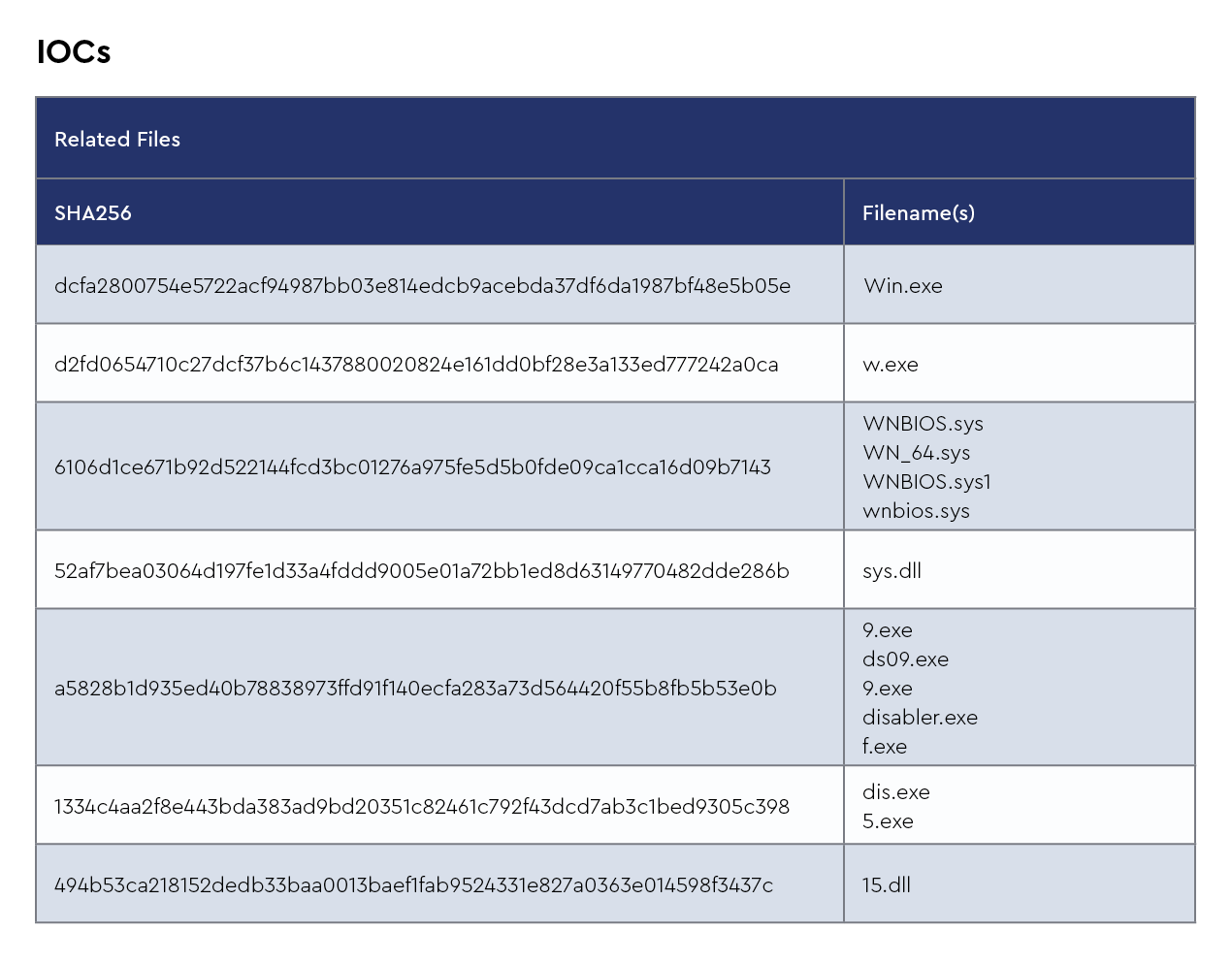
Welcome to the latest edition of the monthly threat brief published by the ConnectWise Cyber Research Unit™ (CRU). In this threat brief, we will provide raw data statistics, intel on the most common malware seen this month, and a list of new detection signatures added to the ConnectWise SIEM™ throughout December.
For a more detailed explanation of the overall trends and analysis of these numbers, check out the 2024 MSP Threat Report. For comparison, December’s threat brief can be found here.
January stats
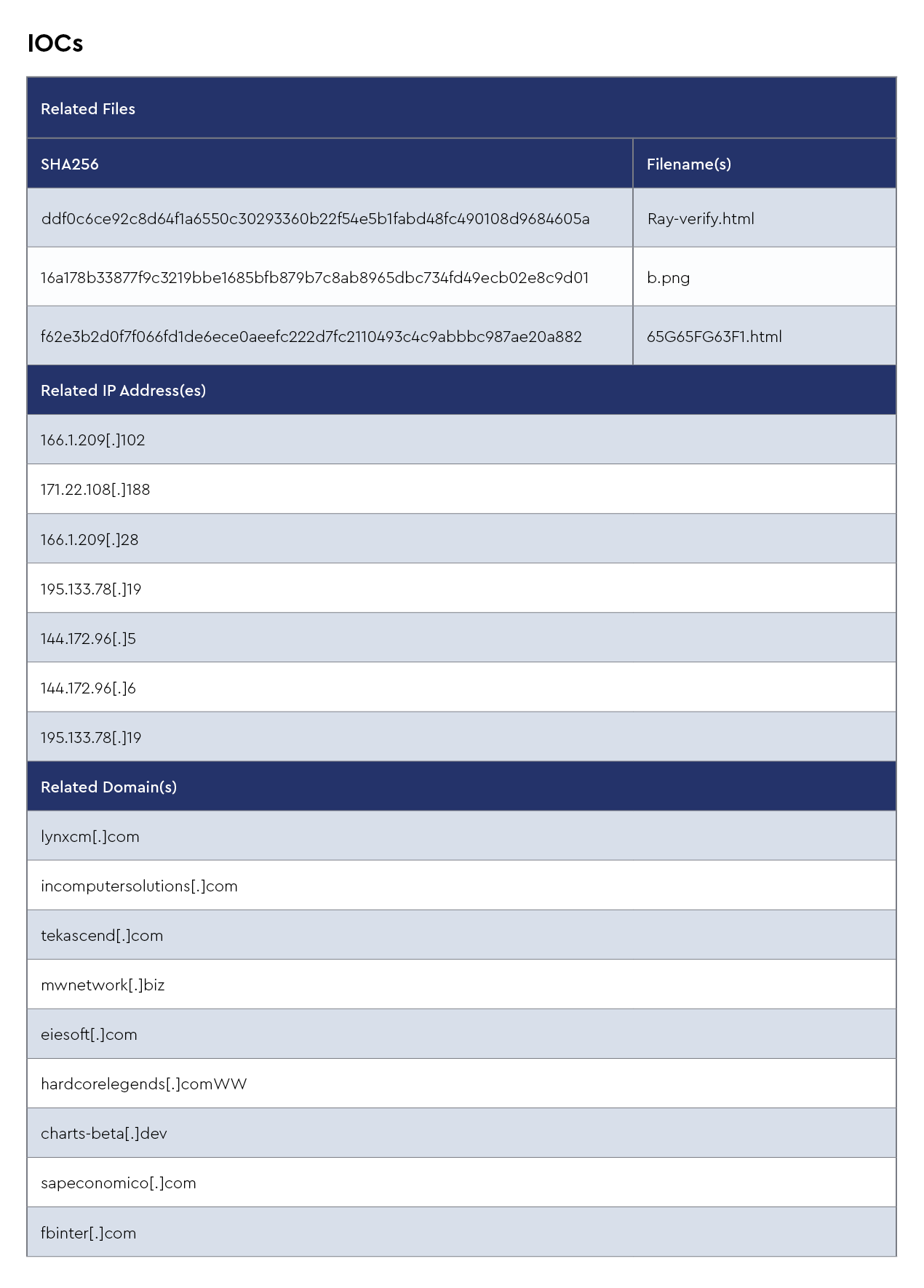
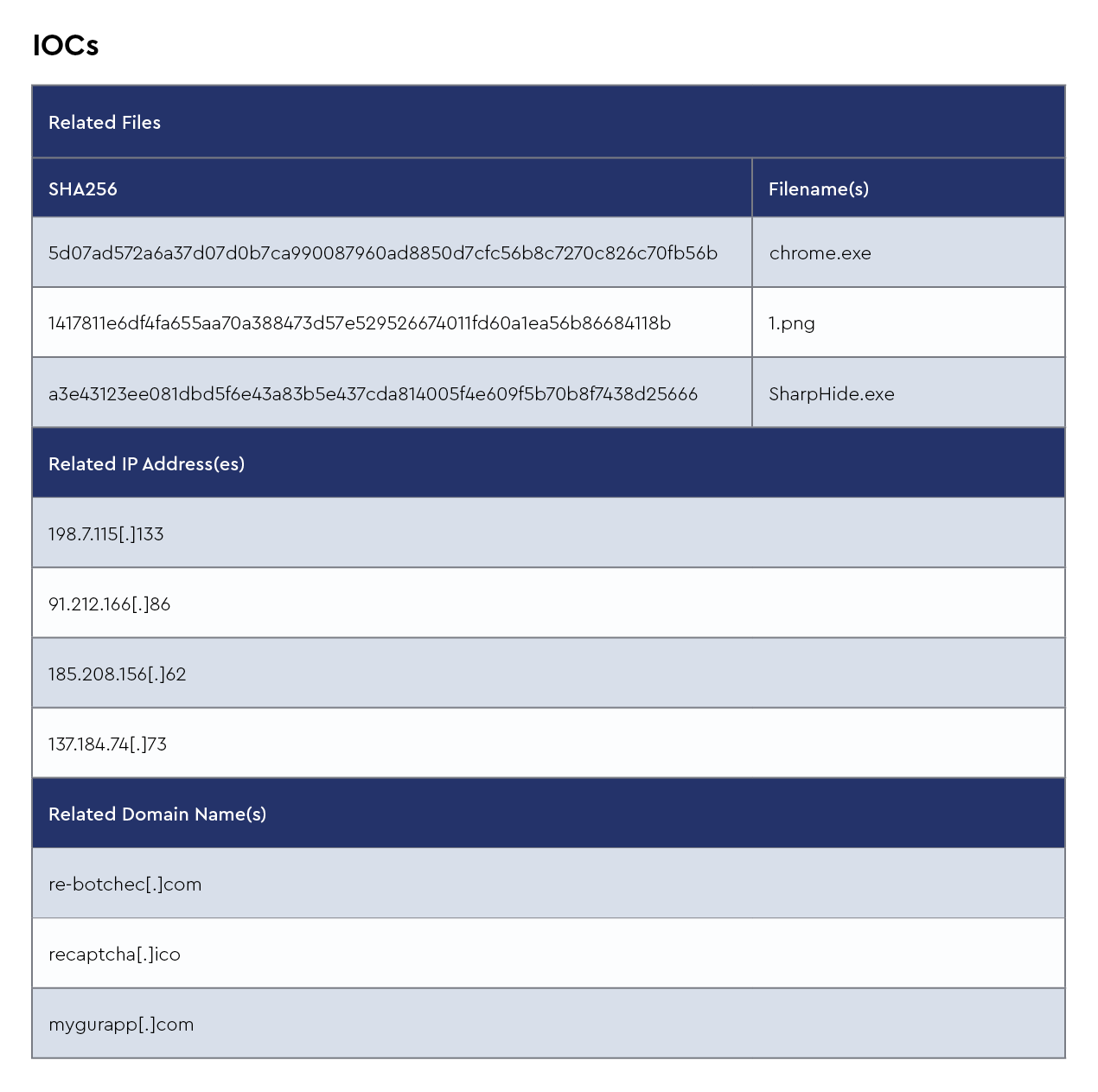
IOCs
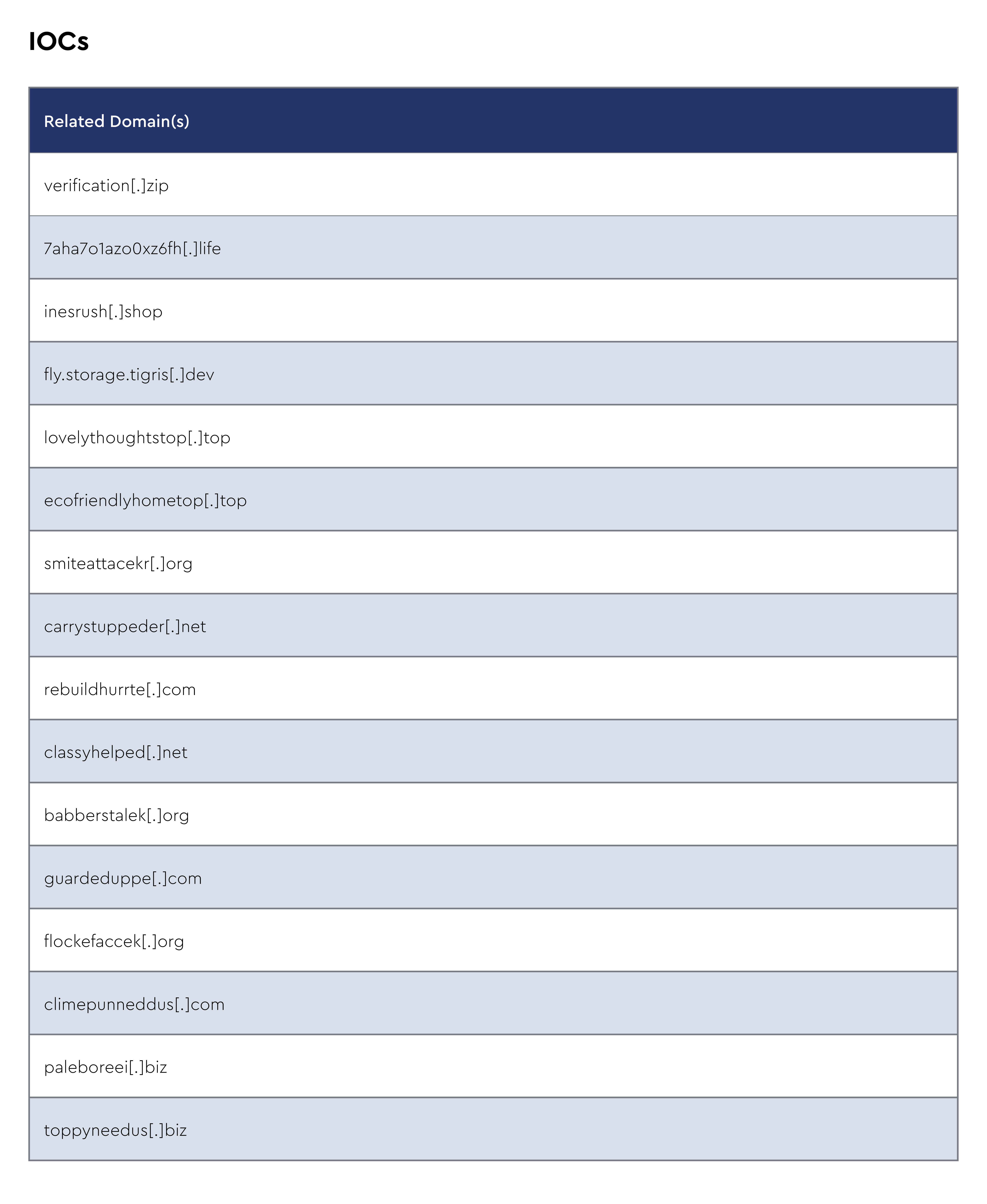
The CRU collects indicators of compromise (IOCs) from public open-source intelligence (OSINT) sources and any cybersecurity incident escalated by the ConnectWise security operations center (SOC). These IOCs are used for automated threat hunting and data enrichment to assist SOC analysts. Below is a summary of the IOCs collected.
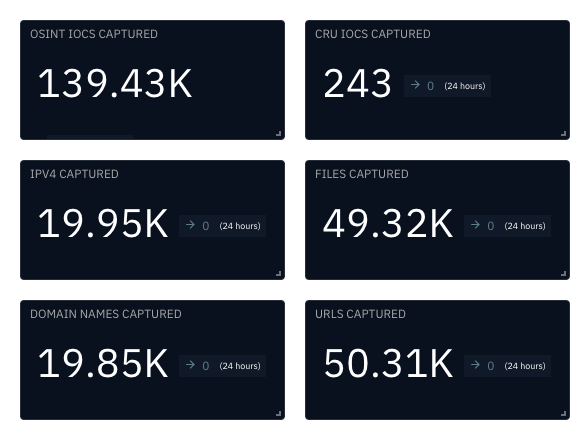
Figure 1: Summary of IOCs collected in January 2025
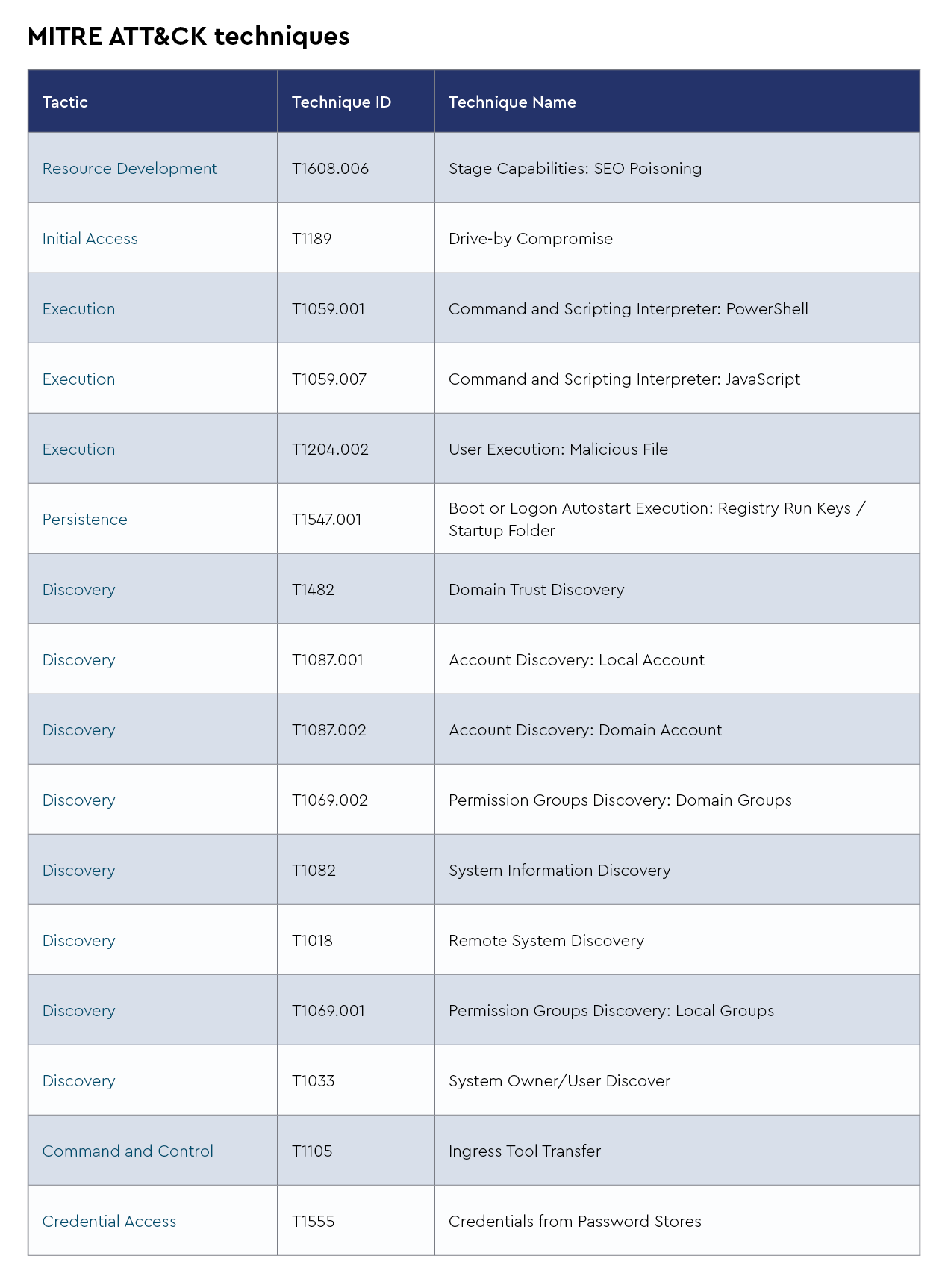
TTPs
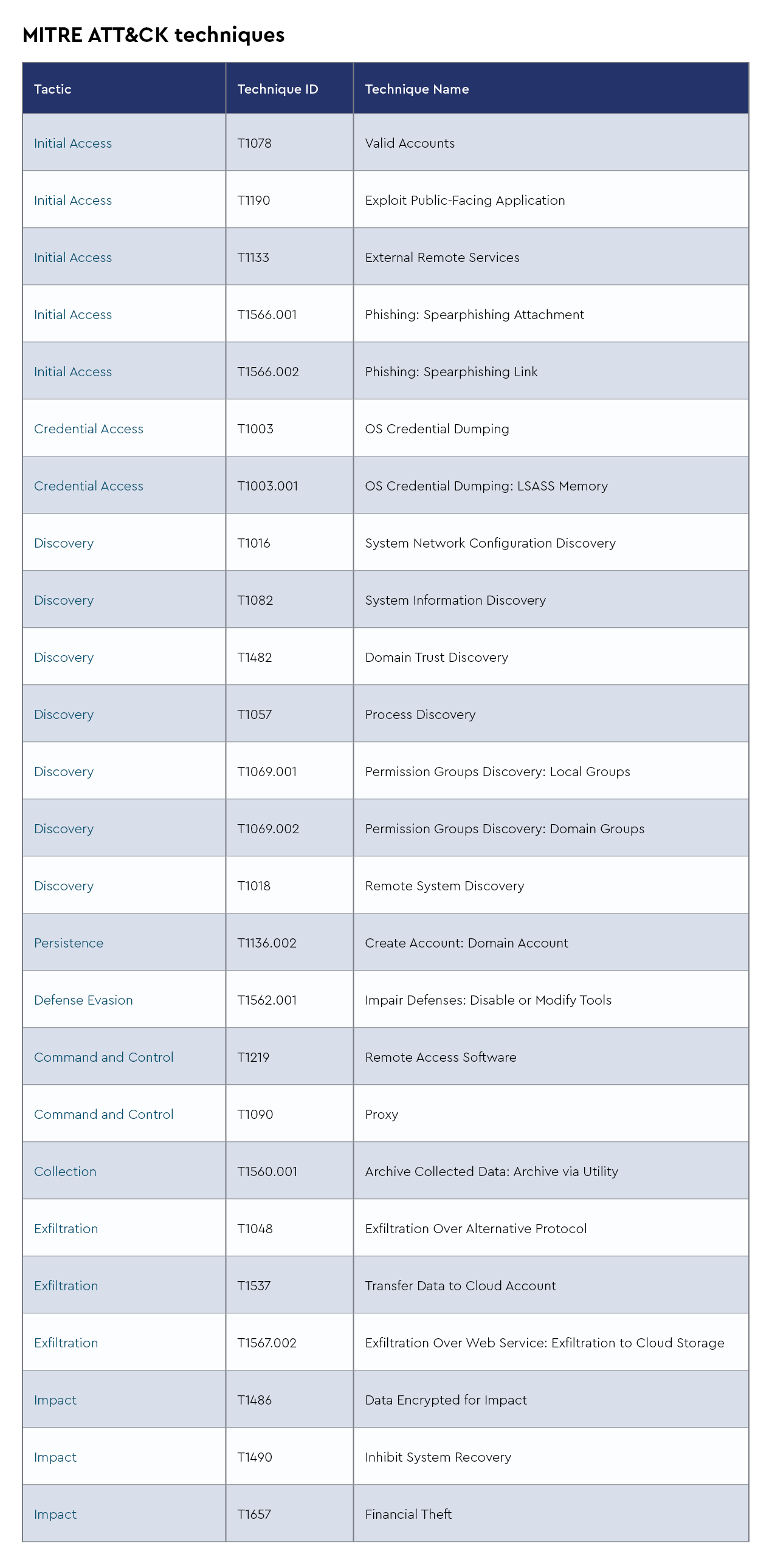
The CRU collects tactics, techniques, and procedures (TTPs) from all incidents escalated by the ConnectWise SOC. This information helps us keep tabs on how threat actor behavior changes. Below are the top 10 MITRE ATT&CK® techniques for December 2024—provided for comparison—and January 2025.
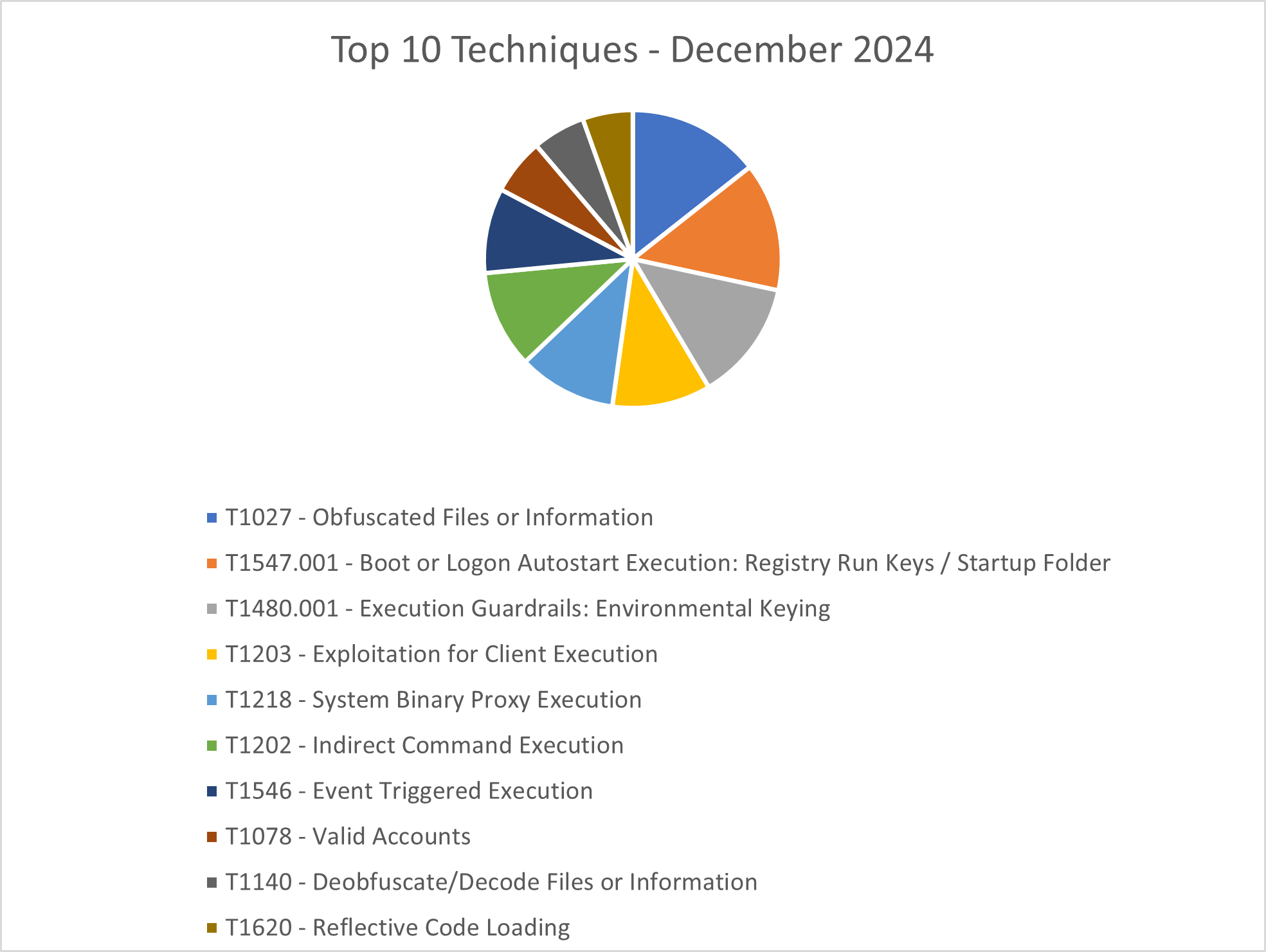
Figure 2: Top 10 MITRE ATT&CK techniques observed in December 2024
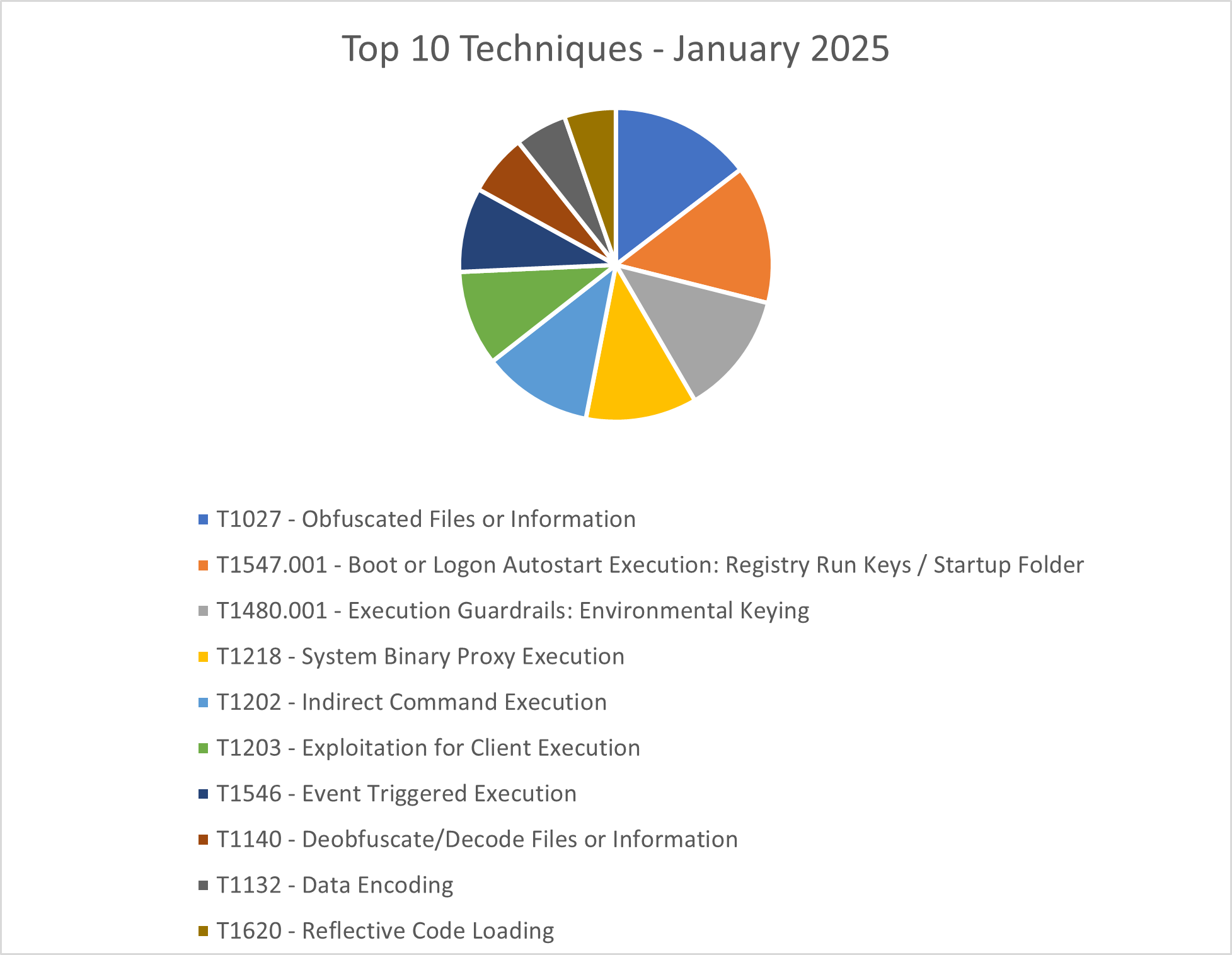
Figure 3: Top 10 MITRE ATT&CK techniques observed in January 2025
Latest threats
Each month, we highlight threats that we have seen targeting our managed service provider (MSP) partners and their clients.
Malware

Figure 4: Top five malware observed in January 2025
Lumma Stealer
Lumma Stealer, also known as LummaC2, is an information-stealing malware written in C that has been available through a malware-as-a-service (MaaS) model on Russian-speaking forums since at least August 2022. Developed by a threat actor known as "Shamel" or "Lumma," this malware specializes in exfiltrating sensitive data from compromised systems, including passwords, browser information, cryptocurrency wallet details, and two-factor authentication (2FA) browser extensions.
Once the targeted data is obtained, it is exfiltrated to a command-and-control (C2) server via HTTP POST requests using the user agent "TeslaBrowser/5.5." Additionally, Lumma Stealer features a non-resident loader capable of delivering additional payloads via EXE, DLL, and PowerShell.
The malware employs various deceptive distribution methods to infiltrate systems. Recent campaigns have utilized fake CAPTCHA verification pages, where users are tricked into executing malicious PowerShell commands disguised as legitimate human verification steps. Other tactics include distributing the malware through telegram channels offering pirated software, torrents with pirated TV shows, and YouTube videos promoting cracked software.
These methods exploit user trust and the popularity of certain platforms to propagate the malware effectively. The persistent and evolving nature of Lumma Stealer underscores the importance of robust cybersecurity measures, including user education, up-to-date antivirus solutions, and cautious interaction with unsolicited or suspicious online content.
NetSupport Manager RAT
NetSupport Manager RAT is a program that enables users to manage and control other computers over a network. It functions as a “remote access trojan,” and while it’s intended for legitimate uses such as technical support and corporate network management, it can also be misused.
The software offers various features, such as:
- Remote desktop control: Gives an administrator full access to the target computer’s screen and inputs
- File transfer: Allows moving files between the computers
- System inventory: Provides details about the target computer’s hardware and software
- Hardware and software monitoring: Tracks system performance and installed applications
- Chat functionality: Facilitates communication between the administrator and the target computer user
NetSupport Manager RAT operates by installing a client component on the target computer and a control component on the administrator's computer. These components communicate via a network connection, enabling the administrator to access and control the target computer. However, remote administration tools, including NetSupport Manager RAT, can be used for malicious purposes. Cybercriminals frequently use similar software to infiltrate computers, steal confidential information, or carry out harmful activities without the user's knowledge or consent.
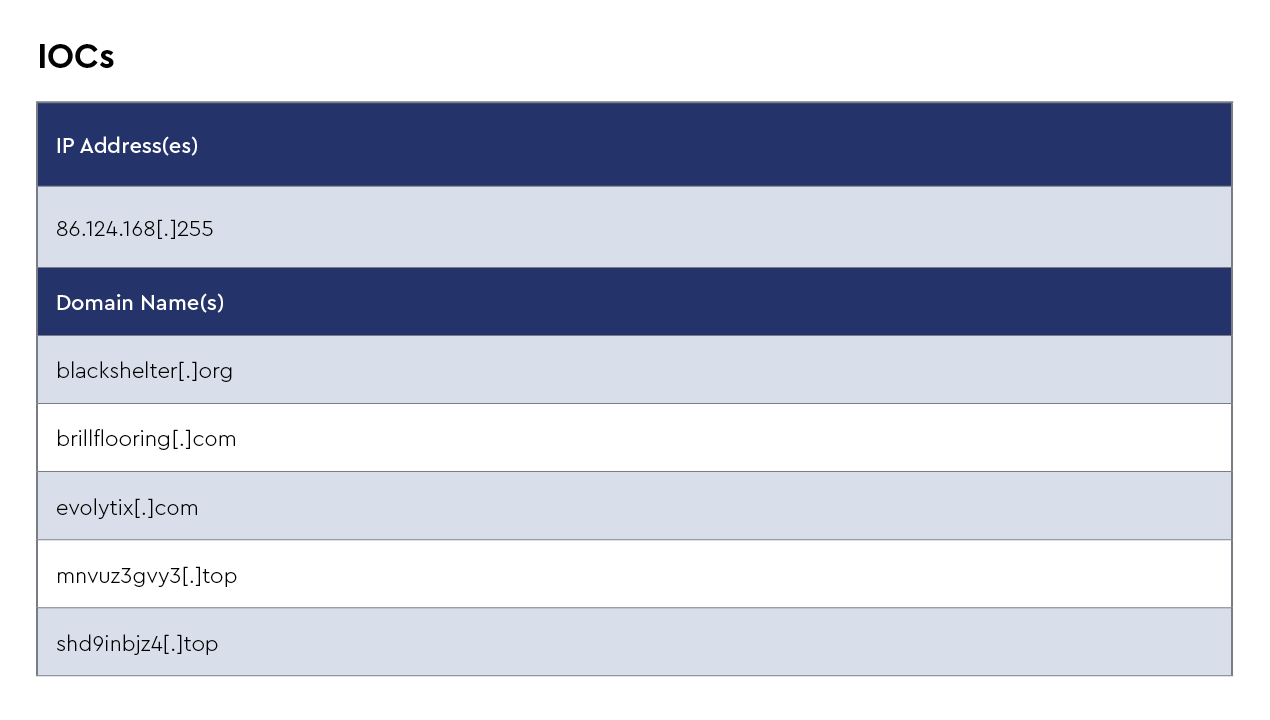
FAKEUPDATES/FakeUpdates/SOCGholish
FakeUpdates, also known as FAKEUPDATES or SocGholish, is a prevalent malware campaign that emerged around 2018. It is characterized by its use of social engineering techniques to trick users into downloading malicious software disguised as legitimate updates. This malware is primarily delivered through compromised websites, where users are prompted with fake update notifications, typically for common software such as Adobe Flash Player or browser updates. These prompts are designed to appear authentic, exploiting users' trust and urgency to keep their software up-to-date.
Once the user initiates the download, the malware installs a backdoor on the system, providing attackers with remote access and control. FakeUpdates is often used as a delivery mechanism for additional payloads, including ransomware, banking trojans, and information stealers. The attackers leverage this access to exfiltrate sensitive data, deploy further malware, or use the compromised systems for broader campaigns.
The widespread use of compromised legitimate websites and the convincing nature of the fake update prompts make FakeUpdates a significant threat, capable of impacting a wide range of users and organizations. Its persistence and adaptability in evading detection underscore the importance of robust cybersecurity practices and user education to mitigate such threats.
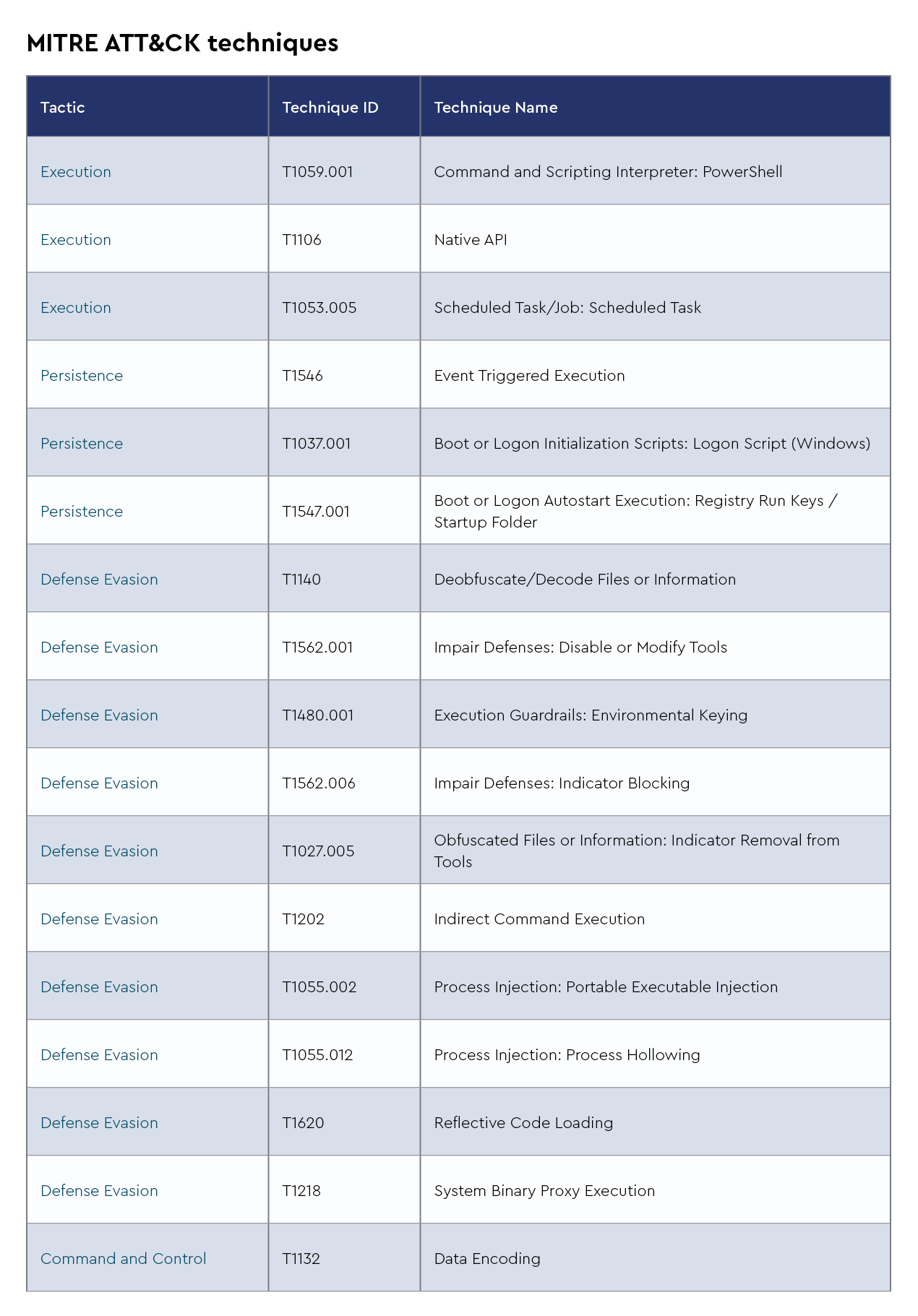
XWorm
XWorm is a remote access trojan (RAT) that has been gaining traction among cybercriminals due to its versatility and stealth. Distributed primarily through phishing emails and malicious attachments, XWorm enables attackers to take full control of an infected system. Once installed, it provides remote access, allowing for keylogging, screen capturing, data exfiltration, and the ability to run arbitrary commands. XWorm is lightweight, which makes it harder to detect, and is often obfuscated to avoid antivirus detection. It can spread laterally within a network, making it particularly dangerous for corporate environments.
Recent intelligence suggests that XWorm has been updated with additional functionalities, including more advanced evasion techniques and modular components that make it adaptable to various attack scenarios. Cybercriminals are increasingly using it in targeted attacks, often against organizations with weak email security controls. There have been reports of its use in financial sector attacks, where XWorm was deployed to steal credentials and banking information. Furthermore, the malware has been spotted in campaigns linked to both espionage and financial gain, indicating its growing popularity among different threat actors. Its evolving capabilities and widespread availability on underground forums make it a persistent and adaptable threat.
Akira
Akira is a ransomware group that emerged in early 2023, operating under the ransomware-as-a-service (RaaS) model. It quickly gained attention due to its effective use of double extortion techniques, where attackers not only encrypt victim data but also exfiltrate sensitive information, threatening to leak it if ransom demands are not met. Akira's ransomware payloads are often customized for each attack, and the group has been observed targeting a wide range of industries, including healthcare, finance, and education. They exploit vulnerabilities in remote access services such as VPNs and RDP to gain initial access to networks, often after weak or compromised credentials have been used.
Recent intelligence indicates that Akira has been increasing the frequency and scale of its attacks. The group is known for its aggressive negotiation tactics, sometimes demanding multi-million-dollar ransoms. Reports have linked Akira to attacks in multiple countries, targeting both small and large organizations. They have been particularly focused on Western targets, where they believe ransoms are more likely to be paid. Akira's adaptability and ability to evade detection by disabling cybersecurity tools during attacks make them a growing threat on the ransomware scene.