Modern society gives birth to modern crimes. Unfortunately, that means criminals and threat actors of the day are attempting to harm users as they browse blogs, shop online, and scroll social media on their smartphones. As a result, digital forensics is becoming a growing, necessary part of how our world works.
But what is digital forensics? How does it work? Discover the answers to these two questions and more by diving into the article below.
What is digital forensics?
Digital forensics – or computer forensics – is the science of manipulating and analyzing digital data to be used as evidence in a court of law.
This data can come from any number of electronic sources, including a laptop, computer, smartphone, server, or data network. Professionals in this field cooperate with a larger forensics team to aid in navigating, inspecting, and analyzing these data sources in a larger criminal investigation.
What are the branches of digital forensics?
There are five different branches to consider within the broader field of digital forensics. Although digital forensics is sometimes called cyber forensics, the process doesn’t solely deal with computers.
The five main branches of this important criminal science are:
- Database Forensics – focusing on databases and associated metadata, database forensics handles multiple aspects of data. Investigators may analyze transactions within a database, or review timestamps to verify a particular timeline of user interactions.
- Computer Forensics – solely focuses on evidence found on computers and in digital storage media. This branch combines traditional data recovery measures with proper legal procedures to support both criminal and civil cases.
- Network Forensics – this is the most fast-paced branch of digital forensics. Once data has been transmitted across a network, it’s gone. As a result, network forensic investigations tend to be more proactive than reactive.
- Mobile Device Forensics – the increased use and intricate nature of mobile devices has increased demand for professionals in this branch. This style of forensics involves navigating complex technologies like GPS and hibernation in any device with internal memory and communication platforms, not just smartphones.
- Forensic Data Analysis – investigators primarily focus on the analysis of structured data regarding financial institutions. The goal is to discover patterns, trends, or spot fraudulent activity by applying keyword searches or data mapping techniques.
Initially, digital forensics was done by skilled IT system administrators with general computer science knowledge, certifications, and training. But, as the need for cybersecurity and digital forensics grew, and digital crimes became more complex, these five cyber forensics specifications became necessary.
How does digital forensics work?
The science of digital forensics relies on the concept of our digital footprint. Unknown to us, every move we make on the internet leaves a trace.
Every time you visit a website, shop online, or send a tweet, a “paper trail” develops. Essentially, we all have digital records of our internet activity out there on the world wide web. Professionals in the field of computer forensics can take that data, analyze it, and produce solid evidence for criminal or civil cases being tried in a court of law.
A cyber investigator may be asked to recover deleted files, restore a damaged hard drive, crack encrypted passwords, discover the source of a security breach, and more. To perform these tasks effectively, some of the tools used can be complex. Packet scrapers, analysis tools across multiple devices and communication platforms, data capture tools, and file viewers are just some of the tools digital forensics investigators have at their disposal.
What are the phases of digital forensics?
Taking digital data in its raw form and turning it into viable evidence to be used by law enforcement can be complex. Generally, the overall process usually follows four distinct phases.
1. Seizure
The cyber investigation process starts with taking possession of the device in question. enforcement officials obtain a warrant and then physically take possession of the device holding the digital evidence. Law enforcement’s involvement is a crucial part of this step as it maintains the appropriate chain of custody with regard to evidence.
2. Acquisition
Once the raw data is physically in possession of law enforcement, cyber investigators work to duplicate files pertaining to the case. This is done using a hard drive duplicator or software imaging tool. Once the copy of the data is created, the original drive is stored safely and securely. At the same time, the digital evidence goes through several stages of validation to make sure it’s still in its original state.
3. Analysis
At this point in the process, cyber investigators will review the files copied from the original hard drive to see if they support or refute the charges brought against the accused. The investigator will call on various skills to analyze this data and get a complete picture of what actually happened during the events in question. Typically, this requires recovering deleted files, reviewing documents and internet history, chat logs, email, and may even require investigators to dig into the computer’s operating system cache.
4. Reporting
Once this data is mined and collected, it’s then translated and made presentable for court. It would be hard for police or attorneys to use in its raw form, so part of a cyber investigator’s job is to make this digital evidence relatable and understandable to non-IT members of the court system. From there, it’s examined further and hopefully will help prosecutors and law enforcement bring the alleged crime to a speedy resolution.
This step is a crucial part of what cyber forensics is. Without it, all of the effort seizing, acquiring, and analyzing the raw data would be wasted.
Why is digital forensics important?
The data recovery measures that are possible via computer forensics can play a crucial role in helping to bring threat actors to justice.
Often, hackers will attempt to destroy data or “cover their tracks” after committing a cybercrime or data breach. Destroying data may even be the technique they choose to harm their targets.
The efforts of cyber investigators can be instrumental in recovering or repairing the data involved in a cybersecurity event. Not only can these professionals repair or recover the data in question, but they can also identify any data that’s been removed from the system by cybercriminals. Considering how important and sensitive data has become in our modern world, digital forensics is an essential line of defense.
How can MSPs implement digital forensics for their clients?
As an MSP, your primary function is protecting your clients’ data. However, no one is perfect. Despite the lengths you may go to in protecting your clients’ network, cyberattacks are inevitable.
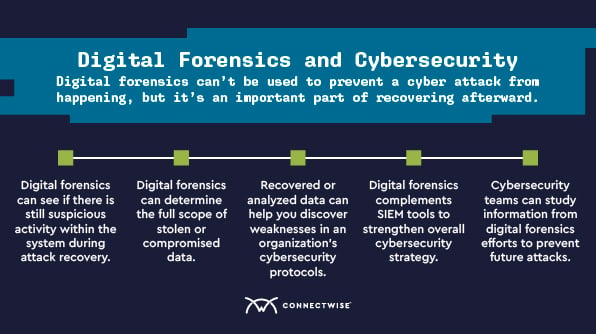
Digital forensics can be a valuable tool in helping MSPs strengthen their clients’ networks. The recovered or analyzed data can help you discover weaknesses in an organization’s cybersecurity protocols and take the steps necessary to strengthen them. Security information and event management (SIEM) tools are often a part of these protocols.
In the event of a cyber-attack, MSPs are also on the front lines. As the party responsible for their clients’ cybersecurity management, it falls on them to act quickly and immediately salvage any digital evidence. Doing so and managing the aftermath is the most critical part of any cybercrime investigation, whether this applies to email, ransomware, or other attacks.
What role does digital forensics play in cybersecurity?
Digital forensics and cybersecurity often overlap as digital forensics plays an important role in your threat response. It can’t be used to prevent an attack from happening, but it’s an important part of recovering afterward.
When an attack does happen to penetrate an organization’s cybersecurity measures, the information you learn from your digital forensics efforts can also be studied to prevent future attacks.
You’ll also be able to offer your clients the utmost protection by leveraging digital forensics to see if there is still suspicious activity within the system. From there, you can suggest steps your clients can take to neutralize these threats and reduce dwell time in the future.
Follow the footprint
Using digital forensics effectively is all about following the digital footprint. MSPs play an important role in what computer forensics is since they are the first line of defense for data protection. Organizations should take the time to make sure their MSP is an expert in the field and can provide the quick response necessary to save data and, ultimately, bring hackers to justice.
Are you ready to help your clients enhance their cybersecurity and stop threat actors in their tracks? Contact ConnectWise today for more information and to see the cutting-edge tools we have to offer.






