7/17/2025 | 7 Minute Read
Topics:

As cyberattacks grow more sophisticated, organizations are rethinking how they identify and eliminate risk. Two core components of any effective cybersecurity strategy, attack surface management and vulnerability management, are often confused or used interchangeably. While both aim to reduce risk, they operate in fundamentally different ways and address various stages of the security lifecycle.
Understanding the distinction between attack surface management and vulnerability management helps IT teams and managed service providers (MSPs) build a more comprehensive security posture that detects known weaknesses and uncovers hidden exposures before threat actors can exploit them.
Understanding the difference between attack surface management and vulnerability management is critical for building a layered cybersecurity strategy. While both aim to reduce organizational risk, they target different areas of the security lifecycle.
Attack surface management focuses on discovering every asset and potential exposure, while vulnerability management zeroes in on known weaknesses within those assets.
The table below highlights the primary distinctions between attack surface management and vulnerability management:
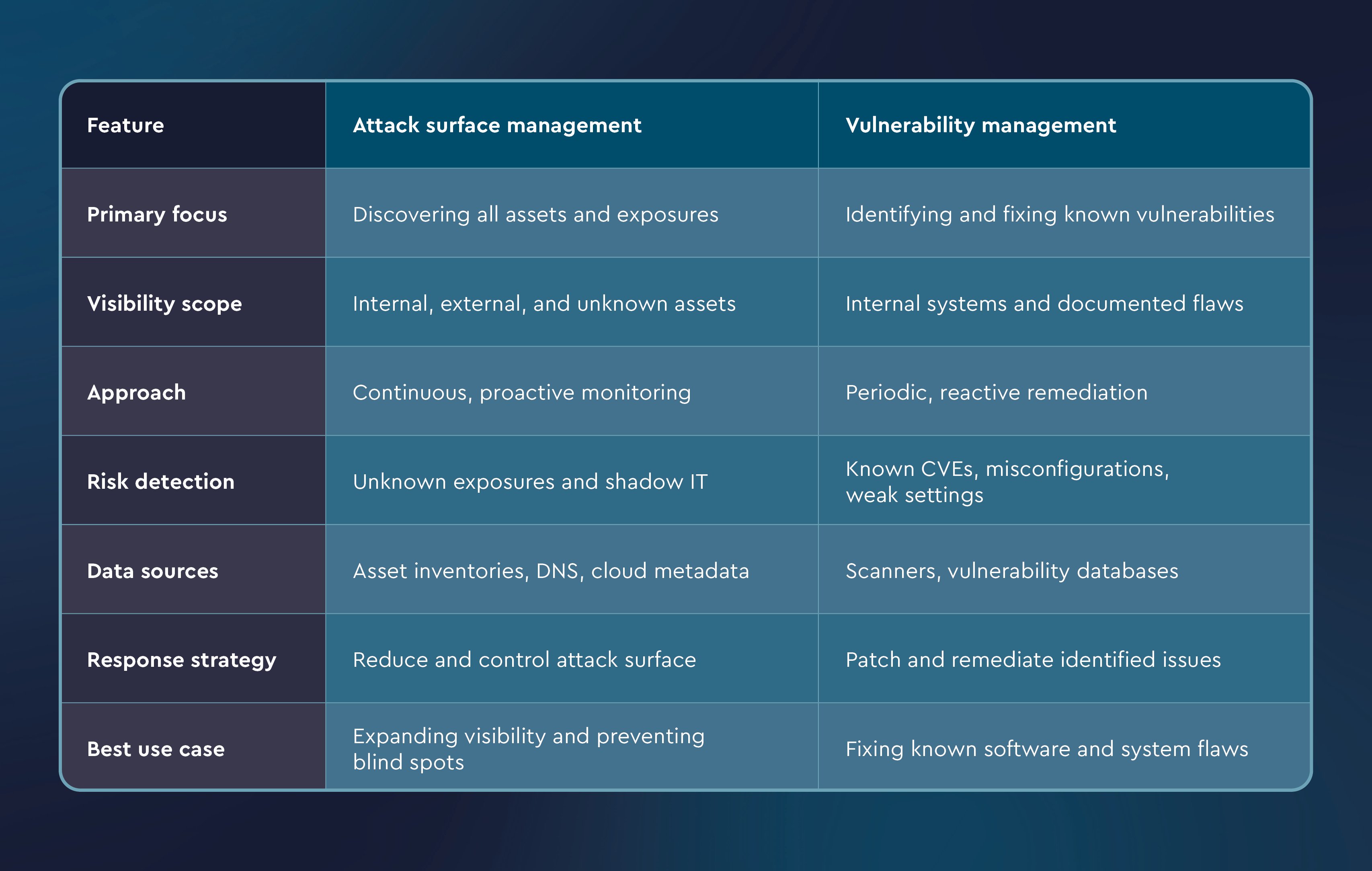
Attack surface management is the continuous process of discovering, classifying, and monitoring all assets, whether on-premises, in the cloud, or in shadow IT, to identify potential exposures. This includes known assets such as servers and endpoints, and unknown or unmanaged assets such as forgotten subdomains, open ports, and orphaned cloud services.
Attack surface management works by constantly scanning for new assets, misconfigurations, and vulnerabilities across the organization’s digital footprint. This real-time visibility helps security teams reduce the overall attack surface by eliminating unnecessary exposures before they can be exploited.
Vulnerability management is the process of identifying, prioritizing, remediating, and reporting on known security weaknesses in software, systems, and configurations. It primarily addresses vulnerabilities cataloged in public databases such as Common Vulnerabilities and Exposures (CVEs) or discovered via security scans.
Vulnerability management typically follows a defined cycle: scan for vulnerabilities, evaluate risk, apply patches or configuration changes, mitigate risk through equipment/software retirement or segmentation, and verify remediation. The goal is to reduce the risk of exploitation by staying current with security updates and best practices.
Attack surface management and vulnerability management serve distinct but complementary roles in cybersecurity. Attack surface management continuously uncovers the full scope of assets, especially those unknown or unmanaged by IT and security teams. Once identified, vulnerability management tools evaluate these assets for known weaknesses and initiate remediation workflows.
For example, attack surface management might detect an unsecured cloud database. On its own, this is an exposure. Vulnerability management then scans the database for outdated software or misconfigurations, ensuring the risk is fully addressed.
By combining these approaches, organizations gain:
Together, attack surface management and vulnerability management help close security gaps, reduce risk, and improve operational efficiency across MSP and IT teams.
Focusing on vulnerability management alone leaves security teams blind to risks they have yet to discover. Untracked assets, unmanaged endpoints, and abandoned cloud services expand the attack surface and create entry points for attackers. Vulnerability management tools can’t secure what they don’t know exists.
Meanwhile, attackers are constantly scanning for exposed systems. Without attack surface management, organizations risk falling behind and may only discover exposures after a breach.
Integrating attack surface management with vulnerability management provides:
Using both strategies together equips organizations with the visibility and control needed to reduce risk and maintain a resilient security posture in an ever-changing threat landscape.
ConnectWise delivers comprehensive cybersecurity solutions that unify visibility, detection, and remediation, empowering MSPs and IT professionals to stay ahead of evolving threats. Organizations can leverage both attack surface management and vulnerability management capabilities in a single, streamlined ecosystem.
With ConnectWise cybersecurity solutions, users gain:
ConnectWise also offers powerful vulnerability management capabilities, including:
Together, these solutions close the gap between discovery and resolution, giving MSPs the tools to protect every asset, reduce dwell time, and deliver more robust, scalable cybersecurity services.
Attack surface management identifies and monitors all digital assets, including unknown or shadow IT, while vulnerability management focuses on known flaws, such as CVEs and misconfigurations, and remediates them. Attack surface management is proactive and continuous, whereas vulnerability management is reactive and cyclical.
Attack surface management helps uncover hidden exposures in real time, including unmanaged assets, open ports, and orphaned cloud services. This expanded visibility reduces blind spots and helps prevent attacks before they occur.
Yes. Attack surface management finds and classifies all assets and exposures, while vulnerability management evaluates those assets for known vulnerabilities and triggers remediation workflows. Together, they create a more resilient and complete cybersecurity defense.
No, vulnerability management can only address known issues on known systems. Without attack surface management, unknown or unmanaged assets can go unmonitored, leaving security gaps that attackers can exploit.
ConnectWise offers unified solutions that combine real-time asset discovery, continuous monitoring, vulnerability scanning, automated patch management, and centralized reporting. This integrated approach helps MSPs and IT teams reduce risk and streamline operations.
Attack surface management may detect unsecured cloud storage, forgotten subdomains, exposed APIs, or shadow IT systems that are not monitored by internal security tools.
Vulnerability management tools include scanners, CVE databases, patch management solutions, and configuration analysis systems. ConnectWise integrates these tools to deliver prioritized, automated remediation at scale.