Ransomware is a pervasive, evolving menace that can incapacitate entire organizations within hours. For managed service providers (MSPs), the stakes are even higher. A successful ransomware breach into an MSP’s environment doesn’t stop at one entry point; it cascades across all connected client systems, expanding the attack vector and amplifying the damage exponentially.
The threat is especially severe for small and midsized (SMB) businesses. According to Verizon’s 2025 Data Breach Investigations Report, ransomware was involved in 88% of breaches in SMBs, compared to 39% in larger organizations. The disparity highlights how disproportionately vulnerable smaller operations are, and why their service providers must lead with resilience.
By focusing on proven ransomware backup strategy techniques, you can strengthen your defensive layers and ensure that data recovery is always within reach, even in the face of sophisticated, targeted attacks.
In this blog, we’ll explore the critical components of ransomware backup protection, offer insights into emerging technologies, and provide actionable steps to help you secure your organization’s most valuable digital assets.
Ransomware is a type of malicious software that encrypts an organization’s files, rendering them inaccessible until a ransom is paid, usually in cryptocurrency. But today’s ransomware is more sophisticated and aggressive than ever. Attackers aren’t just locking data; they’re exfiltrating sensitive information and threatening to leak it if demands aren’t met, a tactic known as double extortion.
These attacks are often automated, fast-moving, and timed for maximum disruption, such as during holidays, weekends, or peak business hours. Once inside, ransomware can silently spread laterally, targeting connected systems and backup infrastructure.
While strong security practices and endpoint protections are essential, it’s not possible to entirely prevent ransomware attacks. That’s why having a ransomware-resilient backup strategy is critical. When prevention fails, rapid recovery becomes your last line of defense, minimizing downtime, data loss, and operational disruption.
Many organizations still rely on legacy backup tools that, while suitable for hardware failure or accidental deletion, fall short against modern ransomware threats. These traditional solutions were not designed with active, intelligent threats in mind, and hackers know it.
Organizations hit by ransomware often discover too late that their backups have either been encrypted, deleted, or never tested for recovery. This is especially dangerous for MSPs, where a compromised backup infrastructure can affect every downstream customer. In enterprises, the fallout can include regulatory penalties, reputational damage, and operational chaos.
Modern ransomware demands a modern approach to backup. To truly protect data, your backup environment must be isolated, intelligent, and resilient.
To protect your organization and clients from ransomware, you need more than just backup copies. You need a tamper-proof backup architecture. The goal isn’t just to store data but to ensure data integrity, rapid recovery, and immunity from compromise, even under active attack conditions.
Below are the six foundational elements of an effective ransomware-resilient backup strategy.
1. Implement the 3-2-1-1-0 rule
A modern evolution of the classic 3-2-1 rule, the 3-2-1-1-0 strategy calls for:
This structure ensures that even if production systems and one backup tier are compromised, a clean and secure backup remains available.
2. Immutable and air-gapped backups
One of the most critical defense mechanisms is immutability, which is the ability to prevent data from being changed or deleted once written. Air-gapped backups go a step further by physically or logically isolating backup data from the network.
Pro tip:
x360Recover’s AirGap® technology delivers a powerful line of defense by automatically creating immutable snapshots of backup data. These snapshots are:
This feature is particularly crucial for MSPs managing multiple tenants, as well as enterprise environments where backup infrastructure is a high-value target. Even if ransomware breaches a backup environment, AirGap ensures that clean, recent copies of your data remain fully intact and recoverable.
3. Automated and frequent backups
Ransomware moves quickly, so your backups must keep up. Implement automated, frequent backups to reduce data loss (RPO) and ensure that recovery points are as recent as possible.
4. Regular backup testing
Even the most sophisticated backup is useless if it fails during a crisis. Conduct routine recovery drills to validate your processes, test the speed of restore operations (RTO), and confirm that backup data hasn’t been corrupted.
5. Strict access controls and MFA
Limit access to backup systems through role-based permissions and enforce multi-factor authentication (MFA). The fewer people with administrative privileges, the smaller the attack surface.
6. Real-time monitoring and anomaly detection
Integrate backup systems with security information and event management (SIEM) platforms or endpoint monitoring tools to detect signs of compromise, such as spikes in file changes, deletions, or unauthorized login attempts.
By adhering to these principles and leveraging technologies such as x360Recover’s AirGap, you can build a ransomware backup strategy that does more than just check compliance boxes. It actively safeguards your operations, your clients, and your reputation.
As ransomware attacks become more targeted and sophisticated, backup solutions must evolve beyond static storage and scheduled snapshots. Today, the most resilient backup strategies are powered by intelligent technologies that proactively detect threats, isolate risk, and ensure rapid, precise recovery.
Below are the five most impactful innovations enhancing ransomware backup protection.
1. AI and machine learning for anomaly detection
Artificial intelligence (AI) and machine learning (ML) are transforming how organizations monitor and protect their data. Integrated into modern backup systems, these technologies can:
This proactive defense mechanism significantly shortens the time between compromise and containment, reducing data loss and downtime.
2. Zero trust architecture in backup environments
Zero trust principles, “never trust, always verify,” are increasingly being applied to backup strategies. In this model:
Zero trust backup infrastructure is especially valuable for multi-tenant environments, remote workforces, and hybrid IT ecosystems where perimeter-based security is no longer sufficient.
3. Immutable storage with policy-based retention
Immutable storage prevents any modification or deletion of backup data during a defined retention period. Solutions such as x360Recover incorporate AirGap snapshots with policy-driven immutability, ensuring that recovery points remain:
This provides peace of mind for organizations subject to compliance frameworks such as HIPAA, GDPR, or SOX.
4. Automated backup verification
Modern solutions go beyond just completing a backup. They verify that the data is usable and complete. Through automated boot verification, screenshots, and checksum validation, systems such as x360Recover can confirm:
This drastically reduces the chance of discovering broken backups only after an attack has occurred.
5. SIEM and backup integration
SIEM solutions centralize logs and alerts across an organization’s infrastructure. When backup systems are integrated into SIEM:
This integration empowers SOC teams to treat backup systems as active assets in the cybersecurity ecosystem, not just passive data stores.
Combining intelligent automation with resilient storage design creates a multi-layered defense that’s far more effective than legacy approaches. Whether you’re a security-conscious enterprise or a proactive MSP, investing in these advanced technologies gives you a significant advantage in the fight against ransomware.
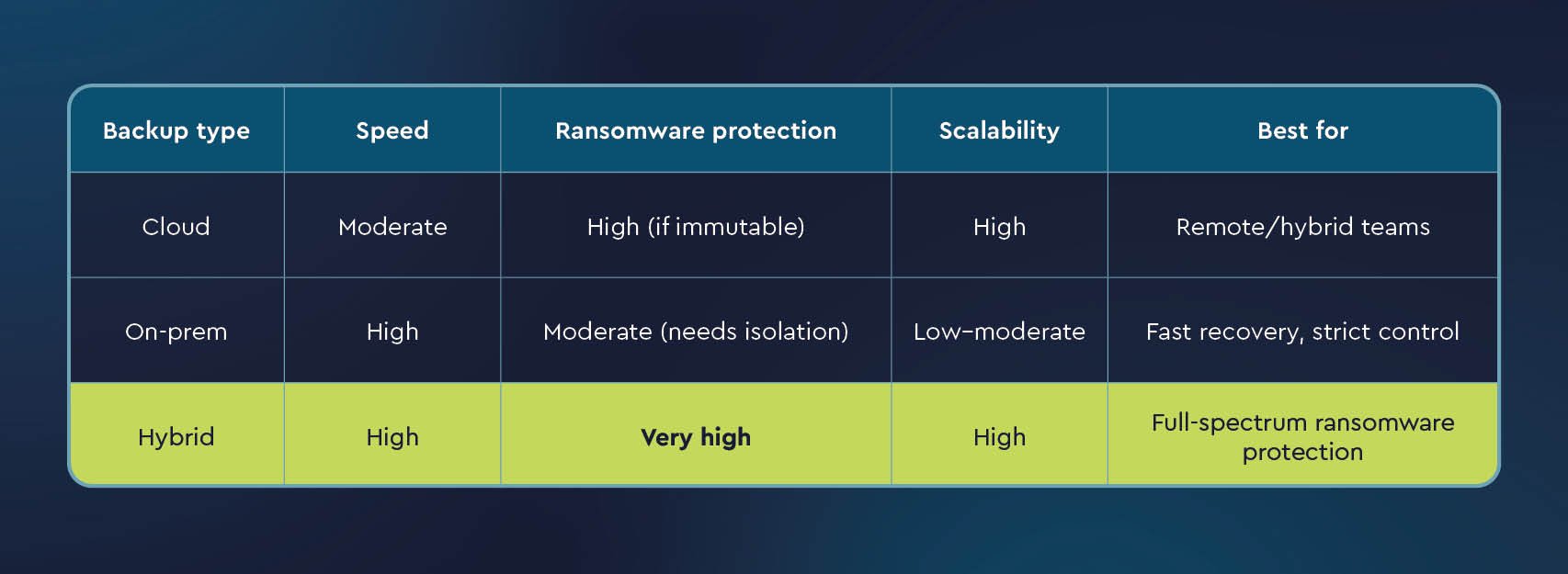
When it comes to ransomware protection, the type of backup infrastructure you deploy can dramatically affect your ability to recover quickly and securely. Not all backup environments are equally resilient to ransomware threats, especially as attackers increasingly target backup systems themselves. Choosing between cloud, on-premises, and hybrid backup solutions requires balancing speed, security, and recoverability.
Here’s how each option stacks up for ransomware backup protection.
On-premises backups involve storing backup data on physical appliances or local servers within your infrastructure. While these offer high-speed recovery, they are also more vulnerable to ransomware if not properly segmented.
Ransomware backup advantages
Potential drawbacks
Ideal for: Organizations with tight compliance needs or those that require ultra-fast local recovery.
Cloud backups store your data in off-site data centers managed by a service provider. This off-site storage is inherently beneficial for ransomware resilience, especially if the solution supports immutable backups and versioning.
Ransomware backup advantages
Potential drawbacks
Ideal for: Businesses with distributed teams or those prioritizing off-site protection and operational agility.
Hybrid backups combine the speed of on-premises recovery with the resilience of off-site cloud storage. This dual approach offers the most robust defense against ransomware, ensuring multiple isolated recovery points.
Ransomware backup advantages
Considerations
Ideal for: MSPs and enterprises seeking a ransomware-resilient backup strategy with both performance and security.
Download our eBook, 2025 Hybrid Cloud Backup Essentials, to learn more about how hybrid cloud backups offer critical business continuity and disaster recovery (BCDR) capabilities.
Choosing a backup provider is more than just picking storage. It’s selecting a ransomware recovery partner. Your vendor should offer technology that goes beyond basic data protection, delivering built-in ransomware resilience, immutable storage, and rapid recovery capabilities tailored to your environment.
Look for solutions that:
For both MSPs and enterprise IT teams, aligning with the right provider ensures your backup strategy can withstand evolving ransomware threats and regulatory demands.
Download our BCDR Buyer’s Guide, which includes a free BCDR evaluation checklist to analyze and compare your options.
Modern attacks are designed to target and destroy traditional backups. To stay ahead, organizations need immutable, air-gapped, and instantly recoverable backups that can restore operations without paying a ransom or suffering extended downtime.
Whether you’re an MSP safeguarding customer environments or an enterprise IT leader protecting critical systems, x360Recover offers a purpose-built solution that delivers:
To get started, learn more about x360Recover and discover how it can help you build a ransomware-proof backup and disaster recovery plan that’s ready for anything.
Yes, many modern ransomware variants are designed to locate and encrypt connected backup storage. That’s why implementing immutable backups and air-gapped storage is critical to ensure backups remain recoverable.
A ransomware-proof backup solution includes immutable storage, off-site replication, automated backup verification, and limited administrative access to ensure data cannot be modified or deleted during an attack.
For ransomware resilience, backups should be performed frequently and automatically, often hourly or continuously, depending on the criticality of the data and the business’s recovery time objectives (RTO).
AirGap®, featured in x360Recover, creates immutable, hidden snapshots of your backup data that cannot be accessed or deleted, even if the primary backup environment is compromised. This ensures reliable recovery after a ransomware attack.
Cloud backups offer off-site isolation, making them inherently more resistant to local ransomware attacks. However, the safest approach is a hybrid strategy that combines on-prem speed with cloud immutability.
Data backup ensures your files are stored safely, while disaster recovery (DR) focuses on how quickly and completely you can restore systems after an event. For ransomware, having a plan that combines both is essential.
Perform regular backup recovery tests to validate that data can be restored quickly and cleanly. Tools such as automated verification, boot testing, and screenshot confirmations help ensure backups work when they’re needed most.
This updated rule recommends Three copies of your data, on two different media, with one off-site copy, one copy being immutable or air-gapped, and zero errors during backup verification. The final zero emphasizes the importance of regularly testing your backups to ensure that no errors exist and that data can be restored reliably when needed. This rule is quickly becoming the new gold standard for ransomware-resilient backup strategies.