Welcome to the May 2025 edition of the ConnectWise Cyber Research Unit™ (CRU) Monthly Threat Brief. This report provides a comprehensive look at the most significant cybersecurity developments impacting the MSP and SMB landscape. We break down the month’s top stories, critical vulnerabilities, and prevalent malware families to help you stay informed and prepared in an evolving threat environment.
The EMERALDWHALE campaign demonstrates how attackers are exploiting a surprisingly common oversight: exposed Git configuration files on public-facing websites. By scanning 500 million IP addresses, threat actors identified 28,000 compromised repositories and stole over 15,000 cloud credentials, all using basic automated tools. The attack targets misconfigured web servers that accidentally expose .git/config files and Laravel .env files containing hardcoded API keys and authentication tokens. While technically simple, this approach proves highly effective because it exploits widespread misconfigurations in development environments.
The stolen credentials aren’t being used for sophisticated attacks. Instead, they’re primarily sold on underground markets (individual cloud credentials can fetch hundreds of dollars) or used to power phishing and spam operations. What makes this particularly concerning is the low barrier to entry. Attackers use commodity scanning tools and open-source credential extraction utilities, making this attack pattern easily replicable by less sophisticated threat actors.
What this means for MSPs
This is a revenue opportunity disguised as a security issue. Most of your SMB clients with any development work, whether internal teams or contracted developers, are likely vulnerable to this exact attack. The fix isn’t complex, but it requires someone who understands both web server configuration and development workflows. Start offering “development security audits” that scan for exposed Git files, review CI/CD pipelines for credential exposure, and implement proper secret management practices. Position this as essential infrastructure hygiene, not an optional security add-on.
The detection angle is equally valuable. Unusual cloud API usage patterns from unexpected IP ranges often indicate compromised credentials from attacks like this. Adding this monitoring capability to your security stack gives you another way to catch breaches early and demonstrate ongoing value to clients.
The ConnectWise CRU has identified a sophisticated malware campaign using PDFast, a fake PDF converter that appears legitimate but delivers multi-stage malware. The attack begins when users download PDFast.exe through malvertising or SEO poisoning, then establishes persistence via MSI installers and scheduled tasks. What makes this particularly dangerous is the extended dormancy period. The malware can sit quietly for 1-21 days (averaging 10 days) before activating its command-and-control functions, giving it time to evade initial security scans.
Once activated, PDFast deploys the Amber Albatross malware, which conducts extensive system reconnaissance, collects antivirus and firewall information, and establishes encrypted communication channels. The malware uses sophisticated evasion techniques, including CDN rotation for C2 traffic and UserAgent header manipulation, to prevent security researchers from analyzing the payload URLs. This represents a concerning evolution in fake converter campaigns, combining professional presentation with advanced persistence mechanisms.
What this means for MSPs
Hunt for this immediately. PDFast infections are actively spreading across MSP client bases with no specific industry targeting. Everyone is vulnerable. Start searching for PDFast.exe, upd.exe, and scheduled tasks named PDFast_updater_* across all managed endpoints. The 10-day average window between infection and C2 activation gives you a detection opportunity, but only if you’re actively looking.
This campaign highlights a critical gap in client education and security controls. Free online converters are becoming the new browser toolbar. Seemingly innocent tools that deliver sophisticated malware. Consider implementing application safelisting policies and adding “fake converter awareness” to your security training programs. The professional appearance of these sites makes them particularly effective at fooling end users who think they’re being security-conscious by avoiding obviously sketchy downloads.
StealC 2.0 represents a significant evolution in information-stealing malware, with Zscaler’s analysis revealing substantial technical improvements since its March 2025 release. Originally a basic $200/month tool from 2023, the updated version now features multiple payload delivery methods (EXE, MSI, PowerShell), RC4 encryption for communications, 64-bit compilation, and dynamic API resolution—all designed to evade modern security controls. The most concerning addition is an embedded builder tool that lets attackers easily customize StealC builds for specific environments or data types, essentially democratizing advanced malware customization.
Recent incidents show StealC 2.0 being deployed as a secondary payload by the Amadey loader, indicating integration into multi-stage attack chains rather than standalone infections. This suggests attackers are building more sophisticated penetration paths designed to bypass layered security defenses. The malware targets browsers, cryptocurrency wallets, and authentication systems, with enhanced screenshot capabilities across multiple monitors for expanded data collection.
What this means for MSPs
This threat requires a layered detection approach beyond traditional signatures. StealC 2.0’s RC4 encryption and builder tool creates unique, encrypted payloads that benefit from behavioral monitoring alongside signature-based detection. Focus on identifying unusual PowerShell/MSI execution chains and encrypted C2 traffic patterns to complement existing security controls. The multi-stage deployment model means early detection of the Amadey loader becomes critical, since each StealC 2.0 build can be customized for specific environments, making static IOCs less reliable for detection.
The ransomware landscape has undergone dramatic shifts in Q1 2025, with RansomHub’s unexpected collapse on April 1 causing affiliate migration to platforms such as Qilin and the emergence of sophisticated new threats, including HellCat. Unit 42’s analysis shows a 149% year-over-year increase in US ransomware attacks, with 32 distinct variants active in January alone. What makes these developments particularly dangerous is the technical evolution: HellCat employs reflective code loading to execute malware directly in memory, bypassing traditional file-based detection, while Qilin affiliates are deploying advanced adversary-in-the-middle phishing kits specifically targeting MSP environments through fake ScreenConnect® alerts.
The threat landscape has expanded beyond traditional email vectors to collaboration platforms such as Slack and Jira, with AI-enabled attacks showing a 4,151% increase post-ChatGPT. These aren’t just better phishing emails. Attackers are using AI voice cloning to bypass biometric authentication and generating convincing internal messages that sidestep email security entirely. The shift toward exfiltration-focused attacks over encryption represents a strategic optimization that reduces detection windows while maintaining extortion effectiveness.
What this means for MSPs
These evolving threats require enhanced detection capabilities focused on memory-based attacks and expanded attack surfaces. HellCat’s reflective loading techniques demand monitoring for memory manipulation, API calls, and process injection, which are capabilities that complement traditional file-based detection. The targeting of collaboration platforms means Slack, Teams, and Jira now require the same security attention as email systems, with contextual authentication and behavior monitoring becoming essential. The Qilin campaign’s specific focus on ScreenConnect highlights the need for hardened remote management with IP safelisting, session monitoring, and jump-box architectures to protect MSP operations.
Despite widespread industry hype about “AI-powered cyberattacks,” the reality is more nuanced. Many reported AI threats are simply rebranded automation, while genuine AI integration is occurring primarily in social engineering. It’s been found that vendors frequently mislabel routine automation as “AI-powered” without evidence of actual machine learning deployment. The clearest real-world AI integration is in enhanced phishing campaigns with grammatically correct, contextually appropriate messages, achieving 19% click-through rates versus 8% for traditional phishing and conversation hijacking, where attackers analyze email patterns to insert malicious content into legitimate threads.
Most other widely reported AI threats remain theoretical. The 2025 Verizon DBIR found that 94% of attacks still rely on known vulnerabilities with “no conclusive evidence of AI-discovered zero-days in the wild.” Claims about AI-enhanced malware obfuscation, fully autonomous attack platforms, and undetectable AI malware lack concrete supporting evidence, with behavior-based detection remaining effective against current threats.
What this means for MSPs
Focus on strengthening email security fundamentals rather than chasing specialized “anti-AI” solutions. The primary genuine AI threat is sophisticated social engineering that eliminates traditional phishing indicators, such as poor grammar and obvious red flags. Shift your email security to behavioral pattern analysis, implement conversation thread monitoring to detect hijacking attempts, and update security awareness training to develop holistic security thinking rather than teaching users to spot technical indicators that no longer reliably identify threats.
Sophisticated fileless malware campaigns are increasingly targeting MSP remote management tools, executing entirely in system memory using "Living Off the Land" (LOTL) techniques that leverage legitimate Windows utilities, such as PowerShell and WMI.
These attacks begin with phishing emails directing MSP staff to compromised websites that exploit browser vulnerabilities to execute scripts directly in RAM, bypassing traditional signature-based antivirus detection. Tools such as SNOWLIGHT are being deployed to drop VShell payloads that provide remote control capabilities, with attackers specifically targeting MSP infrastructure because it provides privileged access to numerous client networks simultaneously.
The technical sophistication creates substantial detection challenges since attacks leave minimal disk artifacts, with most evidence existing only in volatile memory that disappears on reboot. This complicates forensic investigation and requires advanced memory forensics capabilities. For MSPs, a single compromise can cascade into hundreds of downstream client environments, creating operational challenges in distinguishing legitimate administrative activities from malicious actions using the same tools.
What this means for MSPs
Your security stack needs to evolve to address memory-based threats that traditional endpoint protection can't detect. Consider implementing behavioral detection capabilities, comprehensive PowerShell logging, and network segmentation between management and client environments. The targeting of MSP infrastructure specifically creates a multiplier effect where single compromises can impact multiple clients, making privileged access management and zero trust principles increasingly important for remote management tools. Focus on threat hunting capabilities that can identify anomalous behavior even when attackers use legitimate administrative utilities.
DragonForce ransomware actors successfully compromised an MSP by chaining three critical SimpleHelp RMM vulnerabilities. They then leveraged the trusted RMM infrastructure to deploy ransomware across multiple client networks in a sophisticated supply chain attack. The attack sequence began with CVE-2024-57727 (path traversal vulnerabilities) allowing unauthenticated file extraction, escalated through CVE-2024-57726 (privilege escalation bypassing authorization checks), and culminated with CVE-2024-57728 (arbitrary file upload via zip slip attacks). Once inside the MSP's SimpleHelp instance, attackers conducted reconnaissance across client environments and distributed malicious SimpleHelp installers through the legitimate RMM platform.
The attack demonstrates how trusted MSP infrastructure can become a force multiplier, enabling threat actors to impact hundreds of clients through a single compromise. Detection capabilities varied significantly. Clients with advanced endpoint protection, such as Sophos MDR, successfully blocked the ransomware through behavioral analysis, while those lacking comprehensive security suffered both encryption and data exfiltration. This highlights the critical dependency on layered security controls across MSP client environments.
What this means for MSPs
Immediately patch SimpleHelp installations to versions 5.5.8, 5.4.10, or 5.3.9+ and audit for "Remote Access.exe" files with "SimpleHelp LTD" vendor signatures that could indicate compromise. This attack pattern represents the maturation of supply chain targeting, where RMM platforms require enterprise-grade security controls and zero-trust architectures. The stark difference in outcomes between protected and unprotected clients demonstrates that comprehensive endpoint protection across your entire client base isn't optional; it's essential for business continuity. Implement enhanced monitoring for unusual RMM activity patterns and establish network segmentation between client environments to prevent future cascade compromises.
CVE-2024-55592
CVE-2024-55592 is an incorrect authorization vulnerability (CWE-863) affecting Fortinet FortiSIEM across multiple versions from 6.2.0 through 7.2.5. The flaw allows authenticated attackers to perform unauthorized operations on incidents via crafted requests, essentially enabling privilege escalation within FortiSIEM's incident management system. While the vulnerability requires authentication, it represents a significant authorization bypass that could allow users to manipulate security incidents beyond their intended access levels.
FortiSIEM products have become high-priority targets for threat actors throughout 2025, though specific exploitation of CVE-2024-55592 in May 2025 was not documented in available threat intelligence. The broader FortiSIEM platform has been heavily targeted with critical vulnerabilities, such as CVE-2024-23108 and CVE-2024-23109 (both CVSS 10.0) allowing remote unauthenticated command execution. Recent threat activity shows ransomware actors, including Mora_001, actively exploiting Fortinet vulnerabilities, with CISA adding multiple Fortinet flaws to the KEV catalog due to active ransomware campaigns. Current exploitation trends show 28.3% of vulnerabilities being weaponized within 24 hours of disclosure, making rapid patching critical for FortiSIEM deployments.
CVE-2025-24472
CVE-2025-24472 is an authentication bypass vulnerability affecting Fortinet FortiOS versions 7.0.0-7.0.16 and FortiProxy versions 7.0.0-7.0.19 and 7.2.0-7.2.12, allowing remote attackers to gain super-admin privileges via crafted CSF proxy requests. CISA added the vulnerability to its KEV catalog earlier in 2025 following evidence of active ransomware exploitation. The vulnerability carries a CVSS 8.1 HIGH score and enables attackers to bypass authentication controls without requiring initial access.
The most significant recent threat activity involves the Mora_001 ransomware group, which has been actively exploiting both CVE-2025-24472 and CVE-2024-55591 since January 2025 to deploy SuperBlack ransomware. Forescout Research identified this group as having ties to LockBit operations, with campaigns targeting exposed FortiGate firewalls between late January and March 2025. While exploitation activity peaked in Q1 2025, with vulnerabilities being weaponized within 24 hours of disclosure at unprecedented rates, current threat intelligence suggests continued but decreased activity as defenders implement patches and security controls.
CVE-2025-30406
CVE-2025-30406 is a critical deserialization vulnerability affecting Gladinet CentreStack through version 16.1.10296.56315 and Triofox up to version 16.4.10317.56372, caused by hardcoded cryptographic keys in the ASP.NET ViewState mechanism. The vulnerability carries a CVSS 9.0 score and enables remote code execution without authentication beyond the knowledge of the default machineKey values. CISA added the vulnerability to its KEV catalog on April 8, 2025, following evidence of active zero-day exploitation dating back to March 2025.
Recent threat intelligence reveals sophisticated and persistent post-exploitation tactics by attackers who have compromised multiple organizations. Following initial exploitation, threat actors deploy encoded PowerShell scripts to download malicious DLLs, install MeshCentral for persistent remote access, and conduct extensive enumeration using commands such as echo, ping, net, and nltest.
This section leverages the Diamond Model of Intrusion Analysis to structure the examination of recent malware activity, providing a clear analytical framework that links adversary, capabilities, infrastructure, and victimology. By applying the Diamond Model, we can better contextualize malicious behavior, identify patterns across campaigns, and highlight the relationships between threat actors, tools, and targeted entities.
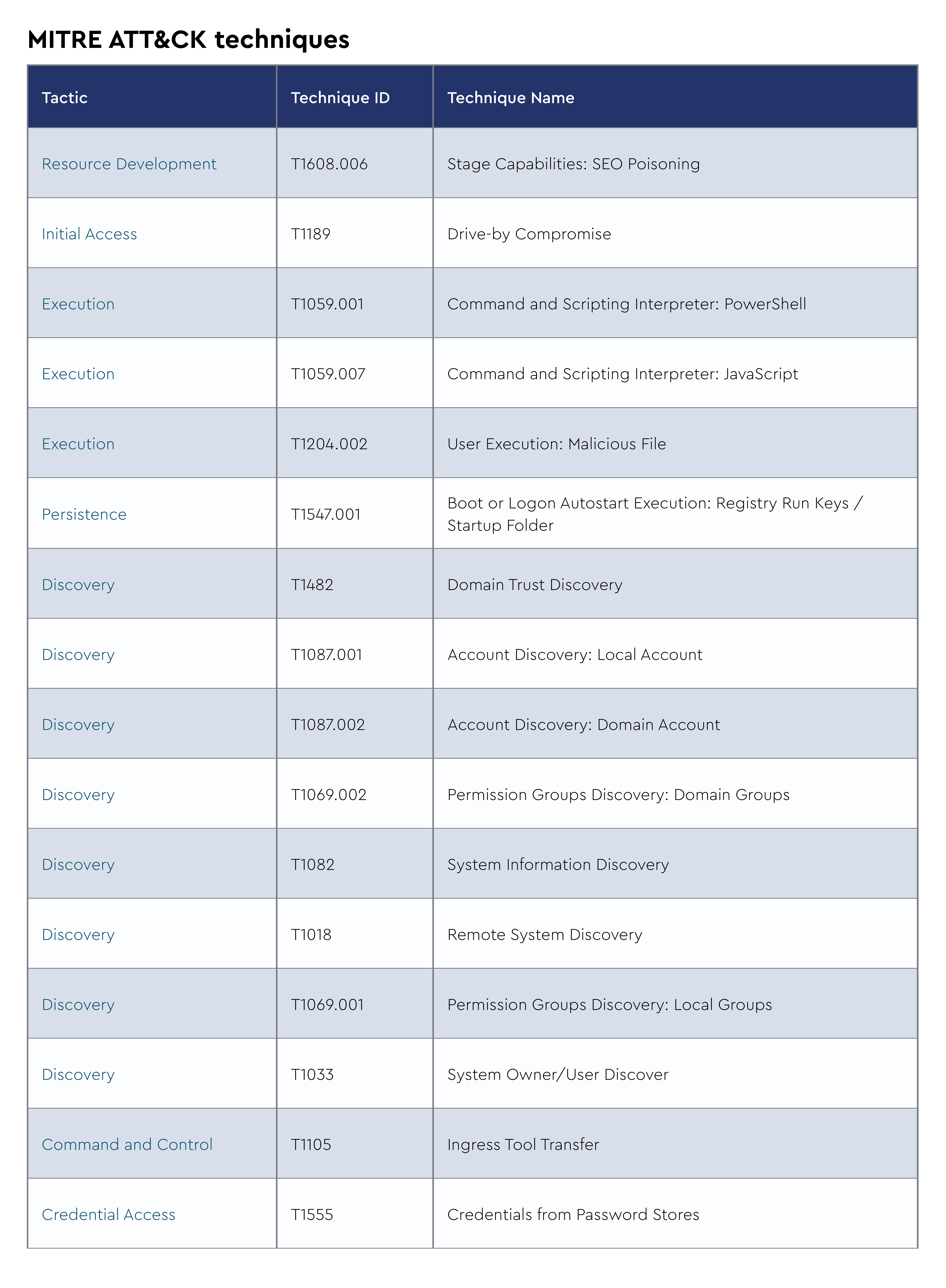
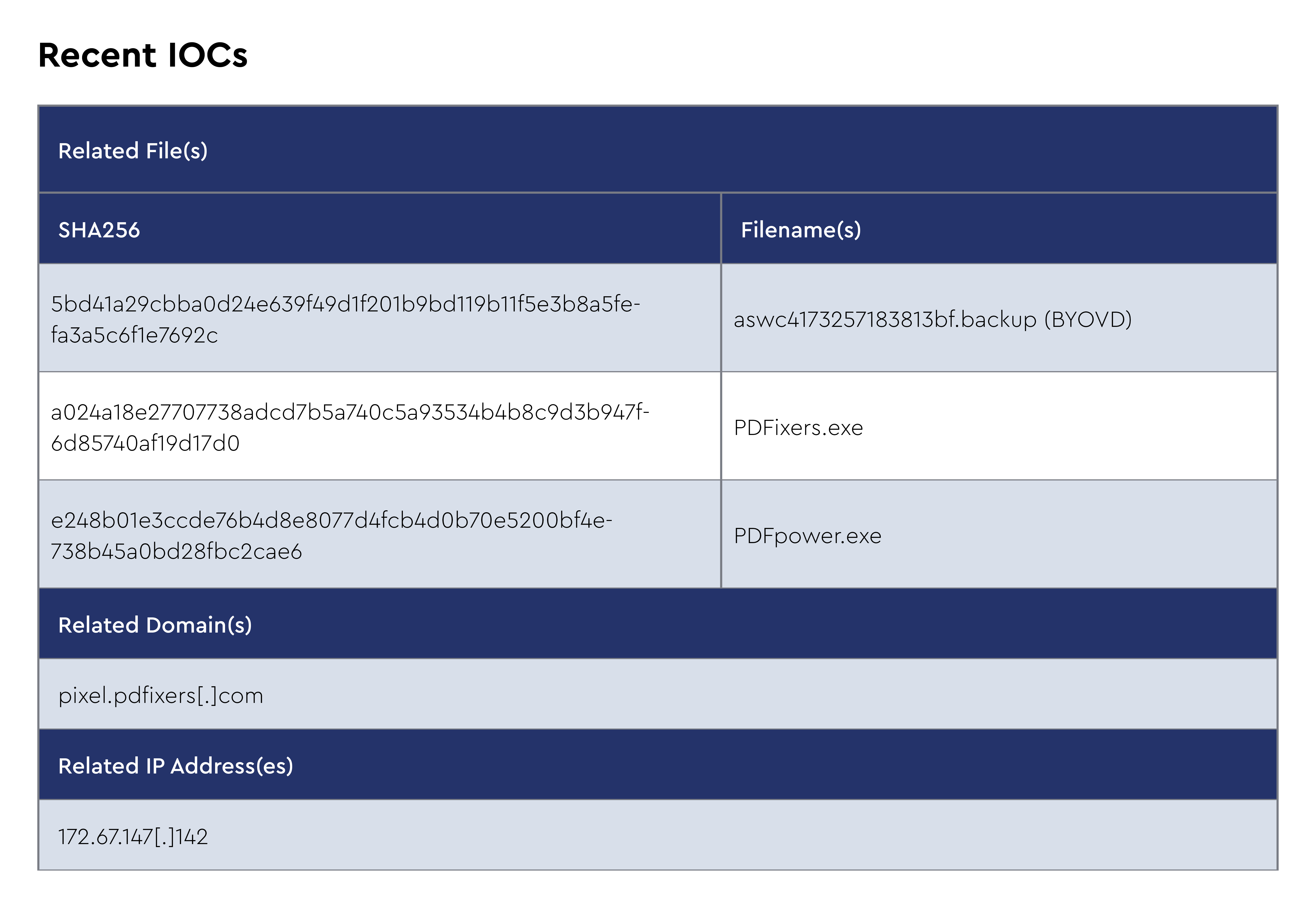
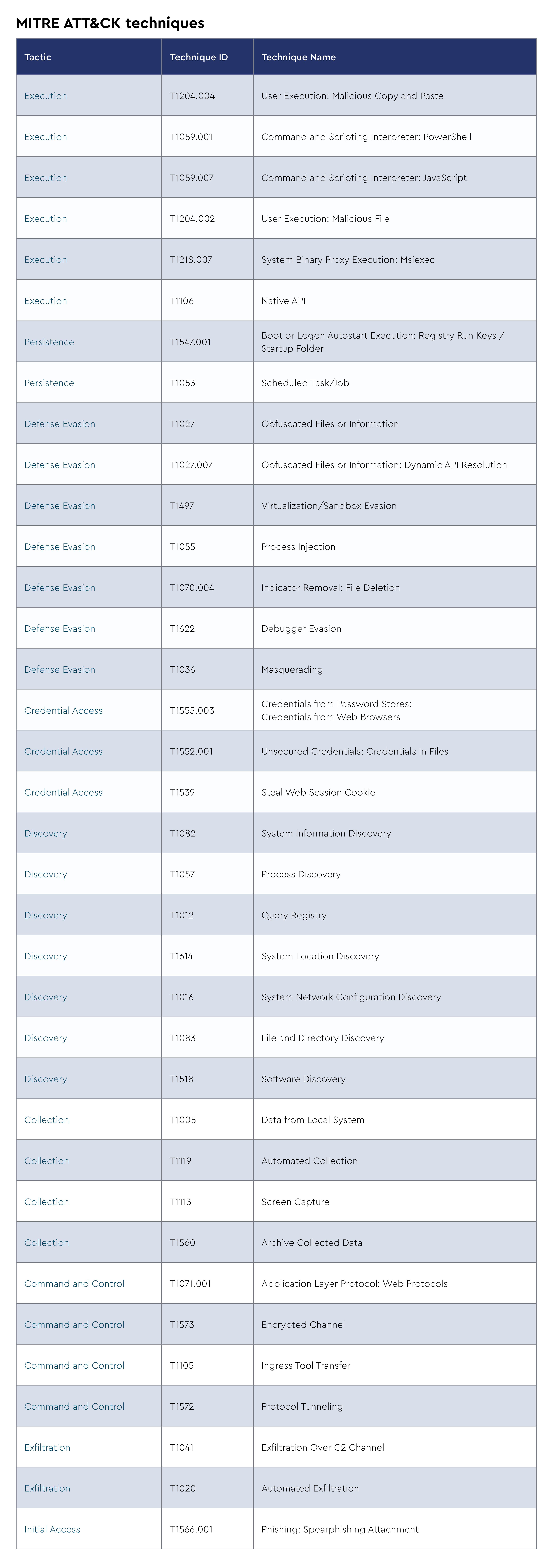
Akira continued operating as a dominant ransomware-as-a-service (RaaS) player in May 2025, maintaining its aggressive targeting of small-to-medium enterprises across North America, Europe, and Australia. The group has maintained consistent operations since its March 2023 emergence, leveraging double-extortion tactics with data exfiltration preceding encryption. Recent technical analysis shows Akira samples active in the wild use ChaCha algorithm for file encryption and employ Windows restart manager APIs to terminate processes for file access. The ransomware continues deploying both its original C++ variant (creating .akira extensions) and the Rust-based Megazord variant (.powerranges extensions), with operators switching between variants based on target environment specifics.
In May 2025, the CRU observed Akira operators using fake PDF converter applications distributed via malvertising, SEO poisoning, and social engineering techniques for initial access. These malicious converters serve as droppers for the Akira payload while appearing legitimate to users searching for PDF conversion tools through compromised search results and malicious advertisements. Additionally, threat actors have adopted “bring your own vulnerable driver” (BYOVD) tactics for EDR evasion, specifically exploiting a vulnerable version of AVG Anti-Rootkit to disable endpoint security solutions before deploying the ransomware.
Aliases
Infrastructure
Victimology
Capabilities
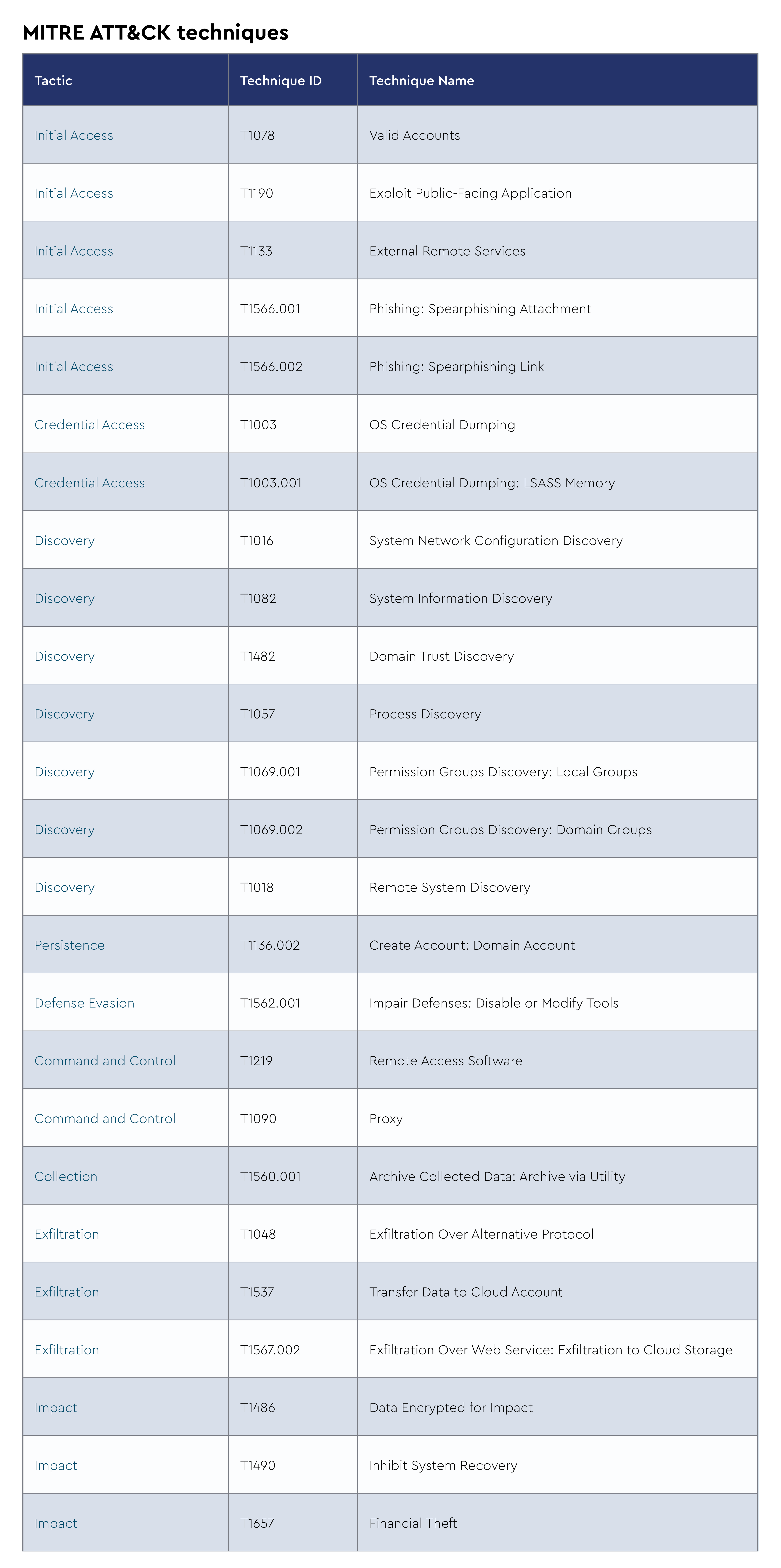
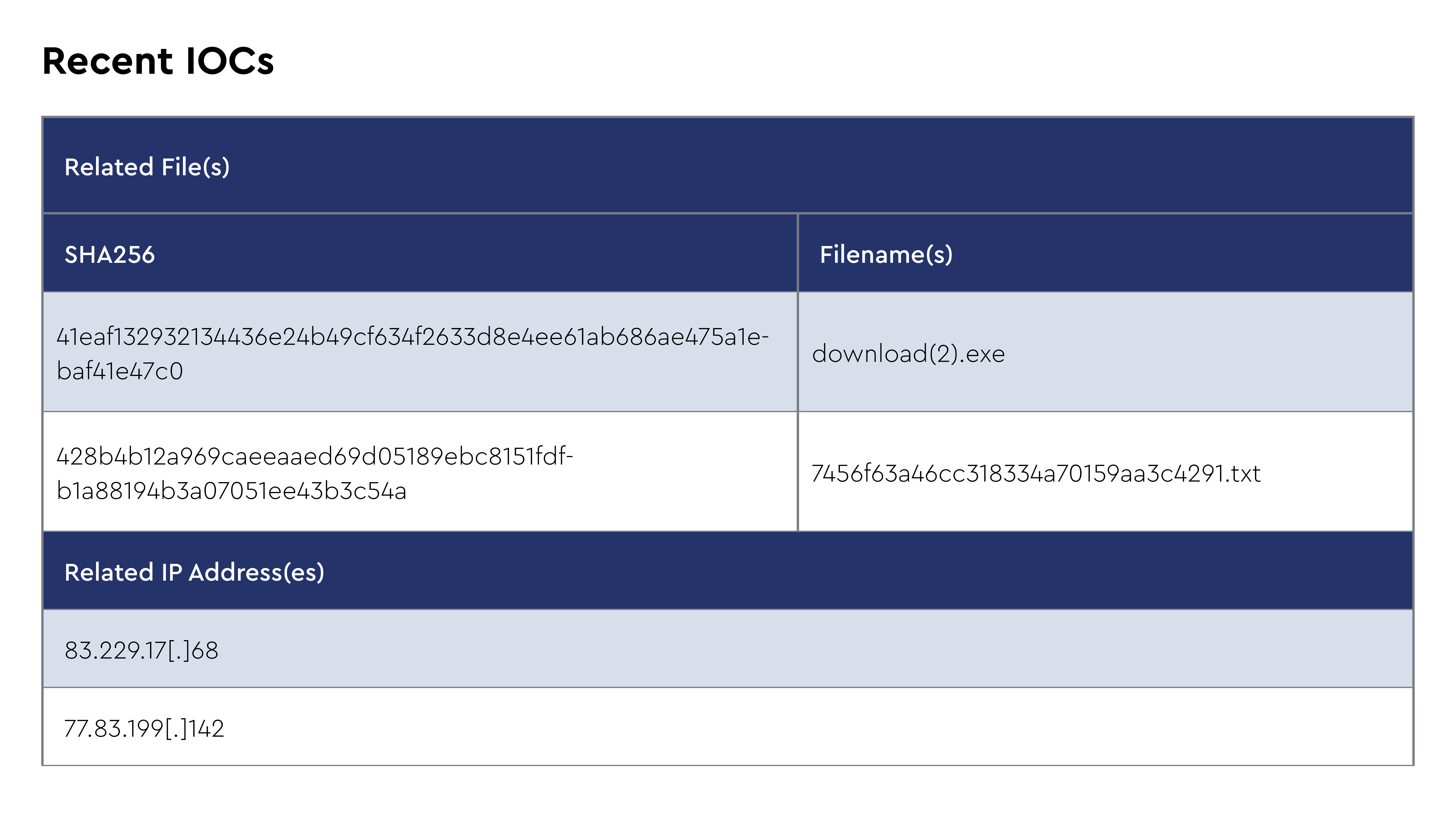
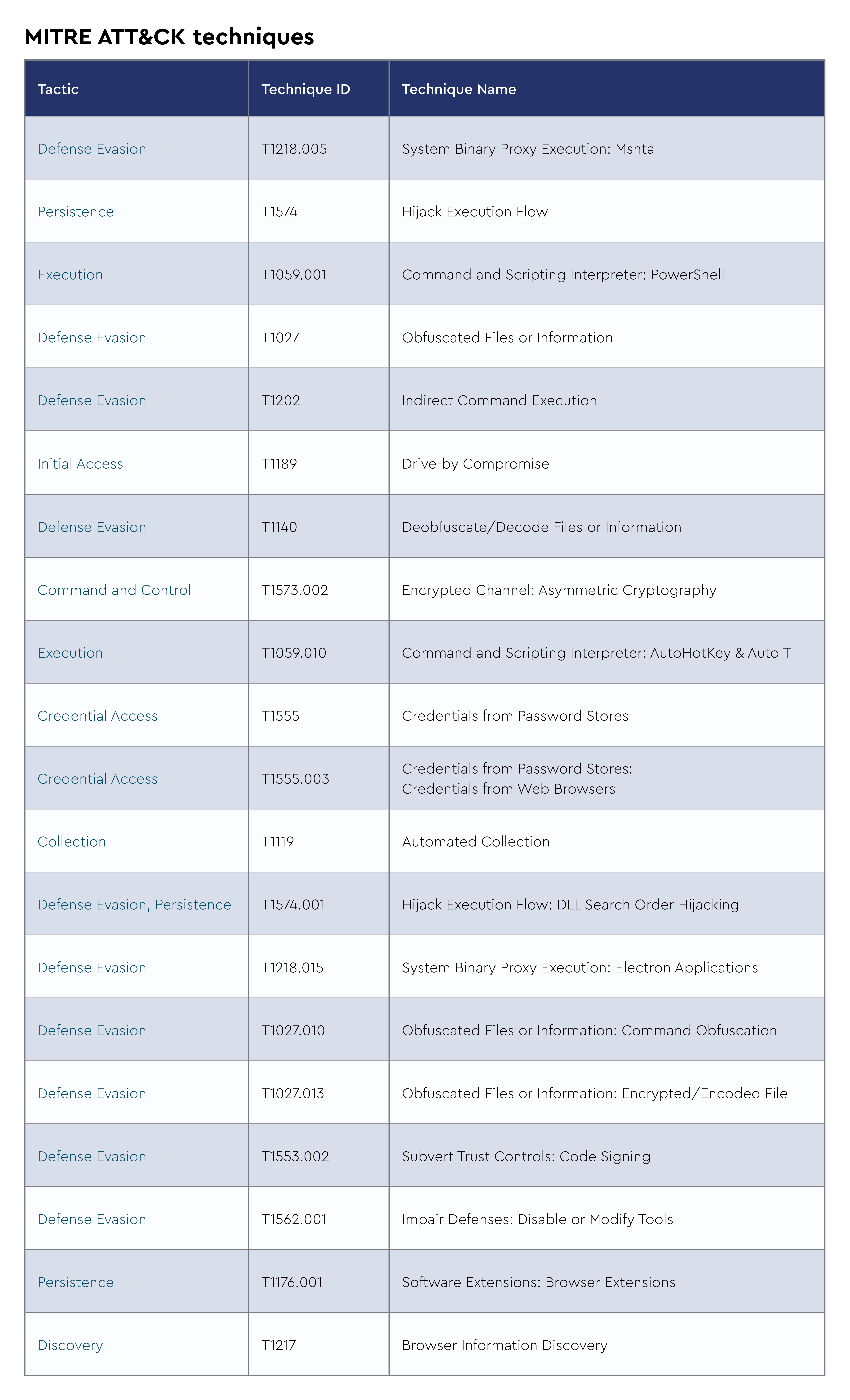
StealC is a popular information stealer and malware downloader sold as malware-as-a-service since January 2023. Version 2.0 was introduced in March 2025, featuring streamlined C2 communications, RC4 encryption, and expanded payload delivery options, including MSI packages and PowerShell scripts. The malware emerged as a lightweight info-stealer selling for $200/month on dark web forums, gaining traction through aggressive promotion and code similarities to established stealers like Vidar, Raccoon, Mars, and RedLine. According to the CRU analysis, StealC 2.0 introduces significant technical improvements, including multi-stage deployment capabilities, enhanced evasion techniques through encrypted C2 communications, and an embedded builder tool enabling custom builds with specific data theft rules for different environments.
In May 2025, the CRU observed StealC being deployed through the Ngioweb botnet alongside NetSupport RAT and SOCGholish (FakeUpdates) in sophisticated multi-stage attack chains. This combination was documented in SmartApeSG campaigns where legitimate but compromised websites with injected scripts led to fake browser update pages distributing NetSupport RAT, followed by StealC as a secondary payload. The initial access vector involved TikTok videos likely generated using AI tools that instructed users to run malicious commands on their systems under false pretenses of activating Windows, Microsoft Office, CapCut, and Spotify through the ClickFix technique.
May 2025 campaigns demonstrated StealC's integration into established distribution frameworks. Threat actors leverage fake browser updates to deliver the initial RAT payload before deploying StealC for credential harvesting from browsers, cryptocurrency wallets, and cloud services through DLL side-loading techniques that abuse legitimate Windows Media Foundation files.
Infrastructure
Victimology
Capabilities
Lumma Stealer is an information stealer malware sold as a service since August 2022, developed by Russian threat actor Shamel. The malware infected over 394,000 Windows computers globally between March and May 2025, with Europol calling it the "world's most significant infostealer threat". Lumma steals passwords, browser data, cryptocurrency wallets, session tokens, and two-factor authentication credentials from infected systems.
The developer operates approximately 400 active clients, selling different service levels through Telegram channels and Russian-language forums. The malware uses dead drop resolver techniques, hiding actual command-and-control server addresses on legitimate platforms like Steam, Google Forms, and Google Slides rather than hardcoding them into the malware.
In May 2025, the CRU observed Lumma being used with Penguish and HijackLoader in multi-stage attacks. HijackLoader, a modular loader active since 2023, delivers Lumma and other payloads by decrypting PNG files and uses techniques such as Heaven's Gate to bypass security software. These May campaigns used fake CAPTCHA sites that tricked users into running malicious PowerShell commands, with researchers estimating up to 5,000 such sites were involved. The operation was disrupted in mid-May 2025 when Microsoft's Digital Crimes Unit, the FBI, Europol, and international partners seized approximately 2,300 domains that formed Lumma's infrastructure, significantly reducing but not eliminating the threat.
Infrastructure
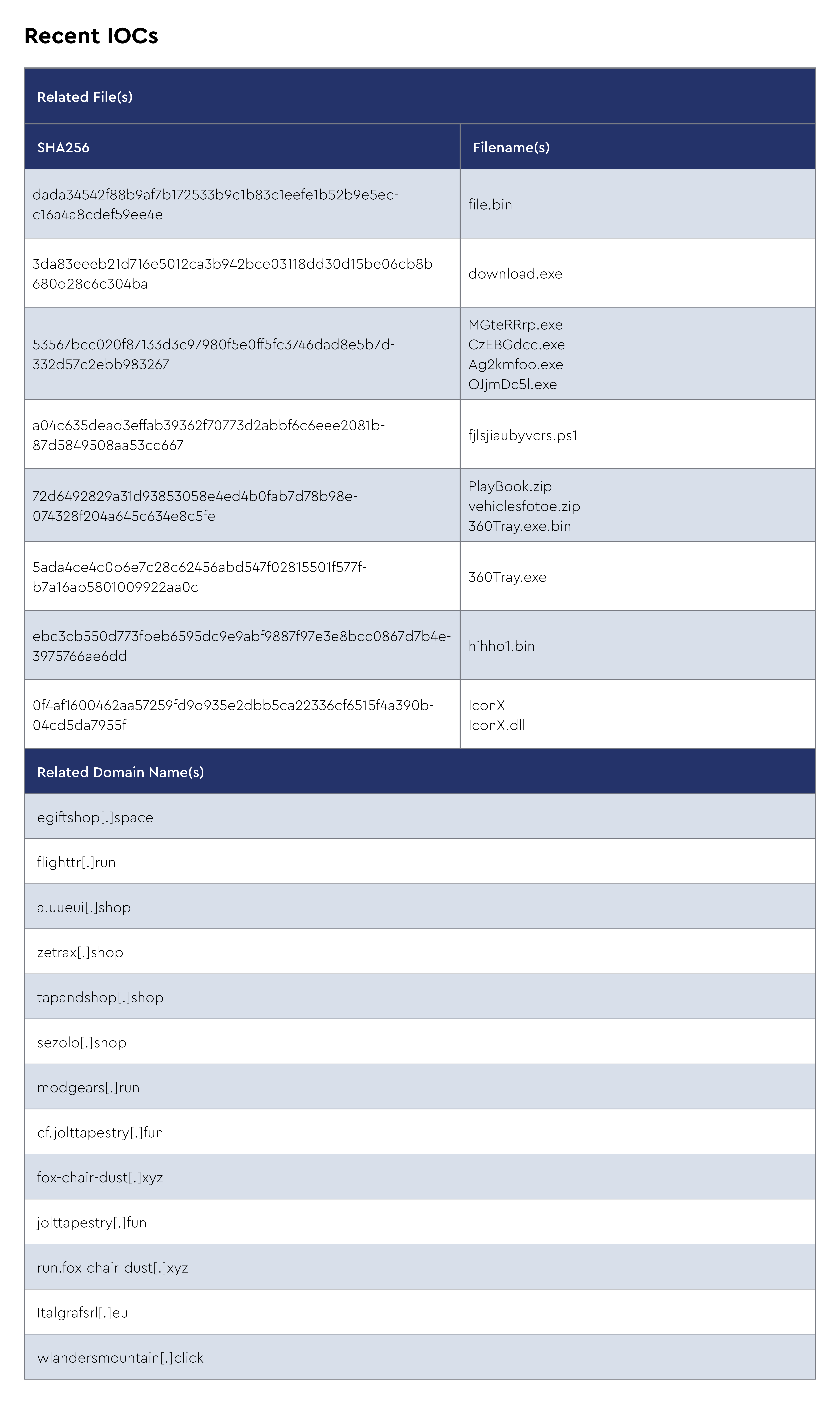
Victimology
Capabilities
NetSupport RAT is a legitimate remote administration tool that has been repurposed by cybercriminals as a remote access trojan since at least 2017. Originally designed for technical support and system management, threat actors have weaponized NetSupport RAT to gain unauthorized remote access to victim systems for malicious purposes.
The malware is distributed through various methods, including fake browser updates, malvertising campaigns, and social engineering attacks that masquerade as legitimate software downloads. NetSupport RAT has been observed targeting multiple sectors, including education, government, and business services, with over 15 new infections detected in recent weeks, according to security researchers. The tool's legitimate origins make it particularly effective at evading detection, as many security solutions may safelist the software.
The CRU observed NetSupport RAT being used with StealC and SocGholish, attributed to SmartApeSG campaigns. These attacks typically begin with compromised websites displaying fake browser update pages that trick users into downloading malicious JavaScript files, which then deploy NetSupport RAT as the initial payload before delivering secondary malware, such as StealC, for credential harvesting.
The malware establishes persistence through registry modifications and can perform various malicious activities, including file transfer, system monitoring, keystroke logging, and lateral movement within compromised networks. Recent campaigns have shown NetSupport RAT being delivered through increasingly sophisticated attack chains involving multiple stages of obfuscated scripts and legitimate cloud services for command-and-control infrastructure.
Infrastructure
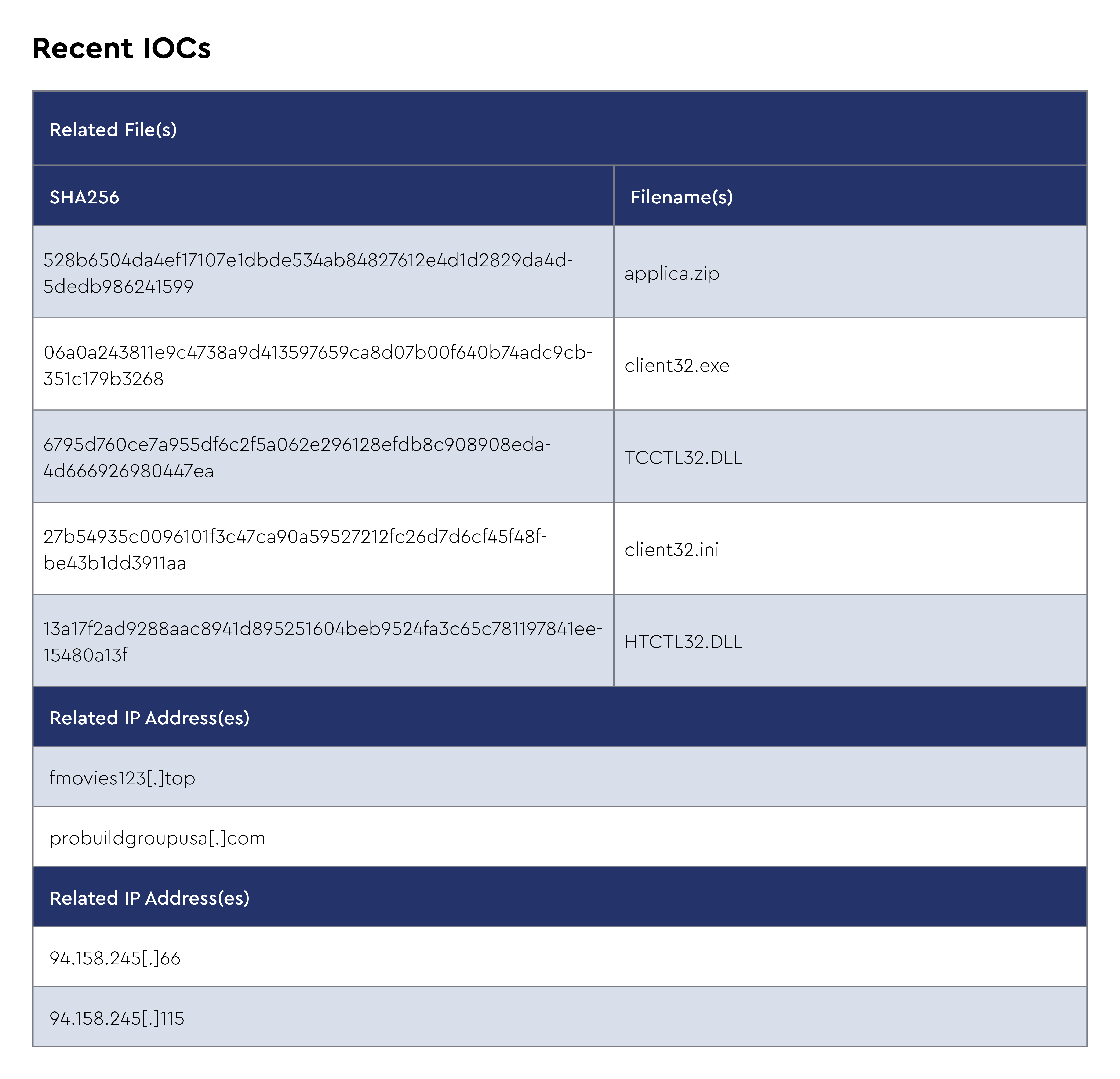
Victimology
Capabilities
FakeUpdates, also known as SocGholish, is a JavaScript-based loader malware that has been active since at least 2017, operated by threat actor TA569 (Mustard Tempest). The malware specializes in drive-by downloads that masquerade as legitimate software updates, typically browser updates for Chrome, Firefox, and Edge, delivered through compromised websites injected with malicious JavaScript code. When users visit infected sites, they encounter convincing fake update prompts that trick them into downloading and executing malicious files disguised as critical security updates. The malware performs extensive reconnaissance using Windows management instrumentation calls to profile victim systems and determine eligibility for additional payloads.
As observed by the CRU in May 2025, SocGholish was used in conjunction with NetSupport RAT and StealC in SmartApeSG campaigns, demonstrating its continued role as an initial access facilitator for multi-stage attacks. TA569 monetizes access gained through SocGholish infections by selling compromised system access to other cybercrime groups, including Indrik Spider, who deploy secondary payloads such as Cobalt Strike, ransomware (DoppelPaymer), and information stealers (CHTHONIC, DRIDEX, AZORULT). The malware's sophisticated evasion techniques include eligibility checks to avoid analysis environments, obfuscated JavaScript code, and careful campaign management that makes incident response analysis particularly challenging for defenders.
Infrastructure
Victimology
Capabilities