Responding to the ScreenConnect Vulnerability
This event was not a data breach, intrusion, or ransomware event
What happened?
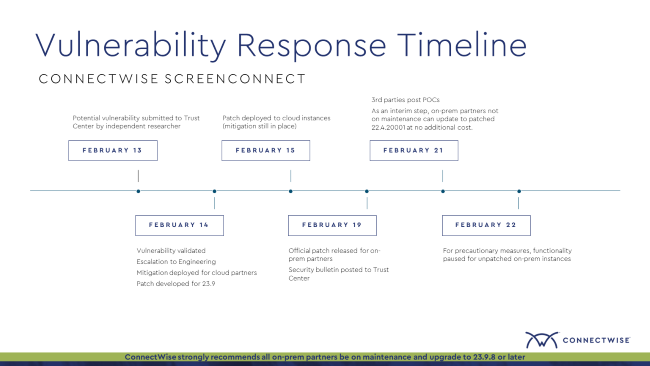
On February 13, 2024, an independent researcher ethically and responsibly reported a potential critical ConnectWise ScreenConnect™ vulnerability using the ConnectWise vulnerability disclosure program through the ConnectWise Trust Center.
What did ConnectWise do?
Once the vulnerability was validated on February 14, 2024, ConnectWise Product Security and Engineering teams worked together to mitigate all cloud instances of ScreenConnect within 48 hours. We did so without requiring a version update. Then, we upgraded cloud instances to a later version for further hardening. As a result, partners within our hosted cloud environments were quickly secured against this critical vulnerability.
Following industry best practices for patching strategy, an official upgraded package was released on February 19, 2024, for all on-prem ScreenConnect partners, and a security bulletin was posted to the ConnectWise Trust Center strongly recommending partners patch their on-prem instances of ScreenConnect. On the same day, ConnectWise initiated contact with CISA, and on February 22, CISA added CVE-2024-1709 to its Known Exploited Vulnerabilities (KEV) Catalog.
In addition, to provide timely information and support to our partners, we mobilized outreach communications through multiple channels, including security bulletins and advisories, partner emails, virtual events, and blogs. These communications emphasize the urgency to patch on-prem instances of ScreenConnect while providing our partners with the latest information, best practices, and support for this critical vulnerability.
External exposure and ConnectWise change in approach
On February 21, 2024, third parties publicly published proofs-of-concept (POCs)—and, in doing so, further exacerbated a challenging environment for customers patching their on-prem instances by increasing the risk of the vulnerability being exploited by threat actors. As a result, ConnectWise quickly took additional preventative measures to protect partners and their clients.
Additional mitigation measures implemented
We respect and appreciate that some partners may choose to host their own instance to manage patching priorities; however, because of the critical vulnerability, we recognized the heightened risk of exploitation with any patching delay. As a result, ConnectWise employed additional preventative measures by pausing functionality on servers of unpatched versions of on-prem ScreenConnect to prevent potential exploits. Other steps taken to mitigate risk include:
- No additional cost for on-prem partners not on maintenance: ConnectWise granted the ability for on-prem partners or customers who were no longer on maintenance to update to ScreenConnect 22.4.20001* at no additional cost. This allowed all partners to upgrade to a patched release of their on-prem ScreenConnect instance to remediate the critical vulnerability, regardless of their maintenance status.
- Pausing of ScreenConnect functionality: ConnectWise took further steps to pause ScreenConnect functionality for any on-prem partners who did not update to a patched version of on-prem ScreenConnect. Once a patched version of on-prem ScreenConnect is reinstalled, functionality is restored.
The pause functionality status leaves the ScreenConnect on-prem server active, so customers can still upgrade to a patched version. However, the on-prem server no longer allows generation of new sessions. Even in a paused functionality state, a ScreenConnect on-prem server is still vulnerable until the server is updated with a patched version.
*Note for partners or customers not currently under maintenance with on-prem versions of ScreenConnect between 22.4 and 23.9 please upgrade to your latest eligible patched version that includes the remediation for CVE-2024-1709.
Recommendations for ConnectWise partners or clients
All cloud instances of ConnectWise ScreenConnect are mitigated against CVE-2024-1709 and required no additional action.
If on-premise and under current maintenance:
Partners active with maintenance are strongly recommended to upgrade to the most current release of 23.9.8 or later. Using the most current release of ScreenConnect includes security updates, bug fixes, and enhancements not found in older releases.
If on-premise and NOT under current maintenance:
Partners not currently under maintenance are urged to upgrade their servers to at least version 22.4.20001, which includes the remediation for CVE-2024-1709. ConnectWise granted the ability for on-prem partners or customers who were no longer on maintenance to update to ScreenConnect 22.4.20001* at no additional cost. This allows all partners to upgrade to a patched release of 22.4.20001 to remediate the critical vulnerability, regardless of maintenance status.
*Note for partners or customers not currently under maintenance with on-prem versions of ScreenConnect between 22.4 and 23.9 please upgrade to your latest eligible patched version that includes the remediation for CVE-2024-1709.
If you’re a ScreenConnect partner and need additional assistance or have questions, please visit the ConnectWise Trust Center or contact our dedicated support team for help by visiting ConnectWise Home and opening a case or emailing help@connectwise.com.
Patch management
We recommend organizations establish communication channels with vendors and subscribe to their security advisories to ensure teams are always up to date with critical notifications. It’s essential to apply critical patches promptly to mitigate vulnerabilities, but monitoring third-party vendors for patches is equally important.
By combining vigilant monitoring of third-party patches and immediate action in critical situations, organizations strengthen their cybersecurity and reduce risk.
Security hardening for on-prem software
Security hardening for on-prem software involves implementing measures and practices to reduce vulnerabilities and protect against threats, which is crucial for preventing unauthorized access, data breaches, and ensuring the integrity and availability of critical systems. ConnectWise has two hardening guides for reference. The first guidance and best practices for Operating Systems and Networks and Applications. The Second is specific to the ScreenConnect vulnerability CVE-2024-1709. Customers should review and implement both for additional protection.
- ScreenConnect Hardening Guide by ConnectWise
- ConnectWise ScreenConnect Remediation and Hardening Guide by Mandiant
The ConnectWise ScreenConnect Hardening Guide includes the following:
- Security configurations such as managing access, 2FA, and SSL configuration
- Server configurations that block and restrict access to your ScreenConnect site
- User Authentication Options and the ability to revoke user access
- Recommended extensions for security such as reporting
The Mandiant Hardening Guide includes the following:
- Enabling baseline audit and privacy logs
- Proxy server and load balance configurations
- Restricting Egress
- Additional information on restricting permissions
ConnectWise recommends reviewing and implementing these hardening steps once your on-prem ScreenConnect instance has been patched and updated.
Importance of responsible disclosure
Vulnerability disclosure programs are an essential element of security strategy. They enable organizations to manage and mitigate cybersecurity risks, while fostering trust and collaboration with the security community and stakeholders. Promptly addressing reported vulnerabilities reduces the window of opportunity for attackers to exploit them. This can significantly lower the risk of incidents.
ConnectWise's response to the vulnerability disclosure showcases our commitment to security and partner protection. Promptly validating and addressing the vulnerability demonstrates a proactive approach to security. ConnectWise continues to prioritize security and encourages all customers to stay updated with the latest patches and releases to maintain a secure environment.
The benefit of cloud
Most ConnectWise ScreenConnect partners and customers use the cloud instance of ScreenConnect. For partners using ScreenConnect cloud, software patches and upgrades can occur automatically. This means that security vulnerabilities are addressed swiftly compared to on-prem software, where customers must manually apply patches. This issue is exacerbated for on-prem instances not on maintenance as partners may not apply patches or updates promptly, leaving systems vulnerable to exploitation.
SaaS providers, including ConnectWise, offer security measures that are often beyond the reach of individual organizations. This includes automatic scaling of security measures to meet changing needs, robust disaster recovery and data redundancy across multiple locations, and adherence to strict compliance and security standards. By offloading infrastructure maintenance to cloud providers, partners or customers can reduce the operational burden on their IT teams, allowing them to focus on other critical security tasks. This combination of flexibility, advanced security, and compliance support provides a level of protection that is challenging to achieve with on-prem solutions, especially those not covered by a maintenance agreement.
Misuse of remote control tools
Cyberattacks can occur through numerous avenues, including vulnerabilities, phishing, and business email compromise. While usually used for IT service delivery and product support, attackers can misuse remote control tools to facilitate malicious activities.


