Your security stack is the foundation of your client’s cybersecurity protection. Whether you’re building a stack from scratch or making updates and changes to your existing setup, it’s a task that needs to be done correctly and with cybersecurity best practices in mind.
Building your cybersecurity stack effectively is a balancing act. In theory, it’s easy to assume that the more tools you include, the better your protection will be. While this is true to a point, there is a point of diminishing returns.
Along with that, adding too many tools can make your stack overly complex and, ultimately, leave your client’s system open to vulnerabilities. The goal is to build an IT security stack that includes as many useful tools as possible but doesn’t take away from its primary purpose.
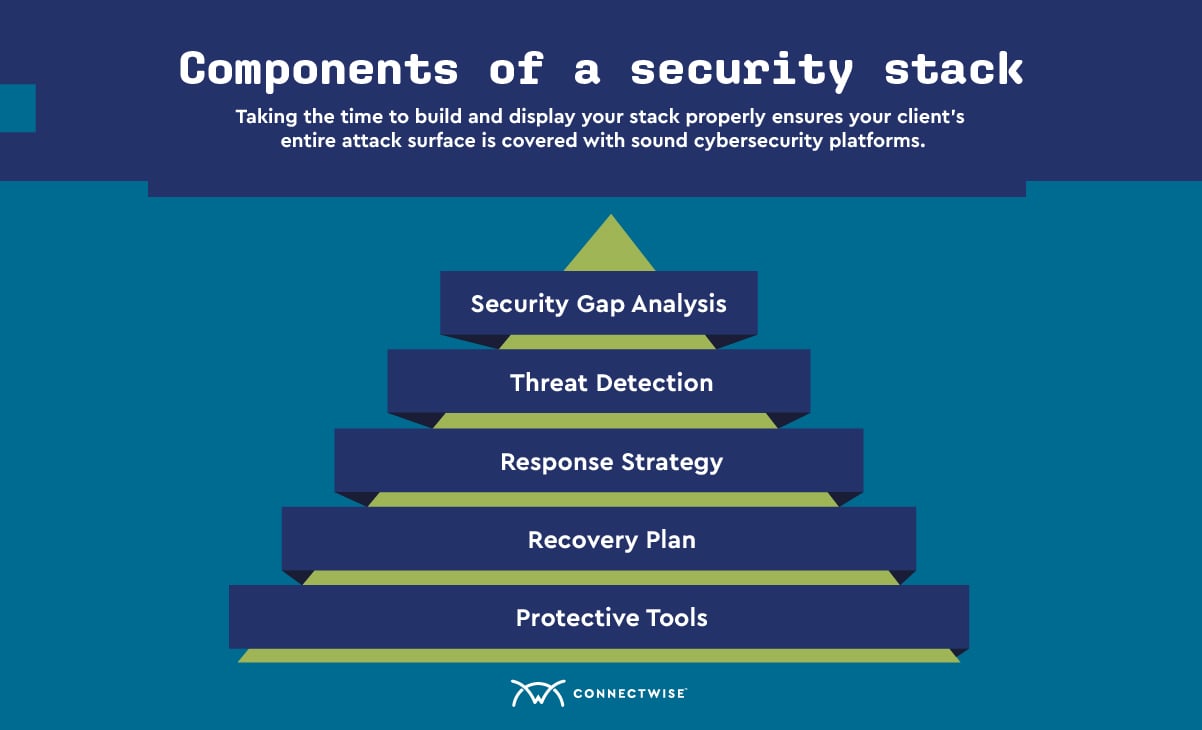
Your security stack serves as both an inventory and a roadmap of your cybersecurity tools. A proper stack should allow you to see all the tools you have at your disposal, the tool’s primary function, and the systems it interacts with within your network. Each organization’s stack will be different, but it’s generally a best practice to display this “roadmap” in layers.
Displaying this information in a layered visual format allows MSPs to understand what tools they have, what tools they need, and where they may have potential vulnerabilities or loopholes in their protection. Tools within an MSP’s stack can easily be overlooked or “lost in the shuffle” because of the sheer number of tools involved in proper cybersecurity protection. Taking the time to build and display your stack properly ensures your client’s entire attack surface is covered with sound, updated cybersecurity platforms.
The first step in properly building your security stack is assessing your needs. More specifically, for MSPs, you’ll need to put yourself in your client’s shoes. What issues are they most likely to face? What protections will ultimately be most important to them?
In general, there are 6 areas of business risk most organizations are likely to face:
Keep these 5 key areas in mind as you assess your client’s current cybersecurity infrastructure and look for opportunities to optimize your security stack.
Cybersecurity experts agree that security stack best practices necessitate a layered, balanced approach.
Your network security stack will differ significantly from the tools you use to protect against data breaches. With this said, while each facet of your client’s overall network is different, your layers of protection should build on one another to provide a solid overall shield of protection.
There also needs to be a balance among these levels to maximize the effectiveness of your stack. The concept of “balance” will look different from client to client based on the structure of each company.
For example, a particular client may be more concerned with protecting large amounts of data and intellectual property. As a result, their cybersecurity concerns may focus primarily on backup for vulnerable system areas and data breach protection.
Tech companies like SaaS providers conduct most of their business online, in the cloud. This naturally makes their security concerns much different than our first example. Since they live in the cloud, their server uptime is what directly affects their business. Subsequently, DDoS protection may be their primary concern, where they focus most of their cybersecurity dollars.
MSPs should run their client’s systems through a risk assessment or gap analysis to get a clear picture of where they lack proper protection. An in-depth evaluation should uncover system hardware, software, data, and more vulnerabilities.
Once you determine the analysis results, you can compare these results against a standard cybersecurity framework. The NIST framework provides a good benchmark for what your client’s cybersecurity should cover. Over time, you can take learnings from previous assessments and continually bring them back to the NIST framework to optimize your client’s protection in the long term.
Note that NIST is not the only framework available, though, especially internationally due to different compliance standards. For example, in the UK, the primary benchmark is Cyber Essentials. In Australia, Essential 8 is a popular framework. Your team can look around to find what framework makes the most sense.
For more information about proper risk assessments, gap analysis, and cybersecurity frameworks, feel free to contact us. We can give you the insight and tools to tackle more in-depth questions if they arise.
Early and efficient threat detection is an essential component of effective cybersecurity protection. Detection planning builds a detection workflow into your security stack. This level of planning outlines how incoming threats will be prioritized and managed. It will also dictate which key team members are to be notified in the event of each threat type.
Generally, there are two types of detection MSPs need to concern themselves with:
Your detection plan will involve a combination of both types of detection. Ultimately, it will give your team a detailed workflow on what to do and who will be notified of any threat that may emerge.
Effective detection plans typically follow these 6 steps:
There are 6 key steps to consider when building your response strategy:
No security stack is complete without recovery. Identifying and mitigating a threat is great, but what’s the point if you can’t restore your client’s system and data to pre-event status? Reliable backups are necessary to ensure your clients don’t lose countless customers and revenue because of one attack.
Security frameworks like the NIST Cybersecurity Framework are helpful in the recovery process, but MSPs need to think deeper. Extra care should be taken to work with your client’s employees and implement a cybersecurity education program across departments. Something as simple as sending fake social engineering attacks like phishing emails can be enough to keep employees educated and on their toes.
Additionally, IT managers should require employees to update their passwords constantly. The IT team should also be required to attend regular briefings on the latest hacker threats, tactics, and procedures (TTPs).
The best form of recovery is preparing both IT and non-IT employees in the first place, both for present and future needs. As the saying goes, “An ounce of prevention is worth a pound of cure.” For a more detailed look at how backup and data recovery businesses can grow, read our resource article, 4 Best Practices for Scaling Your BCDR Business.
One thing remains constant no matter how different security stacks can be. That constant is the fact that you need to use the right tools. As we mentioned, it’s easy to become overwhelmed by the wealth of options and include too many tools when building your stack.
Here are 5 must-have tools when building your security stack (in alphabetical order):
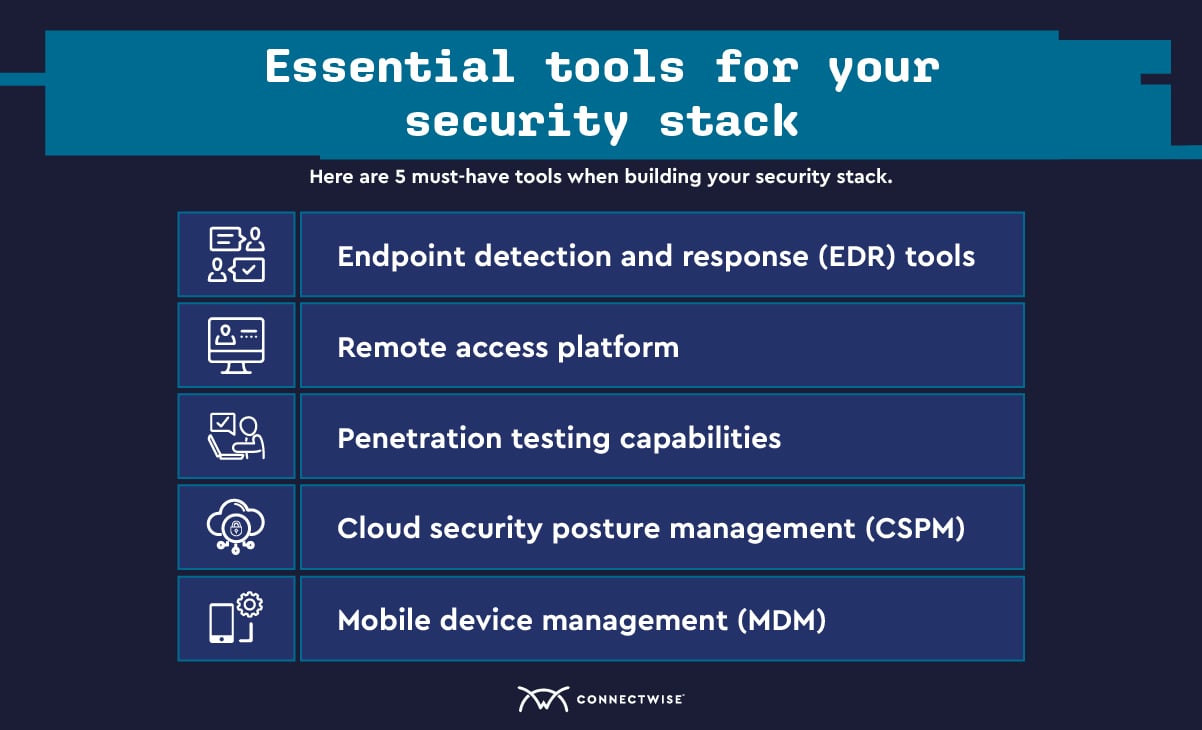
MSPs can find more information on various cybersecurity tools and how they fit into your overall stack in the ConnectWise cybersecurity center. We’re here to provide whatever resources you need to help protect your clients.
What better way to accomplish this through trying it yourself? ConnectWise offers free trials of all of our major tools to find the fit for your security needs.
A security stack is an inventory and roadmap of an organization’s cybersecurity tools. It covers all the cybersecurity tools an organization has, their function, and the specific systems they interact with.