Innovative hacker TTPs that cause disastrous data breaches are constantly covered in the news. While it’s important to protect against these outside threats, all this focus on said outside threats may leave the health of your clients’ internal system components themselves to slip through the cracks.
Subsequently, processes like OS hardening become critical to optimizing the effectiveness of your cybersecurity efforts. For that reason, we’re going to take an in-depth look at OS hardening and why it’s an indispensable component of your MSP business.
OS hardening is the process of using patching and other security measures to improve the security of a server’s operating system. This advanced cybersecurity protocol comes in the form of a software application that MSPs or IT admins need to run on the system to install these crucial updates.
Oftentimes, data protection and OS hardening are discussed simultaneously, but both are very different procedures. OS hardening focuses on increasing the protection of a system’s software and hardware assets while data protection simply focuses on having a robust backup procedure in place to replace lost, damaged, or corrupted data in the wake of a cyberattack.
The most efficient way to run OS hardening procedures is to have them implemented automatically by your client’s system. Typically, OS providers will include native notifications within their system to remind users to make these all-important updates.
While OS hardening itself is vitally important, this software is actually just a small part of the overall system hardening process. Savvy MSPs know that their client’s IT estate needs to be protected from every angle, and combine OS hardening with other techniques and updates like:
Each of these processes plays its own role in protecting the sum of your client’s IT assets — and is necessary in its own way. But, making sure to include these in your client’s overall protection plan is only half the battle.
Additionally, you’ll need to deftly manage the patches for each facet of your client’s system to ensure seamless integration. Download our free Patch Management Best Practices eBook or contact us to get the most out of the patch and update process you use to serve your clients.
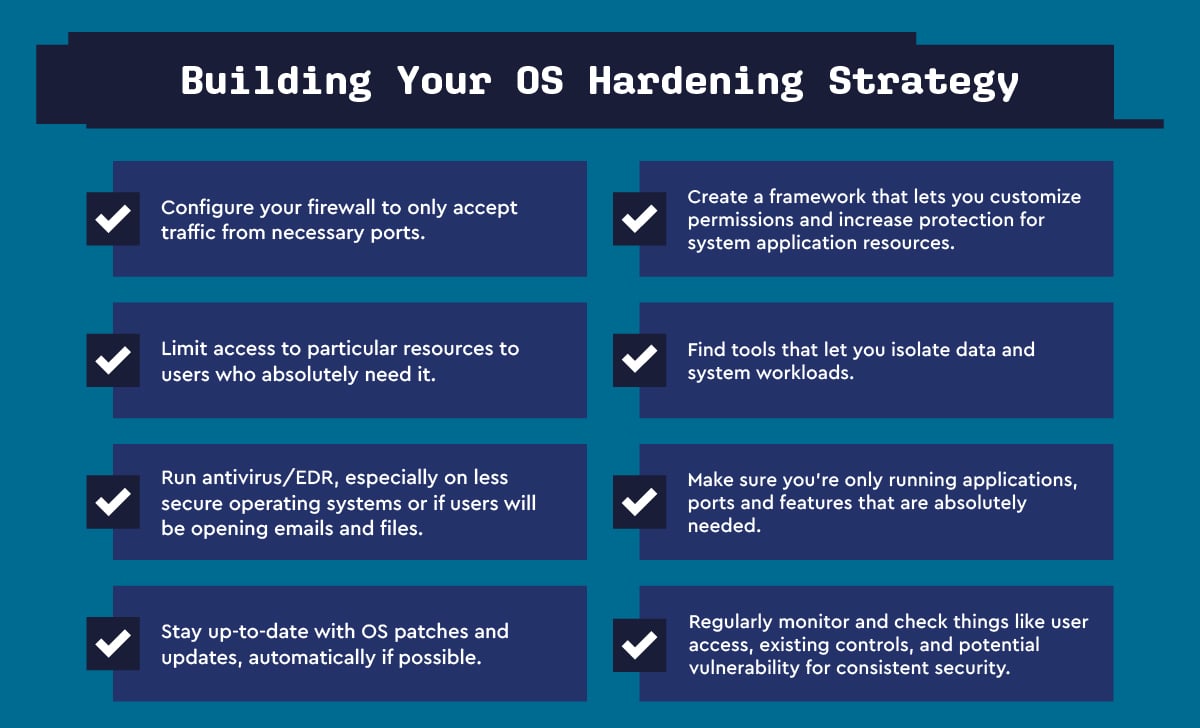
As an MSP, your end goal should be to make your client’s system bulletproof. Each item on your overall OS hardening checklist should be geared toward maximizing system protection at every level.
Configuring your client’s OS to the highest level of protection, executing system updates punctually and efficiently, implementing policies and procedures to help securely govern their system, and removing unnecessary apps and platforms are all part of the process. Ultimately, a foolproof OS hardening procedure is meant to minimize the exposure of the system’s backbone – the operating system – and stay ahead of any risks or problems before they start.
As mentioned earlier, OS hardening is just a small part of your complete system hardening process. To gain the true benefit of what OS hardening is, you’ll need to implement it in conjunction with:
Application hardening is the process of updating all your client’s internal and third-party software apps. This process aims to leverage software-based security measures to increase the overall security of the server and network.
Some steps to consider implementing during your application hardening process are:
The data, ports, everyday functions, and components of your client’s servers can also be exposed to threats. Since servers are arguably the most critical component of any IT system, protecting them at every level is an essential part of cybersecurity.
The server hardening process is designed to protect a system’s servers at the software, firmware, and hardware level. Some techniques to consider implementing during this process include:
Allowing a hacker access to just one database of information can be a veritable gold mine for them – and a nightmare for your clients.
Securing these valuable databases and the overall management system controlling them generally involves three steps:
Several effective techniques could be used to handle each of these three aspects. Here are a few options available to help boost your clients’ database protection:
To protect data in transmission, MSPs need to focus on protecting the network – the structure responsible for an IT system’s communication. The two most effective ways of accomplishing this are through either an intrusion detection system (IDS) or an intrusion prevention system (IPS).
An IDS or IPS is a software application that will scan your client’s network for suspicious activity. And while these applications are incredibly effective, they’re at their best when paired with other network hardening practices.
In addition to using an IDS or IPS, MSPs should also be:
All of these supplementary tactics go a long way toward bolstering the performance of an IDS or IDP and, ultimately, hardening and protecting your clients’ networks.
The benefits of OS hardening are as broad and far-reaching as your client’s network itself. Because all departments are leveraging a company’s IT assets, protecting those assets can have a hand in improving all aspects of a business.
Some of the benefits your clients can expect to receive from your OS hardening protocols are:
While some clients may hesitate to take the leap and incur the extra expense of your OS hardening services package, outlining these benefits is an easy way to show them how worthwhile it can be in the long run.
When it comes to the three main operating systems – Windows, Linux, or macOS – they each can accommodate varying levels of cybersecurity. One of the reasons for this is that each platform has its own OS hardening standards.
Windows is widely considered the least secure of the three. Experts cite a lack of innovation and security standards on the part of Microsoft as one of the main culprits. Additionally, enterprise-level Windows systems tend to leave organizations with heavy exposure to digital attacks and large attack surfaces.
As we move up the spectrum toward more secure options, MacOS is next. This is due, in part, to the fact that the overwhelming majority of computer users chose Windows for decades. However, in recent years, Apple’s share of the market has been growing. As a result, digital threat actors are beginning to set their sights on Mac targets more often.
Another reason for Mac’s increased security is that Mac devices come out of the box with very few network services connected. Therefore, Mac computers in their default state are very secure. But, this may change once users power them on, personalize them, and connect peripheral network services.
Finally, we have Linux. Linux OS is different than Windows or macOS in that it’s open-source. While you might think this exposes it to more vulnerabilities, it’s actually the opposite.
Since Linux is open-source, its community of users contributes to its cybersecurity. With a community of millions of users reviewing Linux code and constantly issuing Linux patches and updates, the Linux OS remains highly secure and stays ahead of the newest hacker trends and techniques.
Now that you understand the importance of OS hardening, it’s time to implement a foolproof hardening process for your managed IT service clients. Here is a brief OS hardening checklist to get you started:
ConnectWise is here to help. Feel free to contact us with any questions you have regarding MSP services. We have you covered from basic to advanced needs, and our suite of cybersecurity tools is bound to have something that’s easy to implement and gives your clients all the cybersecurity protection they need.