Welcome to the April 2025 edition of the ConnectWise Cyber Research Unit™ (CRU) Monthly Threat Brief. This report provides a comprehensive look at the most significant cybersecurity developments impacting the MSP and SMB landscape. We break down the month’s top stories, critical vulnerabilities, and prevalent malware families to help you stay informed and prepared in an evolving threat environment.
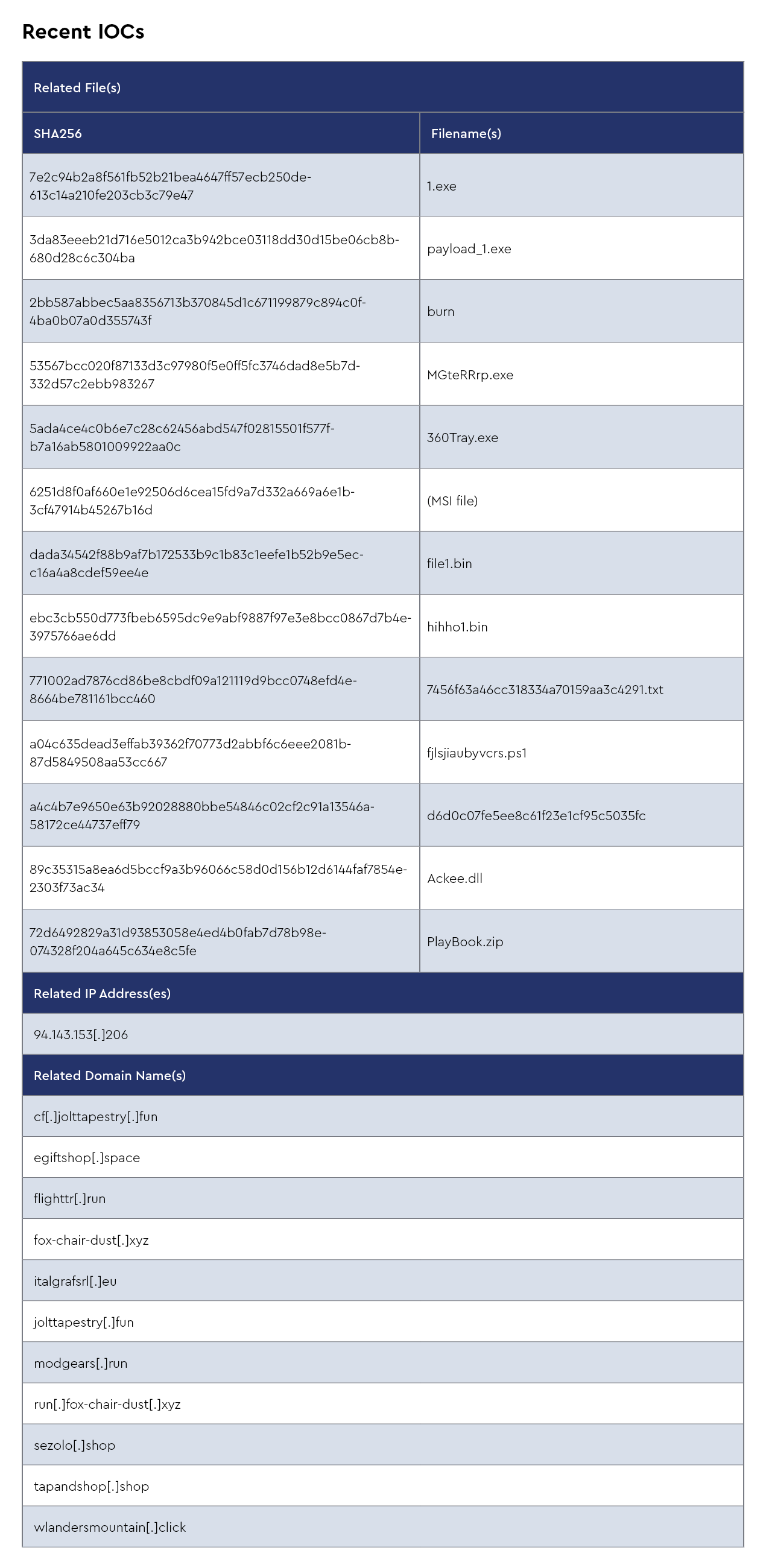
There has been a significant increase in cyberattacks using fake online file converters since February. These attacks target users searching for free tools to convert document formats, such as PDFs to Word or images to PDFs. The attackers create legitimate-looking websites with trusted branding and HTTPS certificates, but these sites deliver ransomware, remote access trojans (RATs), or credential stealers when users upload or download files. The FBI issued a warning about this trend in early March. These malicious sites succeed because attackers use SEO poisoning to rank high in search results and sometimes purchase ad space (malvertising) to appear more legitimate. Two specific sites involved in these scams, docu-flex[.]com and pdfixers[.]com, have been observed in multiple incidents but are now offline.
These attacks pose serious threats to businesses, especially those without strong backup practices. Small and midsized businesses (SMBs) face expensive downtime and data loss, while credential-stealing malware can provide attackers access to cloud platforms and sensitive accounts. For MSPs specifically, a single compromised account can cascade into broader breaches affecting multiple clients. While technical controls such as endpoint detection (EDR) and web filtering are important, user education remains equally critical. Organizations need regularly tested backups and clear incident response plans that are frequently reviewed and updated to address evolving threats.
What this means for MSPs
This trend poses a particular risk for managed service providers (MSPs) due to their access to multiple client environments. A single compromised MSP account can rapidly escalate into widespread breaches affecting numerous clients. MSPs must implement a multi-layered approach that combines robust technical controls with comprehensive user education. Client training should specifically address how to identify suspicious websites, verify URLs, and understand that security indicators such as HTTPS certificates don’t guarantee safety.
Additionally, it’s critical for MSPs to prioritize implementing and regularly testing backup solutions for all clients while maintaining updated incident response plans that address these evolving threat vectors. These preparations allow MSPs to help clients recover quickly from attacks without considering ransom payments.
Recent discoveries have revealed significant vulnerabilities in popular archive utilities WinRAR and 7-Zip that allow attackers to bypass Windows’ Mark of the Web (MoTW) security feature. MoTW is a Windows security feature that tags files downloaded from the internet with metadata about their origin, prompting warnings when these files are executed and allowing applications such as Microsoft Office to open documents in protected view.
In April 2025, vulnerability CVE-2025-31334 was identified in WinRAR versions before 7.11, which allows attackers to create specially crafted symbolic links within archives that bypass MoTW security prompts when opened, potentially leading to arbitrary code execution without user consent. Similarly, in January 2025, CVE-2025-0411 was discovered in 7-Zip versions before 24.09, involving improper handling of nested archives where 7-Zip fails to propagate the MoTW to extracted files, allowing them to execute without triggering security warnings. These vulnerabilities have significant security implications as they allow attackers to execute malicious code without triggering standard security warnings, undermining user trust and potentially increasing infection rates of malware, including ransomware and spyware.
What this means for MSPs
MSPs must ensure all client systems are updated to the latest versions of archive utilities, including WinRAR and 7-Zip, to protect against these known vulnerabilities. It’s crucial for MSPs to implement a proactive approach that includes regular monitoring and application of security patches across all client environments. Client education about the importance of these updates and the role of security features such as MoTW should be prioritized as part of their security awareness programs. Implementing centralized patch management solutions can streamline this process, ensuring uniform protection across all endpoints. MSPs may also want to consider creating custom security policies that restrict the use of outdated archive utilities and monitor for potential exploitation attempts of these vulnerabilities.
The CRU identified a new information stealer called Xerph Stealer that appeared on the market around May 2024. Although relatively rudimentary compared to other commodity infostealers, its low price and frequent updates suggest potential for increased usage and capabilities. The analysis shows that after initial access, the attack chain begins with a victim running a JavaScript file that uses UpCrypter, a loader sold by Brazilian developer pjoao1587. This initiates an obfuscated execution chain that ultimately delivers Xerph Stealer, which is injected into RegAsm.exe. Xerph’s functionality includes extraction of credit cards, messenger data, crypto wallets, passwords, FTP credentials, crypto wallet seeds, and Wi-Fi keys. It can also download and execute various file types, including .cmd, .vbs, .dll, .exe, .ps1, and .py files. The stealer checks in with its command and control server approximately every 10 seconds. Developed by a user known as heartBit, Xerph Stealer is being sold for $390 for lifetime access. The developer has continued providing updates to target more browsers and wallets, with the most recent analyzed version being 1.1.9.
What this means for MSPs
For MSPs, the emergence of Xerph Stealer represents a new threat to monitor in their clients’ environments. While currently described as “rudimentary” compared to other infostealers, its ongoing development and low price point make it accessible to cybercriminals who cycle through commodity malware tools. MSPs must update their detection mechanisms to identify the indicators of compromise listed in the article, particularly focusing on the execution chain that begins with JavaScript files and involves PowerShell processes. It’s also critical to implement monitoring for connections to the identified command and control servers and apply the provided YARA rule for detection.
Additionally, MSPs should educate clients about the dangers of running unknown JavaScript files, as this appears to be a key initial vector in the Xerph Stealer attack chain. It’s important that regular scanning for the targeted subdirectories listed in the appendix be part of MSPs’ security protocols to detect potential compromises early.
CVE-2025-26633
CVE-2025-26633, also known as “MSC EvilTwin,” is a security feature bypass vulnerability in Microsoft Management Console (MMC) that allows attackers to execute malicious code by exploiting improperly sanitized user input. The flaw enables adversaries to create two “.msc” files with identical names—one benign and one malicious—causing MMC to execute the malicious file when the legitimate one is opened. Microsoft addressed this vulnerability in its March 2025 Patch Tuesday update, assigning it a CVSS score of 7.0.
In April 2025, the Russian threat actor group known as Water Gamayun—also referred to as EncryptHub or LARVA-208—actively exploited CVE-2025-26633 in targeted attacks. They leveraged the vulnerability to deploy custom backdoors named SilentPrism and DarkWisp, using signed “.msi” installers disguised as legitimate applications such as DingTalk and VooV Meeting. These campaigns involved the use of malicious provisioning packages and Windows installer files to deliver payloads, establish persistence, and exfiltrate data.
CVE-2025-31334
CVE-2025-31334 is a medium-severity vulnerability in WinRAR (versions prior to 7.11) that allows attackers to bypass Windows’ Mark of the Web (MoTW) security feature. By crafting archive files containing symbolic links (symlinks) pointing to executable files, attackers can trick users into executing malicious code without receiving the usual security warnings. This vulnerability was disclosed in early April 2025 and has been addressed in WinRAR version 7.11.
The nature of this vulnerability makes it a valuable tool for threat actors aiming to deliver malware stealthily. Similar MoTW bypass techniques have been previously exploited by state-sponsored groups, such as Russian hackers using 7-Zip vulnerabilities to deploy malware, including Smokeloader. Given the widespread use of WinRAR and the potential for abuse, users are strongly advised to update to version 7.11 promptly and exercise caution when handling archive files from untrusted sources.
CVE-2025-0411
CVE-2025-0411 is a high-severity vulnerability in 7-Zip (versions prior to 24.09) that allows attackers to bypass Windows’ MoTW security feature. By crafting nested archives, attackers can prevent MoTW from being applied to extracted files, enabling the execution of malicious code without the usual security warnings. This vulnerability was actively exploited as a zero-day in late 2024 and has been added to CISA’s Known Exploited Vulnerabilities Catalog.
In April 2025, Russian cybercrime groups leveraged CVE-2025-0411 in spear-phishing campaigns targeting Ukrainian organizations. These campaigns used homoglyph attacks to disguise malicious files as legitimate documents, leading to the deployment of SmokeLoader malware. The exploitation of this vulnerability underscores the importance of promptly updating 7-Zip to version 24.09 or later and exercising caution when handling archive files from untrusted sources.
CVE-2024-55591
CVE-2024-55591 is a critical authentication bypass vulnerability in Fortinet’s FortiOS (versions 7.0.0 to 7.0.16) and FortiProxy (versions 7.0.0 to 7.0.19 and 7.2.0 to 7.2.12). It allows unauthenticated remote attackers to gain super-admin privileges by sending crafted requests to the Node.js WebSocket module. This flaw, identified as CWE-288, was actively exploited as a zero-day from November 2024 and publicly disclosed by Fortinet in January 2025. The US Cybersecurity and Infrastructure Security Agency (CISA) added it to its Known Exploited Vulnerabilities (KEV) catalog on January 14, 2025, mandating federal agencies to apply patches by January 21, 2025.
In April 2025, threat intelligence reports highlighted that the ransomware group “Mora\_001,” with ties to LockBit, exploited CVE-2024-55591 alongside CVE-2025-24472 to deploy a ransomware strain dubbed “SuperBlack.” Their attack chain involved exploiting exposed FortiGate management interfaces, creating administrative accounts, modifying configurations, and establishing VPN tunnels for lateral movement and data exfiltration. Security firms observed that Mora\_001 leveraged both publicly available and modified proof-of-concept exploits to target vulnerable systems.
This section leverages the Diamond Model of Intrusion Analysis to structure the examination of recent malware activity, providing a clear analytical framework that links adversary, capabilities, infrastructure, and victimology. By applying the Diamond Model, we can better contextualize malicious behavior, identify patterns across campaigns, and highlight the relationships between threat actors, tools, and targeted entities.
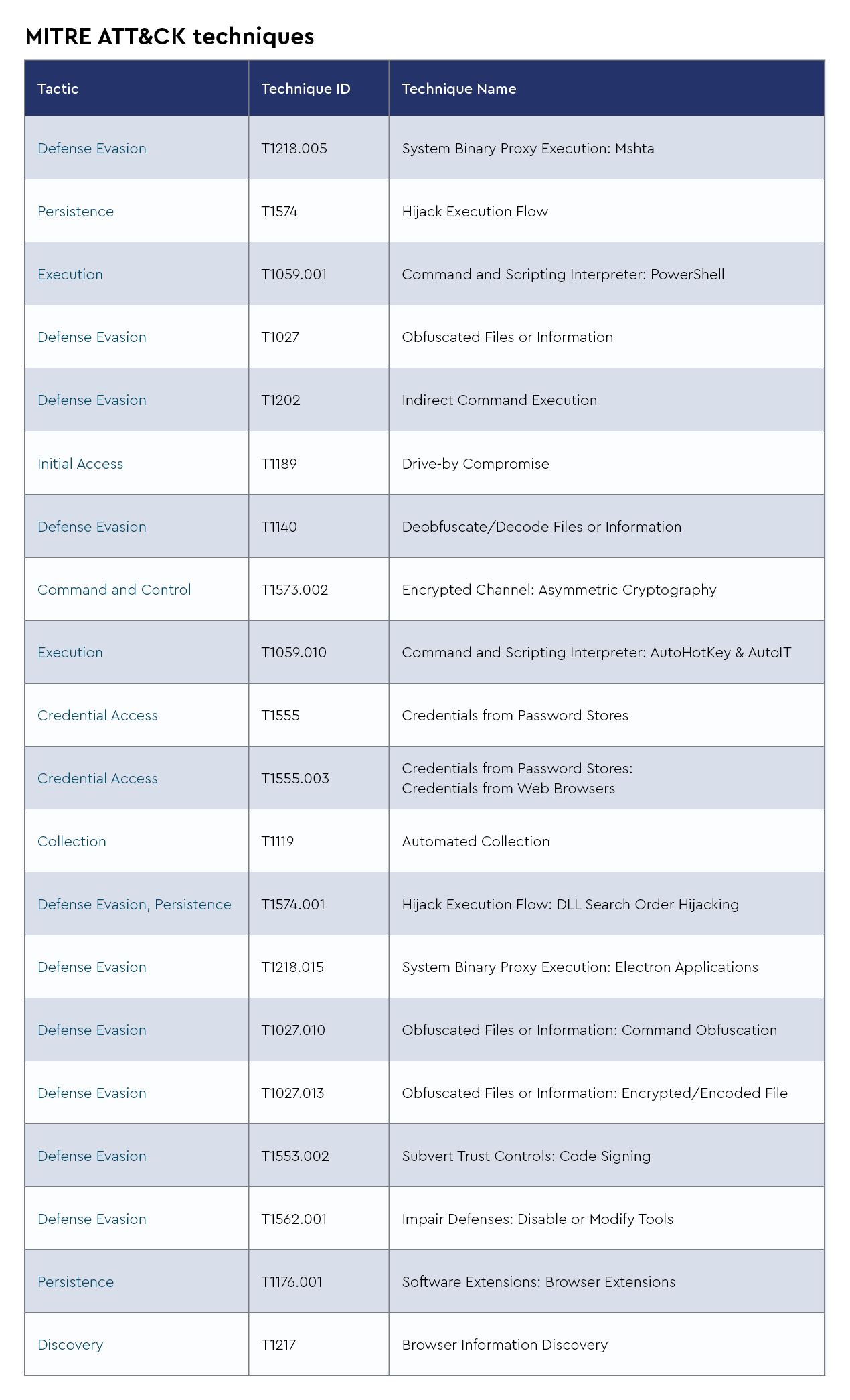
Akira ransomware, operational since March 2023, stands out as a sophisticated ransomware-as-a-service (RaaS) operation that has become one of the most dominant threats in 2025, particularly in North America. Generating at least $42 million in ransom payments through March 2023 to April 2024, Akira has continued its aggressive expansion with 72 attacks in January 2025 and 77 in February, establishing itself as the most active ransomware variant in the United States by market share.
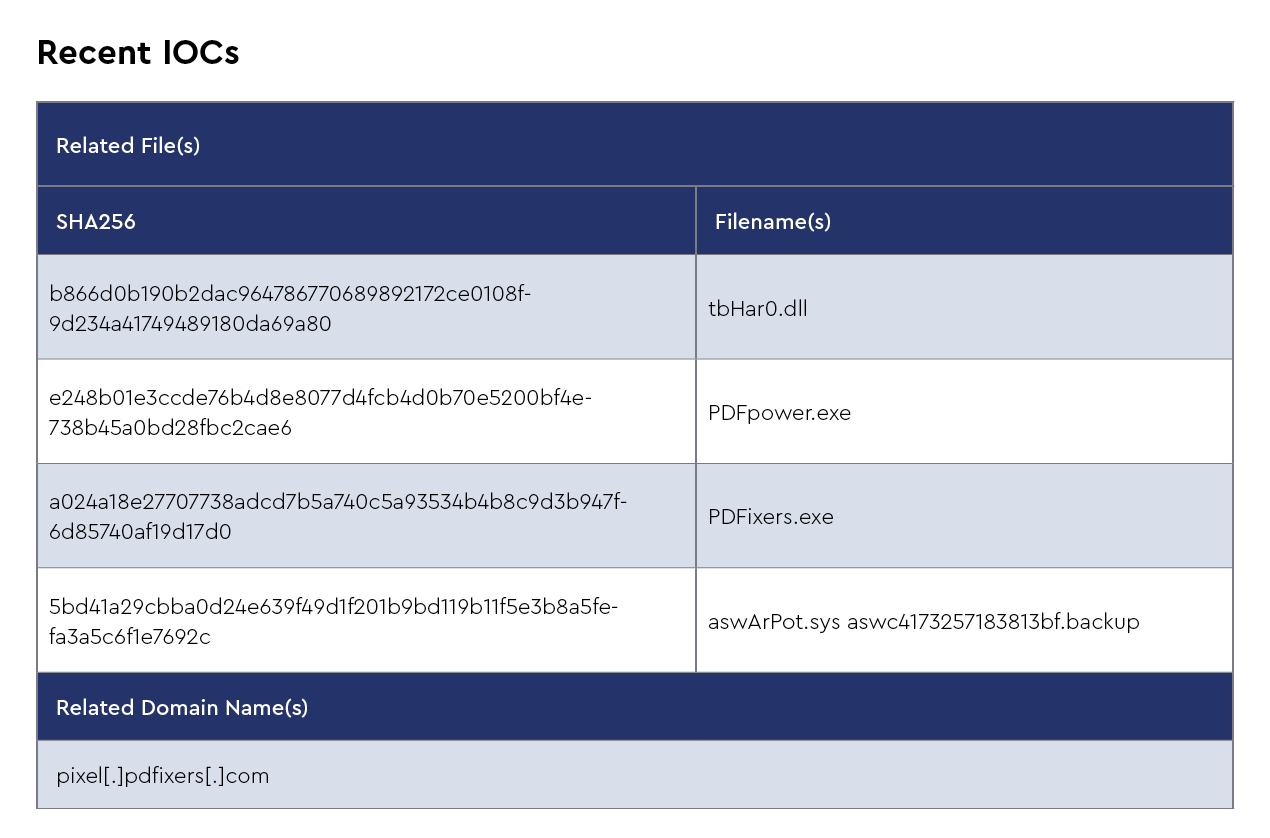
Unlike other ransomware families, Akira employs a unique “retro” styled Tor-based interface reminiscent of 1980s green-screen consoles and offers victims the option to pay for either file decryption or data deletion, not both. Recent intelligence from April 2025 confirms the CRU has identified fake PDF converters (specifically PDFixer and PDFpower) being used as initial attack vectors through SEO poisoning and malvertising, coinciding with an FBI alert issued in March 2025 regarding malicious file converters distributing malware. Once initial access is gained, Akira has been observed delivering a vulnerable Avast Anti-Rootkit Driver (aswArPot.sys) to bypass endpoint detection and response (EDR) solutions by using the driver’s kernel-level privileges to terminate security processes, effectively disabling system defenses before encrypting files.
Adversary
Infrastructure
Victimology
Capabilities
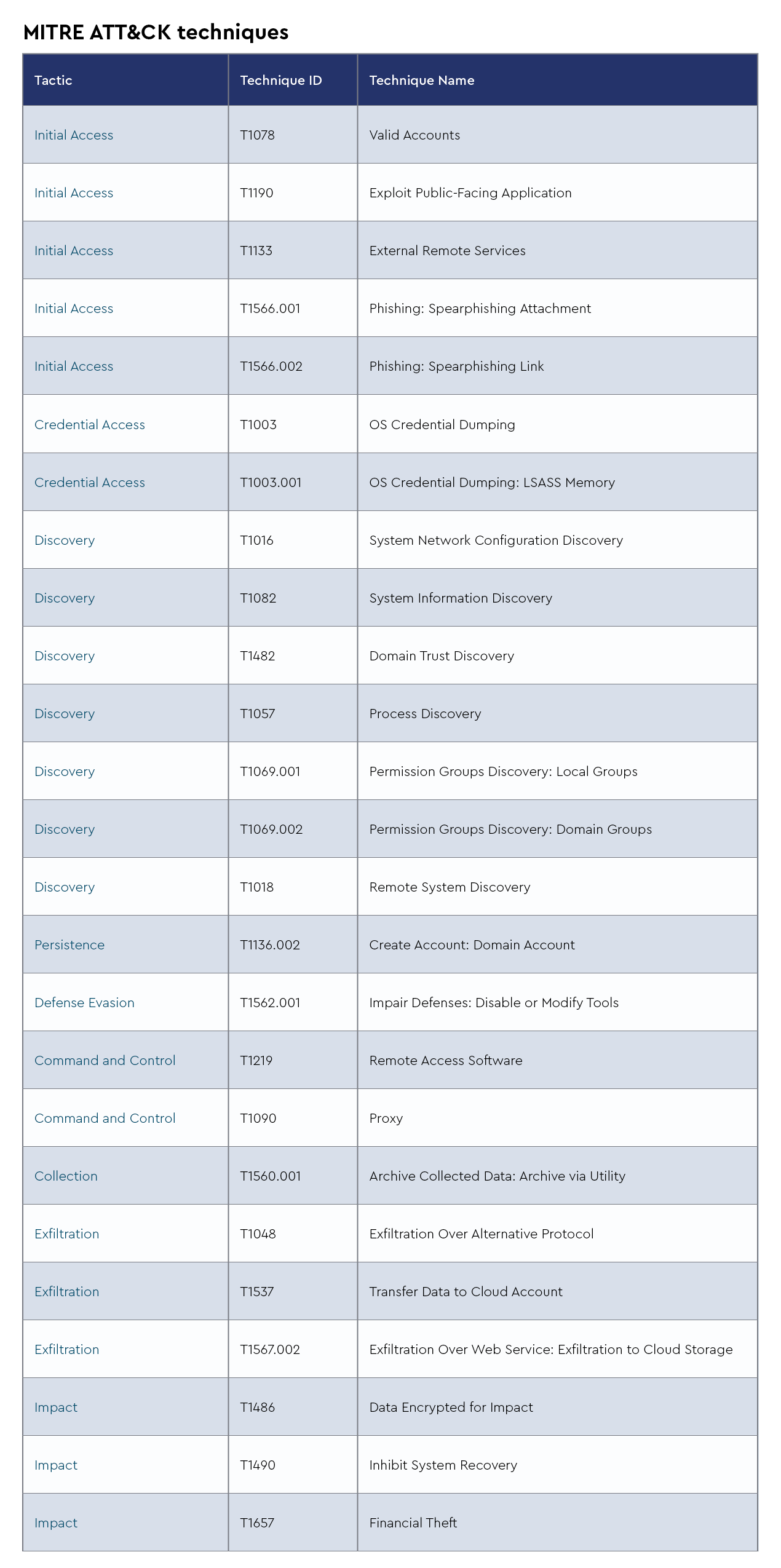
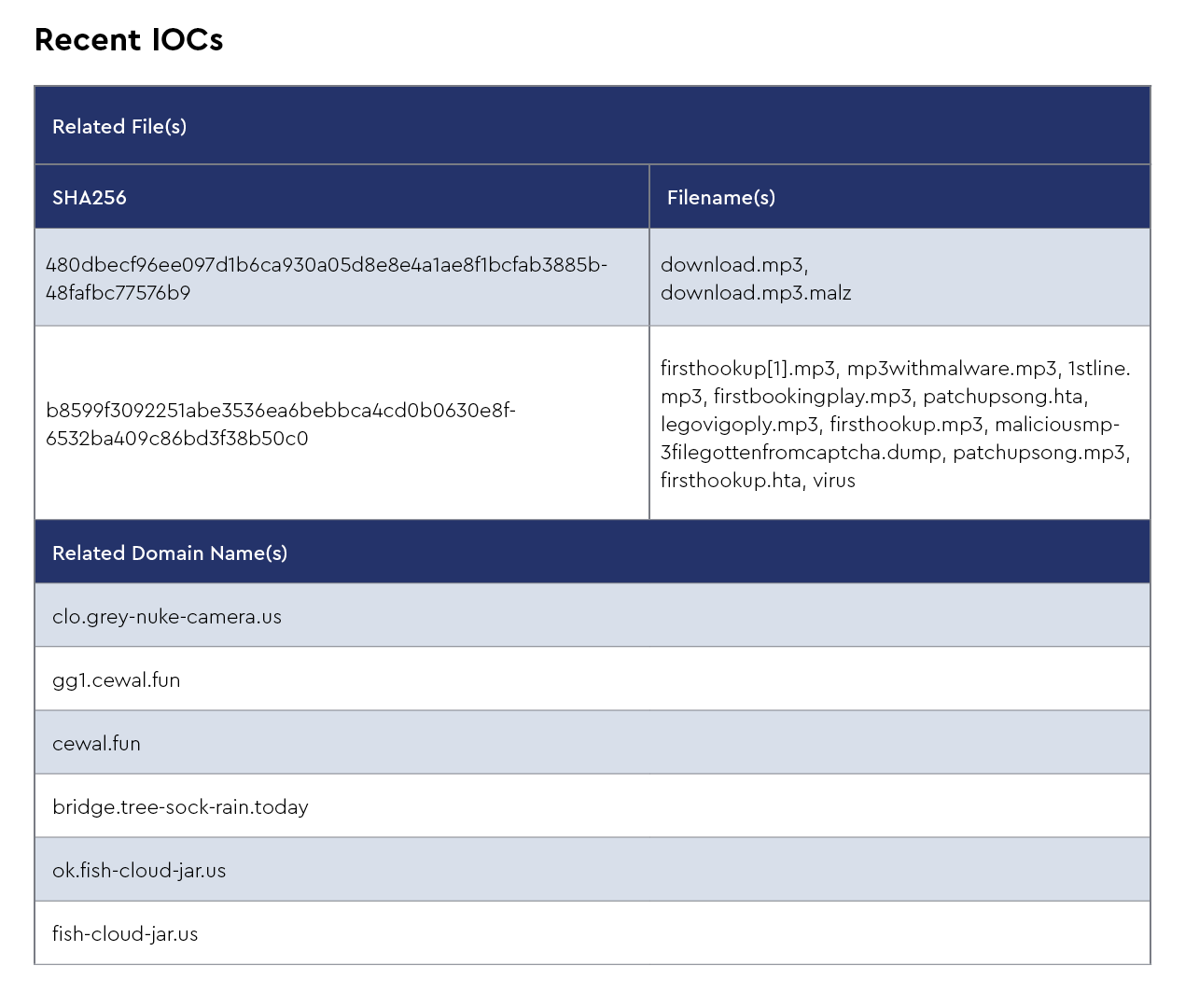
Emmental is a sophisticated banking malware named after Swiss cheese due to its ability to exploit numerous security holes in banking systems. First observed targeting financial institutions in Switzerland, Austria, Japan, and Sweden, it bypasses two-factor authentication by manipulating DNS settings to redirect victims to fake banking websites while installing rogue SSL certificates to avoid browser security warnings. The malware’s attack chain typically begins with phishing emails containing malicious attachments that install fake Windows update tools, enabling attackers to hijack banking sessions and intercept SMS authentication tokens. Recent threat intelligence from April 2025 indicates Emmental has evolved, with CRU observing it being used alongside Rhadamanthys and Lumma stealers in coordinated attacks.
This development is significant as these newer stealers have replaced older variants in many campaigns, with Rhadamanthys incorporating advanced features such as AI-powered optical character recognition and Lumma targeting cryptocurrency wallets. The combined deployment of these tools demonstrates how threat actors are increasingly using comprehensive malware cocktails to maximize their success in compromising financial systems and stealing sensitive data.
Adversary
Infrastructure
Victimology
Capabilities
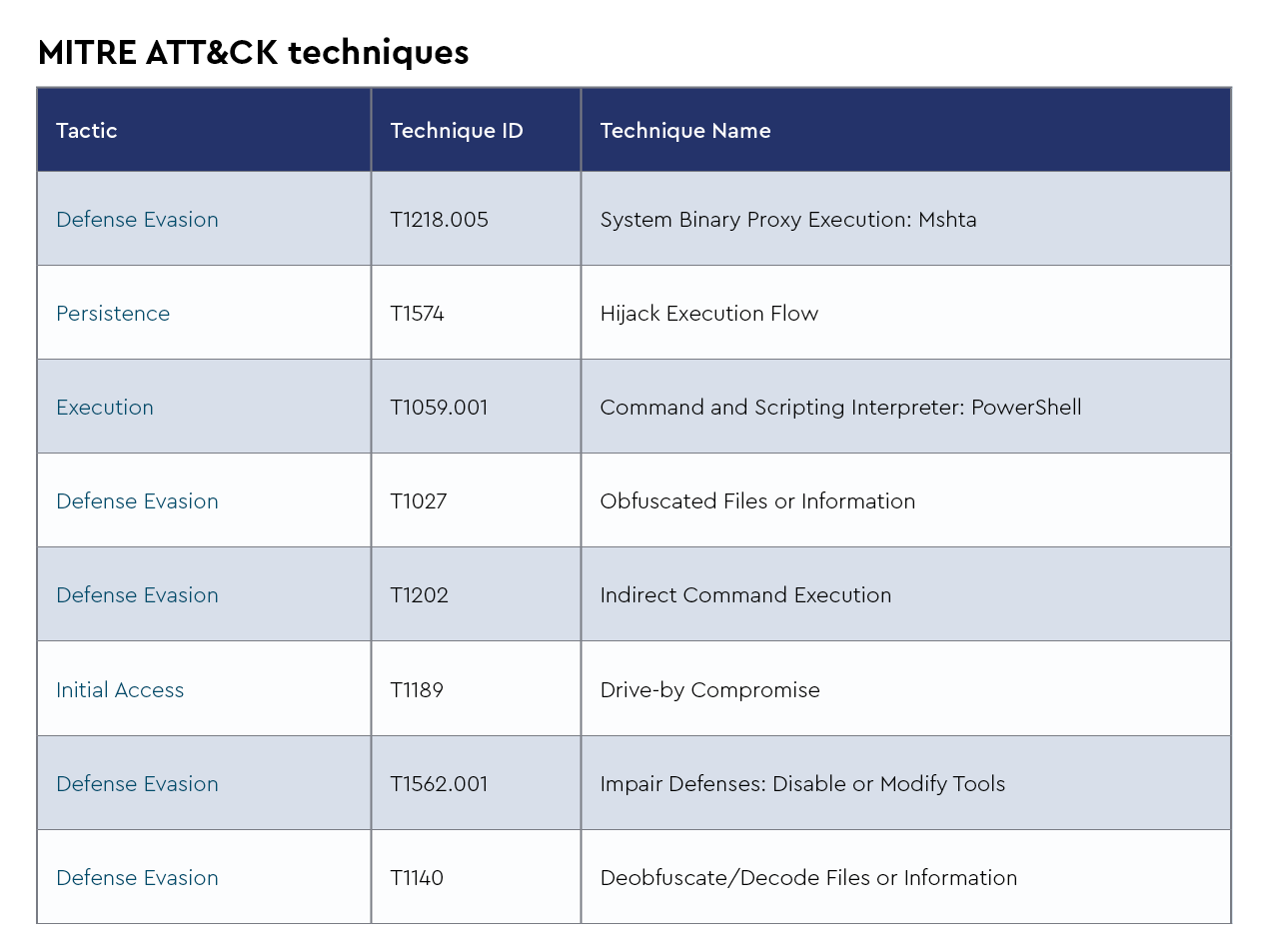
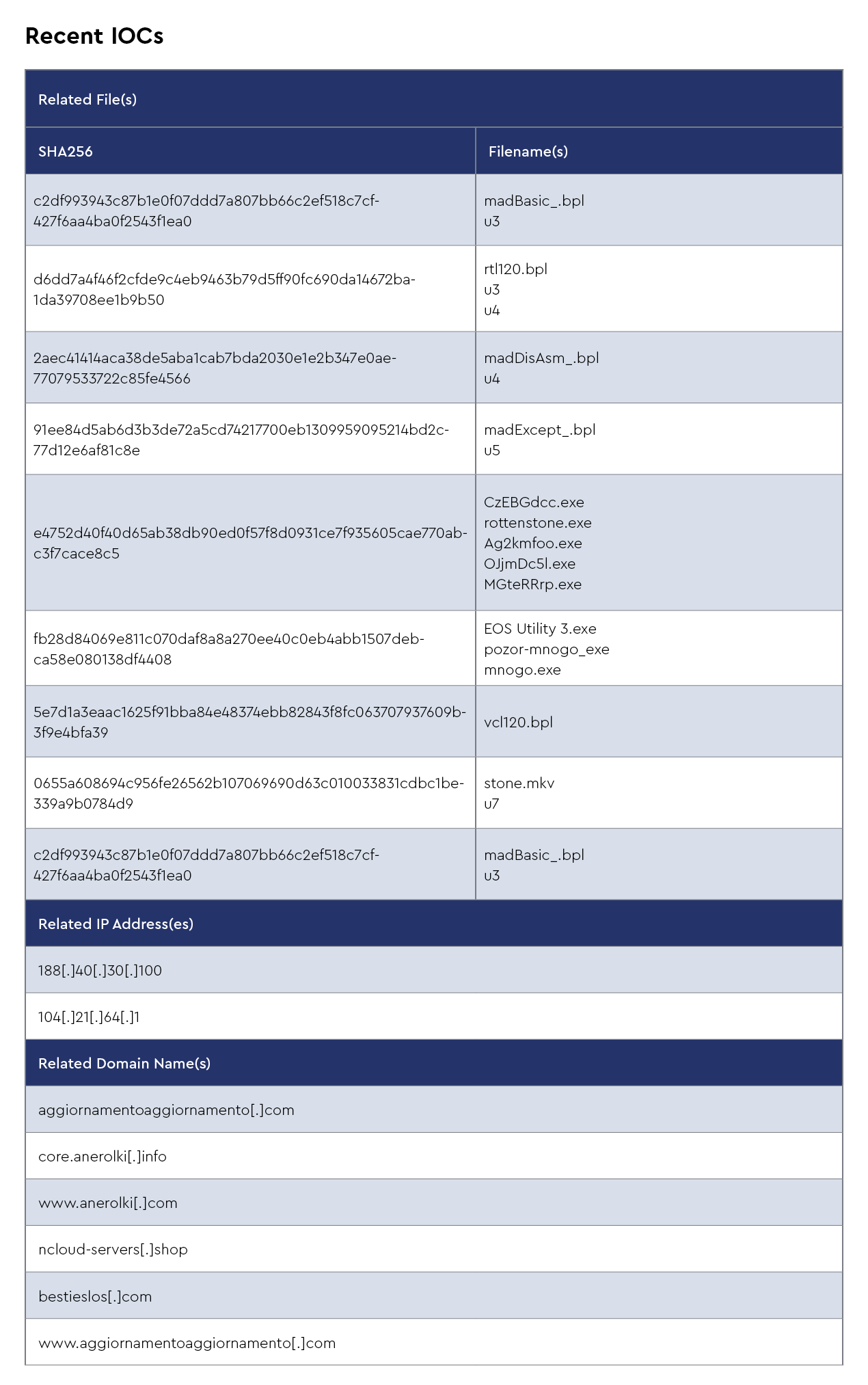
HijackLoader is a modular malware loader that has gained traction for its stealthy multi-stage delivery tactics. The CRU has recently observed campaigns where HijackLoader avoids immediate detection by downloading a series of seemingly benign *.BPL files. Individually, these files appear harmless, but once assembled by the loader, they reconstruct and activate the malicious payload. This approach makes static analysis and traditional signature-based detection significantly more difficult, as no single file contains clearly malicious code.
HijackLoader is frequently used as an initial access vector for deploying additional payloads such as information stealers, remote access trojans, or ransomware. It often leverages advanced evasion techniques, including DLL sideloading, encrypted payloads hidden in PNG IDAT chunks, and dynamic API resolution. This modular “piecekit”-style architecture allows the malware to adapt quickly to different environments and to reconfigure itself mid-campaign, increasing both its longevity and its ability to evade defenses.
Adversary
Infrastructure
Victimology
Capabilities
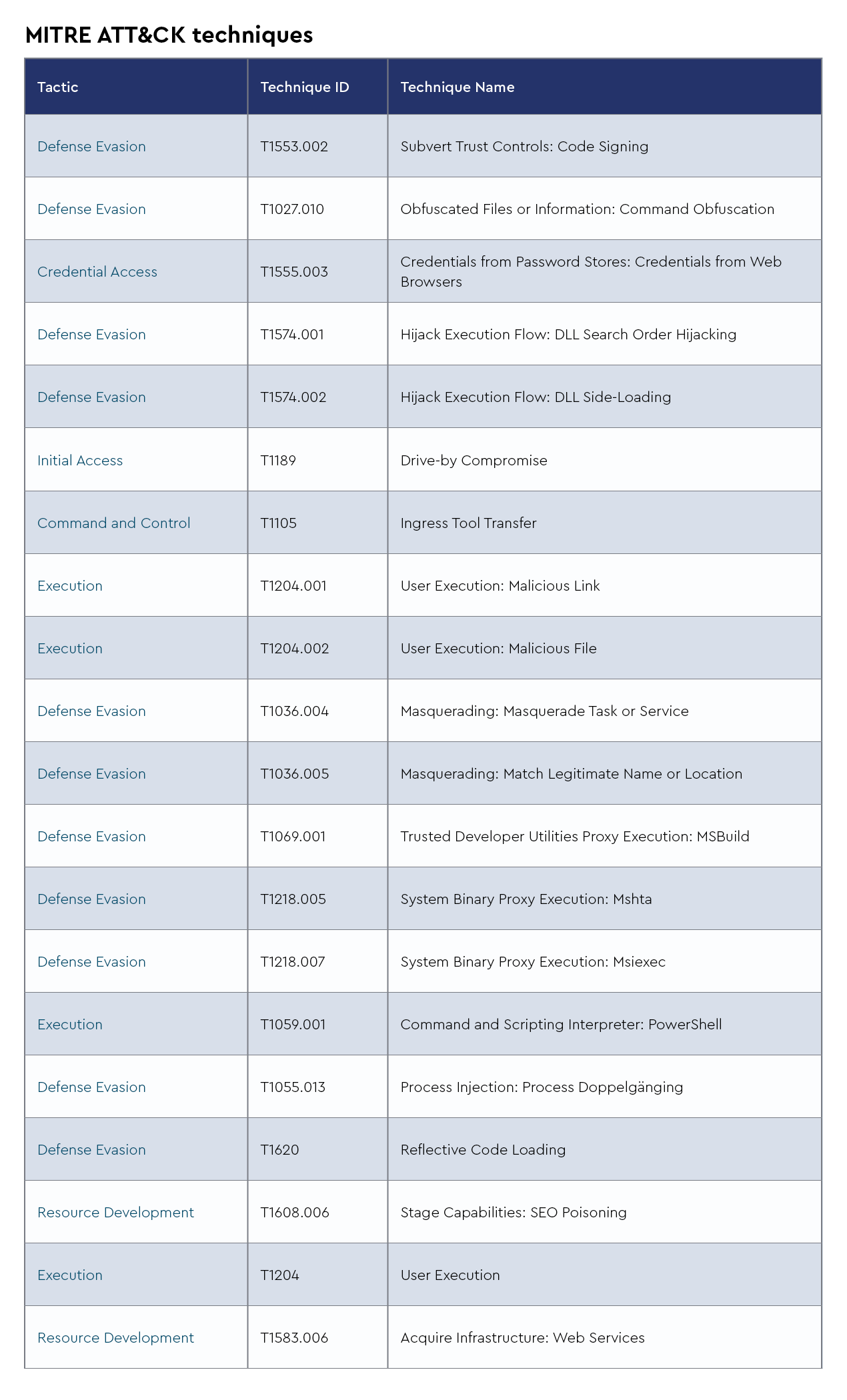
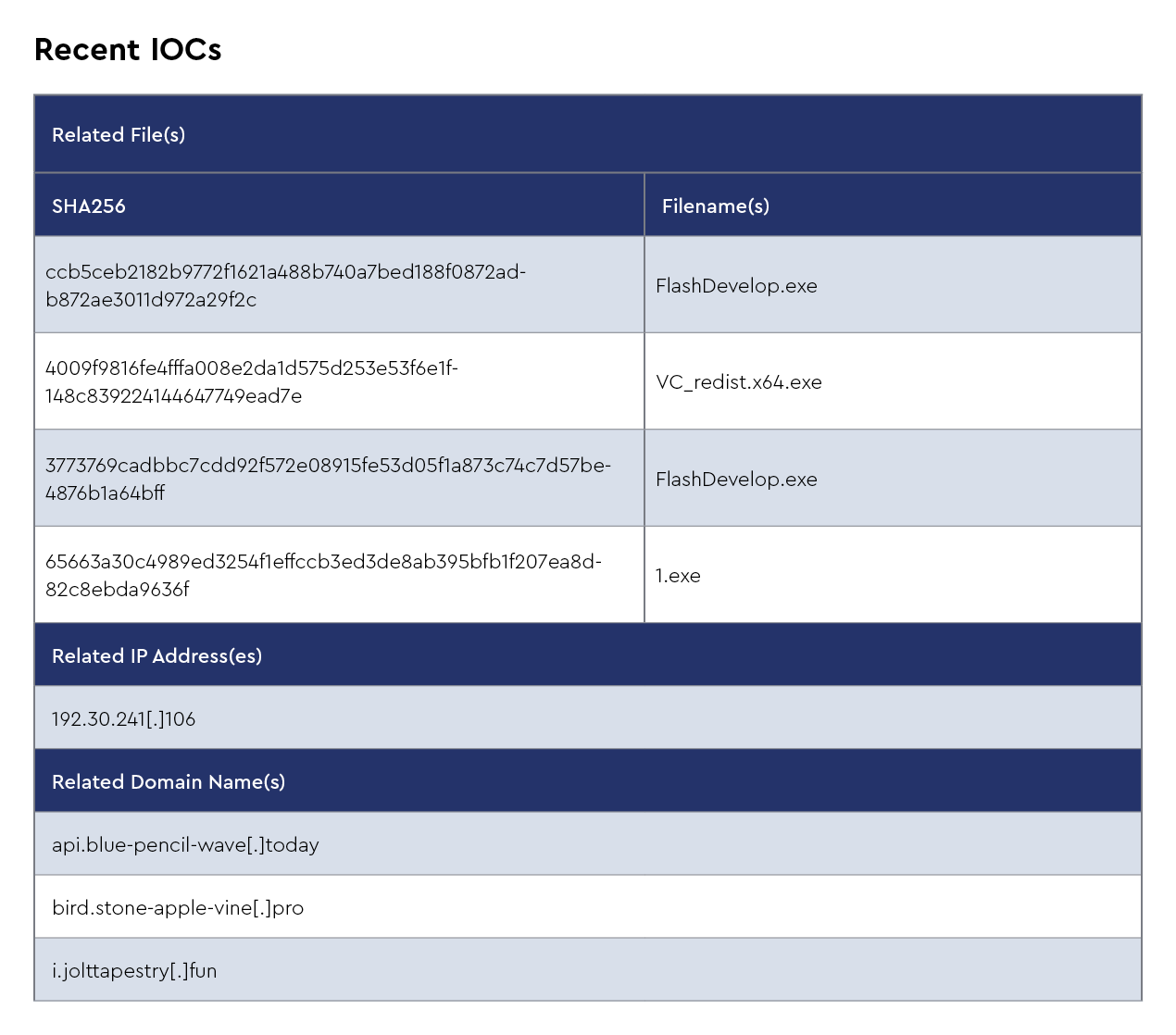
Rhadamanthys is a sophisticated information-stealing malware first discovered in late 2022, operating under a malware-as-a-service (MaaS) model with continuous updates, including a recent v0.9 version released in February 2025, adding features such as increased collection capacity for browser extensions and additional persistence framework.
What makes Rhadamanthys particularly dangerous is its advanced anti-analysis capabilities, especially its downloader component that uses the Quake VM for obfuscation, effectively hiding malicious code through a custom virtual processor that makes detection extremely difficult. Recent threat intelligence from April 2025 indicates that the CRU observed Emmental, a multi-stage loader that typically hides inside modified versions of legitimate Microsoft Windows binaries, being used together with Rhadamanthys in a recent security incident.
This is significant, as Emmental has been distributing various commodity infostealers worldwide since at least February 2024 but maintains relatively low detection rates. The malware continues to evolve with new AI-driven capabilities, including optical character recognition (OCR), and has been observed being deployed alongside StealC malware by threat actors such as EncryptHub, who exploited a recently-patched Windows zero-day vulnerability (CVE-2025-26633). This highlights the continuous refinement of this threat as it targets cryptocurrency wallets, sensitive credentials, and corporate information across multiple sectors.
Adversary
Infrastructure
Victimology
Capabilities
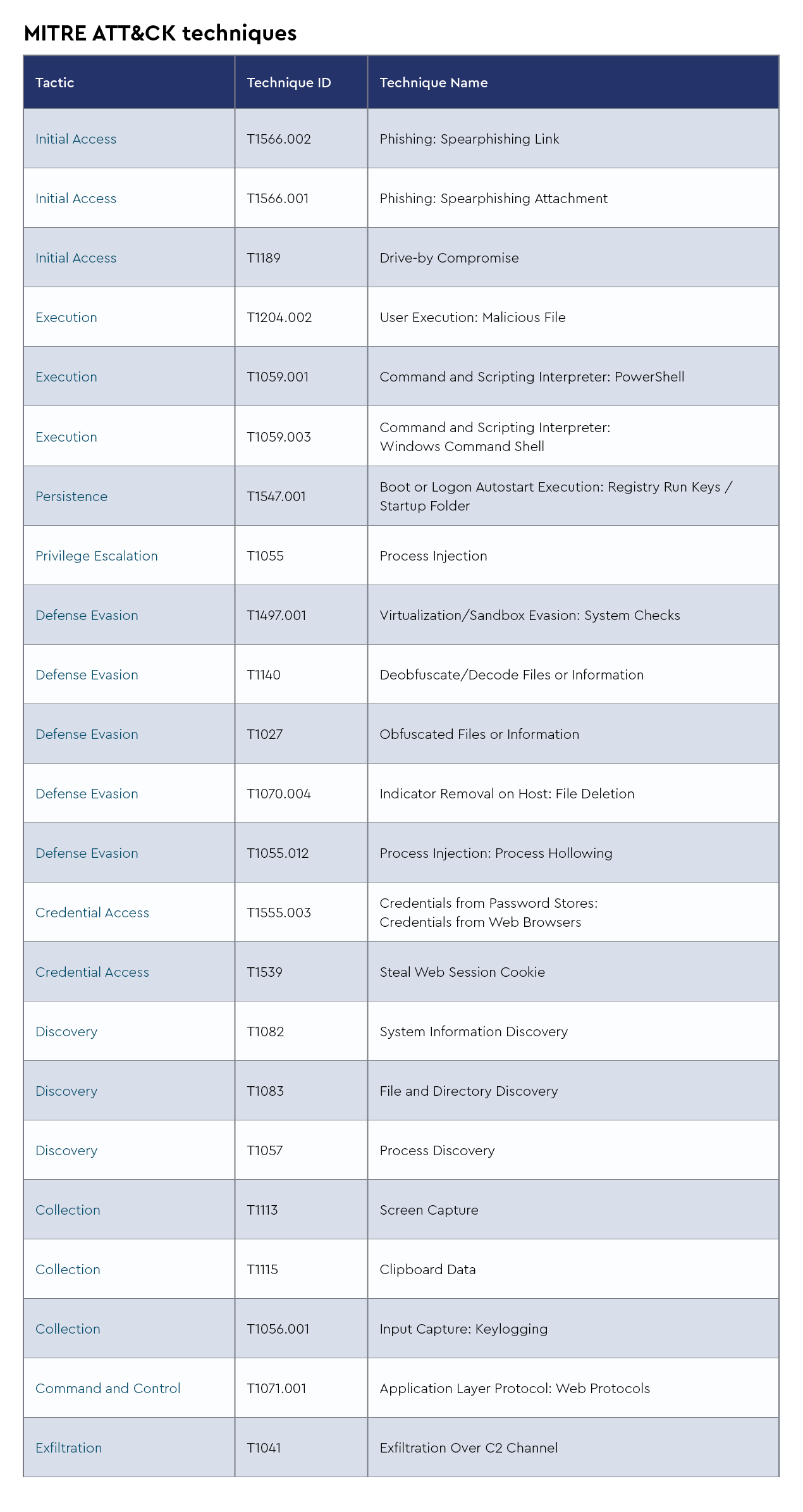
Lumma Stealer is a sophisticated information-stealing malware operating as a malware-as-a-service (MaaS) since 2022, developed by a threat actor known as “Shamel” or “Lumma.” It primarily targets cryptocurrency wallets and two-factor authentication browser extensions before ultimately stealing sensitive information from victims’ machines. Capable of targeting Windows operating systems from Windows 7 to Windows 11, Lumma has seen a 369% rise in detections between H1 and H2 2024.
Lumma stands apart because of its modular structure and frequent updates that enhance its evasion capabilities, including recent updates to use the ChaCha20 cipher for configuration decryption. The CRU observed Lumma being loaded in incidents involving Emmental, a little-known loader used by multiple financially motivated threat actors since February 2024 to deploy commodity RATs and infostealers.
HijackLoader has also emerged as a significant threat, delivering Lumma Stealer alongside other malware families. Recent threat intelligence from April 2025 shows Lumma remains among the top malware threats, spreading through phishing campaigns, malicious websites, and social engineering tactics, including the ClickFix method, where users are tricked into executing attacker-provided PowerShell commands.
Adversary
Infrastructure
Victimology
Capabilities