some of the key components for your “toolbelt.”
The proper monitoring and management tool makes an MSPs life infinitely easier. You need a tool to ensure compliance with industry regulations, run automatic scans, and accurately inventory client devices. Doing any of these things manually can introduce excessive human error into your processes and is a recipe for disaster.
Security assessment tools are essential to your client’s overall infrastructure protection. These tools help identify and prevent threats that would fly under the radar if network security were left to a manual process. Tools like vulnerability managers, endpoint scanners, and data loss prevention platforms can be life savers when MSPs leverage them properly. MSPs can take advantage of platforms that offer all of these tools in one package by electing to implement a security operations center as-a-service (SOCaaS) platform or robust SIEM services.
Cybersecurity, fraud, and cybersecurity inconsistencies continue to worry many system admins. Even the slightest breach of compliance legislation can cost companies a fortune, depending on their industry. Many industries, especially financial and healthcare enterprises, must take every advantage available to remain vigilant.
Managing industry compliance in addition to other duties can overwhelm even the best MSPs. Using a tool like a professional service automation (PSA) platform can help consolidate these responsibilities, allowing you to focus on providing first-class MSP services and growing your client base.
Without the proper network assessment tools for documentation and reporting, your assessment won’t do your clients much good. The goal of analyzing their network is to synthesize information into data-driven insights that can optimize your client’s network. To do that, you need reporting and documentation that presents your findings in one clear, concise, and organized place.
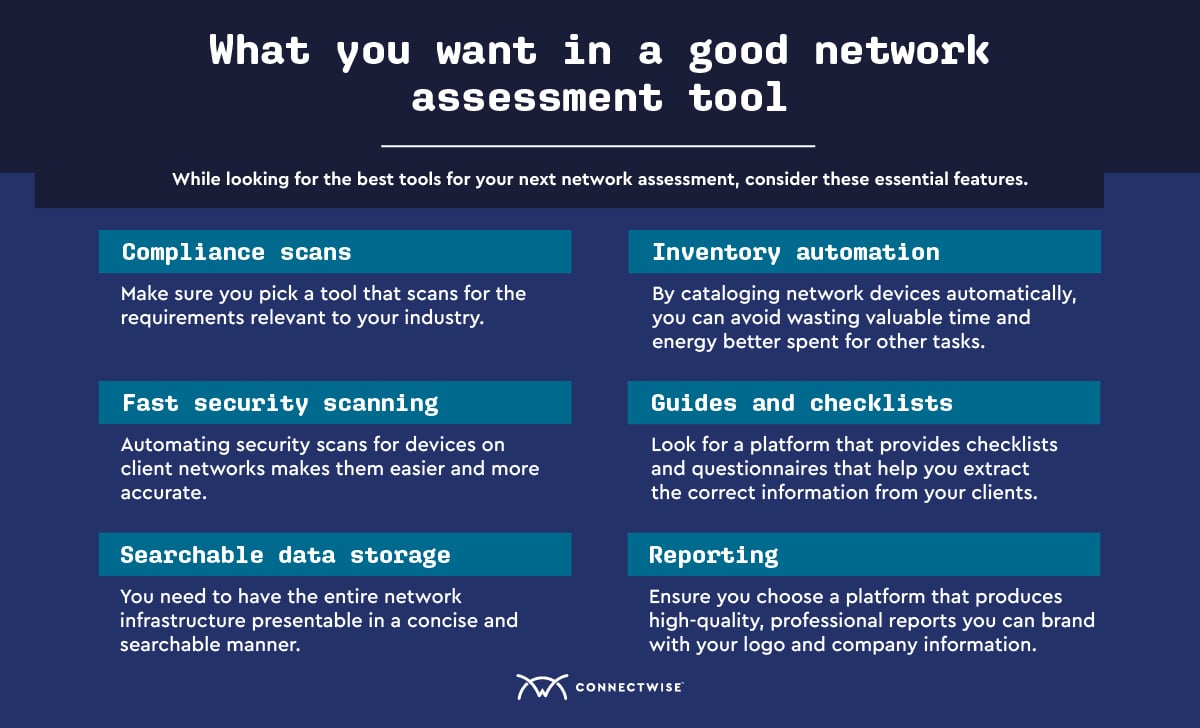
The amount of network assessment tools available today can be overwhelming. It’s easy to make the wrong choice and be left with something that doesn’t serve your clients. To avoid making that type of purchase, here are the features you should be searching for when you’re shopping:
Network assessment tools are a necessary part of your repertoire if you want to grow in the MSP industry. The right platforms will free you to focus on your highest-level tasks like business development and customer service. The automation and organization these tools provide will also make your assessments more accurate, organized, and reduce the impact of human error.
Are you ready to scale your MSP team and services? Start your free trial or view a demo of any of our network assessment tools, and learn what making ConnectWise a trusted partner in your business can do for you.
There are 5 key steps to test for network vulnerabilities:
The primary types of network vulnerabilities are the following:
Network assessment tools accomplish several critical network security functions. They scan system endpoints, automatically inventory network devices, and automate software patch management. Without these tool platforms, manual upkeep would leave room for human error to significantly compromise overall cybersecurity.