Installing a Small Perch Sensor for the SMB, Seamlessly
Are you worried about those pesky hackers getting into your network and owning your devices? Have you ever wanted enterprise-grade detection capabilities on your small residential or commercial network? Do you search the internet regularly looking for the latest TTPs the bad guys are using (like the ones outlined in our weekly threat reports) and wish you could use that info to hunt for threats in your network? The good news is, you can! I’m here to help you figure out how.
It’s dangerous to go alone, take this with you

This post is intended for the folks who like to consider themselves “power users”, but who may not have a full-on enterprise-grade network with all the bells and whistles that a multi-million-dollar company can afford. If you feel like this applies to you, look no further. You’re in the right place. You should also know that you’re not alone. Y’all deserve all the protection the big boys get, even though you may not have the same budget they do.
Here at Perch, we believe that good security should be easily available for everyone, small and medium sized businesses included. This is why we offer a solution that can scale from the smallest to the largest of customers, with a similar experience for everyone.
Our sensors and software can be found everywhere, from the smallest home networks (like the one in my apartment), all the way up to large financial institutions with an annual recurring revenue of over five billion dollars. I’m going to assume the bigger organizations don’t need my help figuring this stuff out. So, I’m just going to focus on what is required to setup a tiny form factor sensor (pictured above) in a small residential network with some commercially available, low-cost equipment.
So, what’s required to get setup and running with a Perch sensor?
Turns out, not a whole lot.
Assuming you’ve already got your network topography in place, it’s really quick and easy to get setup. It doesn’t require an advanced level of knowledge to setup either (if you can use a Roku, you can setup a Perch sensor). It’s not something that requires a massive network overhaul where you have to take everything down (and pray that it comes back up). It takes about 20 minutes to setup the sensor. We can Uber Eats you lunch, and you’ll have your sensor setup and running before your food gets there.
Feeling empowered and inspired yet? Good, you should be 😀.
The only network equipment necessary to drop Perch in on your network is simply a switch with the ability to enable port mirroring. We ideally like to sit behind a firewall, so we can see what makes it past the perimeter defenses. But it’s not required to get setup with us. This write up is going to assume you’re setting it up on a small home network, running a firewall at the perimeter behind the modem, and before the switch.
Besides a switch capable of port mirroring, you’ll really only need an internet connection plus a device that handles traffic routing upstream of the switch. In this case, I’m just using the modem provided by the ISP which handles the DHCP for the whole network upstream of the switch that is mirroring out traffic to the Perch Sensor. The cool thing about doing it this way is I’m able to retain the enhanced services from my ISP that include user analytics profiling abilities, metrics collection capabilities, as well as rogue device detection functionality.
If you don’t have a switch capable of port mirroring, a good economical solution might be a managed smart switch like the TP-Link SG105e. This little 5 port switch is really all you need, with room to spare. One port to bring in the traffic from the modem, one port to forward the traffic back out to any other switches or routers downstream (such as your wireless AP), and two ports for the Perch sensor (one to setup as a mirror/tap, and one so the sensor can connect back to the Perch cloud.) You’ll even have a whole port free to leave you room for growth.
Below is a visual of the topography described above:
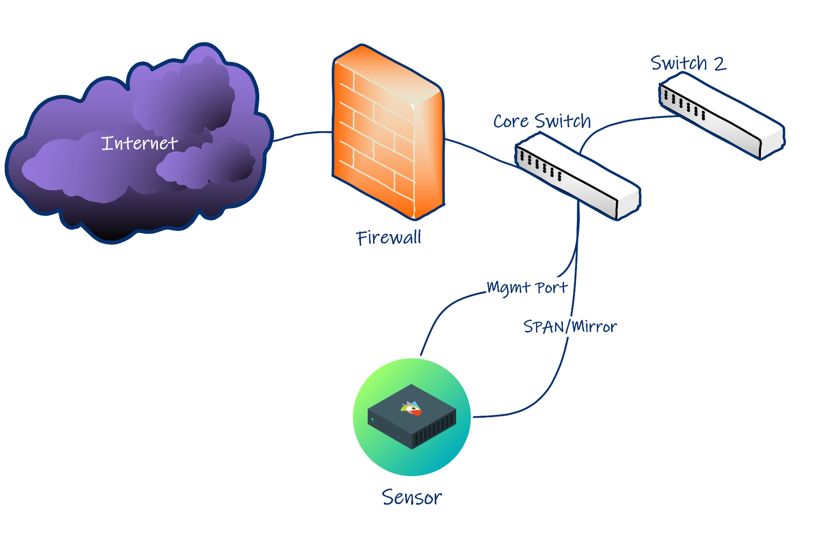
(in my use case switch 2 is both a switch and a wireless AP)
Some pro tips:
One thing that helps a lot before you embark on the setup process, is making sure you have a solid asset management list that documents all the machines that are supposed to be on your network (#1 on the SANS 20 Critical Security Controls). Make sure you document their MAC address and their static IP (if you want to give them one or if they have one pre-configured). Most ISP supplied modems will have their own subnet DHCP pool that’s pre-defined, and their modem will have a static IP assigned on that subnet outside of the DHCP range. I highly recommend giving your switch and access point a static IP address as well and assigning your DHCP range to not include those addresses. Personally, I also give some devices (such as my Xbox One) a static IP for many reasons. One of which is to make the network as fast as possible for pwning n00bz on Xbox Live.
I could go over all the specifics of how easy it is to install the TFF sensor, but why re-invent the wheel when anything I would put here has already been extensively documented in our help pages. There you should find any additional information you could possibly need to get yourself setup. Of course, we don’t have a problem with hopping on the phone with you to help you get it figured out if you need some assistance. But I believe in your ability to do it yourself.
Now you’re ready:
The great thing about what we offer here at Perch is the fact that you don’t have to be an expert to be able to get us setup on your network, nor do you have to have a full security team to triage the alerts that our sensor generates. We’ve taken care of all that for you. Between our great, service-oriented Customer Success team, and our extensive documentation on how to get setup and running, you’ll wonder how you ever lived your life without us to begin with.
Get flocked up!
Here at Perch, we try to make security easy, because it’s already hard enough. If it’s this easy for the little guys, just imagine how painless it will be if you’re an MSP trying to manage multiple small organizations, or if you’re a bigger shop with lots of remote locations you need to monitor. Our solution is applicable for a wide variety of use cases. We look forward to hearing from you about how we can work with you to help you address your security needs.





