Monthly Threat Brief: February 2024
Welcome to the latest edition of the monthly threat brief published by the ConnectWise Cyber Research Unit™ (CRU).
In this threat brief, we will provide raw data statistics, intel on specific threats, and a list of new detection signatures added to the ConnectWise SIEM™ throughout the month of February.
For a more detailed explanation of the overall trends and analysis of these numbers, check out our annual and quarterly threat reports. For comparison, January’s threat brief can be found here.
February 2024 stats
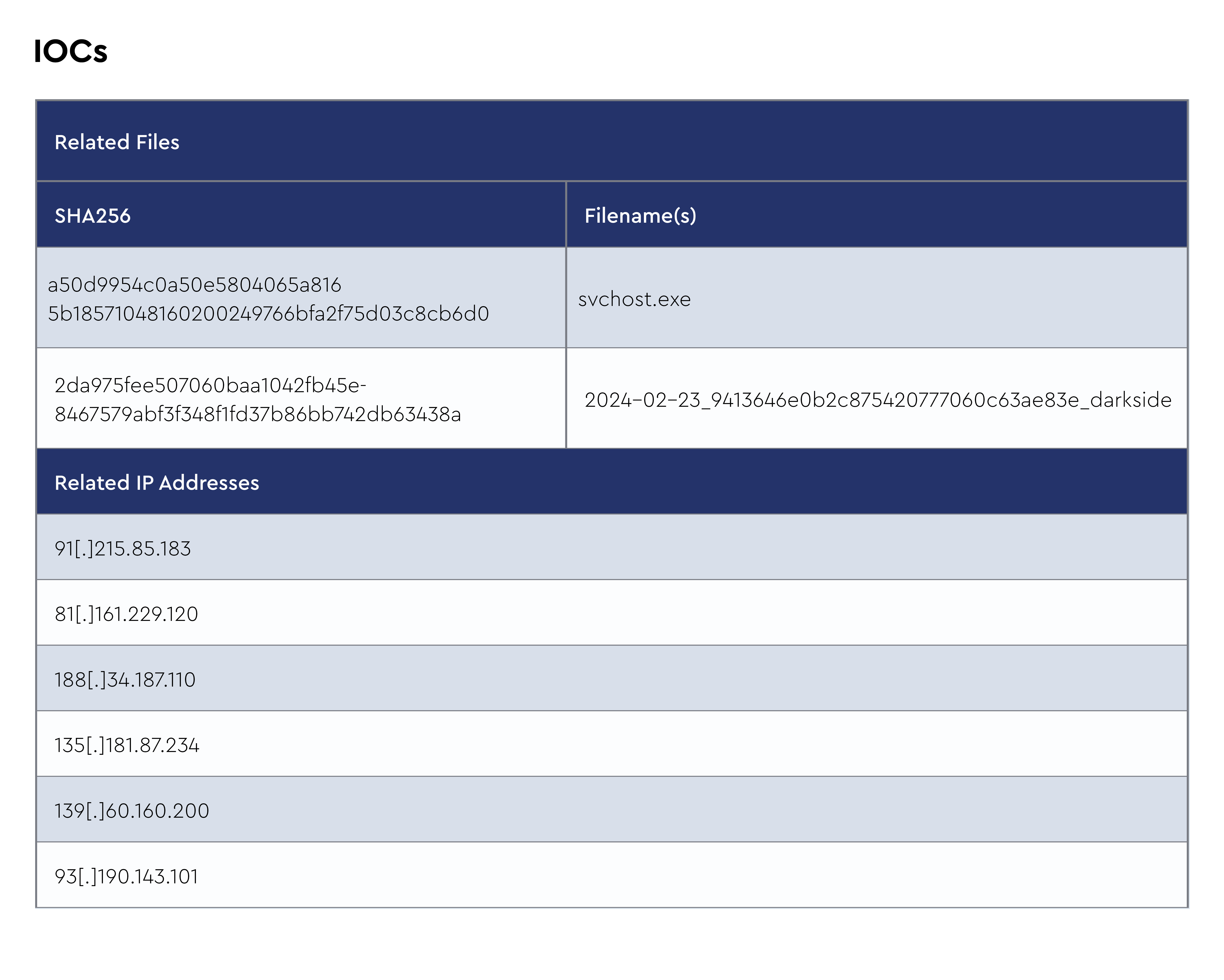
IOCs
The CRU collects indicators of compromise (IOCs) from public open-source intelligence (OSINT) sources and any cybersecurity incident escalated by the ConnectWise security operations center (SOC). These IOCs are used for automated threat hunting and data enrichment to assist SOC analysts. Below is a summary of the IOCs collected. We intend to launch streaming threat feeds based on this data later this year, so stay tuned!
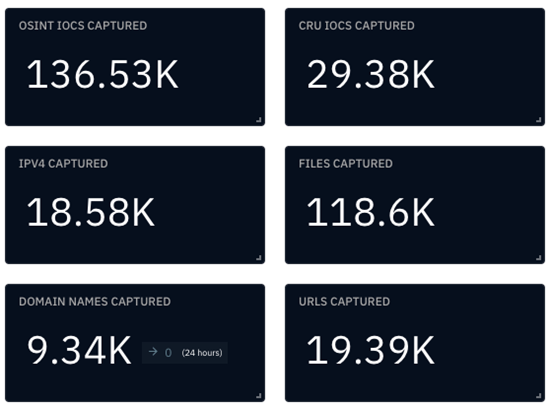
Figure 1: Summary of IOCs collected in February 2024
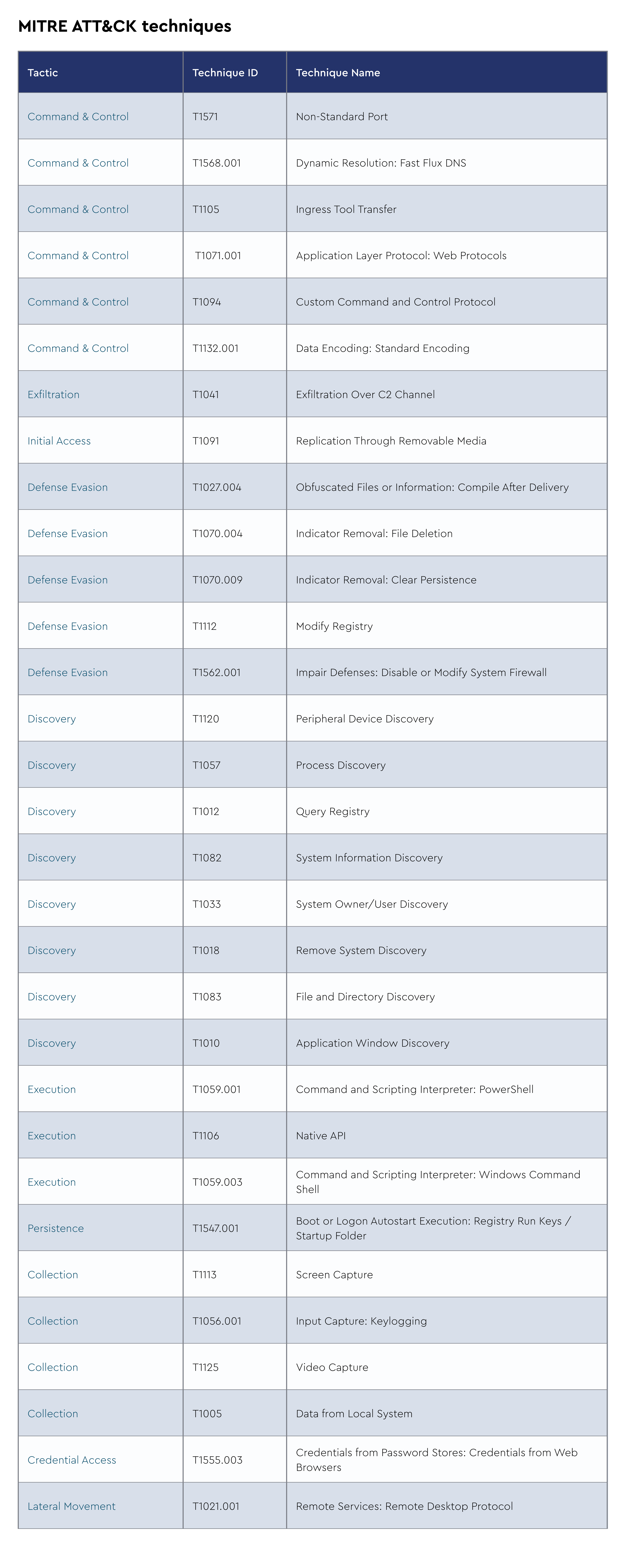
TTPs
The CRU collects tactics, techniques, and procedures (TTPs) from all incidents escalated by the ConnectWise SOC. This information helps us keep tabs on how threat actor behavior changes. Below are the top 10 MITRE ATT&CK® techniques for January 2024—provided for comparison—and February 2024.
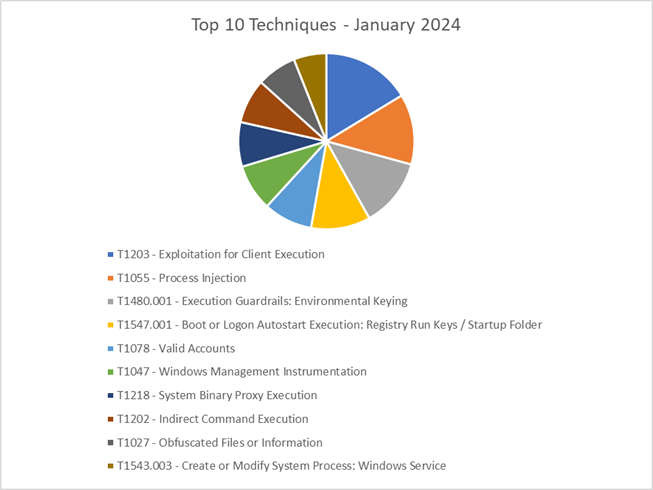
Figure 2: Top 10 MITRE ATT&CK techniques observed in January 2024
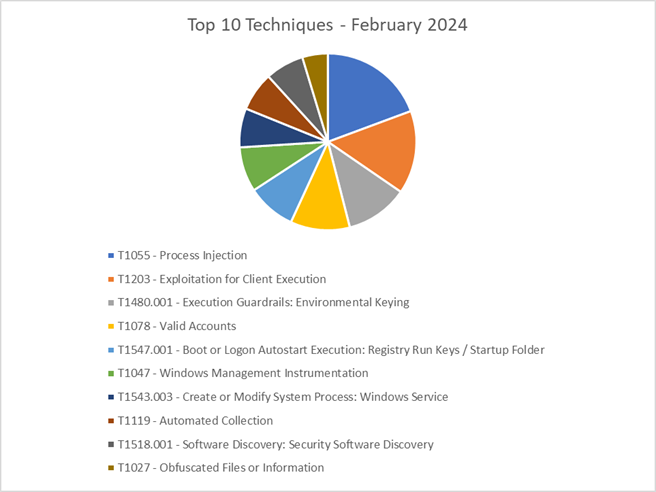
Figure 3: Top 10 MITRE ATT&CK techniques observed in February 2024
Latest threats
Each month, we highlight threats that we have seen targeting our MSP partners and their clients. This month, the ConnectWise SOC saw multiple incidents involving LockBit and njRAT.
LockBit
LockBit is ransomware that has been around since 2019, and it’s regularly among the most active ransomware groups—sometimes involved in three to four times as many breaches as other groups each month. They are a ransomware-as-a-service (RaaS) group that boasts the fastest encryption scheme of their competitors. Their rapid growth each month is mainly due to the success of their affiliate program.
On Tuesday, February 20, 2024, the UK’s National Crime Agency (NCA) released information about an “international disruption campaign targeting LockBit,” which they dub “the world’s most harmful cybercrime group.” Of the 4400 ransomware sightings the CRU recorded in 2023, around 25% were perpetrated by LockBit. According to the NCA, they took control of LockBit’s primary administration environment, which affiliates use to build payloads and manage their attacks, as well as their dark web site where victims’ data was leaked.
Additionally, the NCA was able to obtain over 1,000 decryption keys and worked with victims to help recover encrypted data. Unfortunately, LockBit had a new data leak site within a week of the initial takedown and they continue to extort victims.
njRAT
njRAT is a remote access tool (RAT) that has been in use since 2012 and is commonly associated with threat actors in the Middle East. However, its use has grown, and it has become one of the most widely used RATs on the internet. As a RAT, it includes common capabilities such as keylogging, stealing credentials from a victim’s browser, uploading and downloading files, modifying the registry, viewing a victim’s desktop, accessing the victim’s camera, and installing additional packages. Most recently, njRAT has been tied to Earth Lusca, a suspected China-based cyber espionage group, and Transparent Tribe, a suspected Pakistan-based threat group.
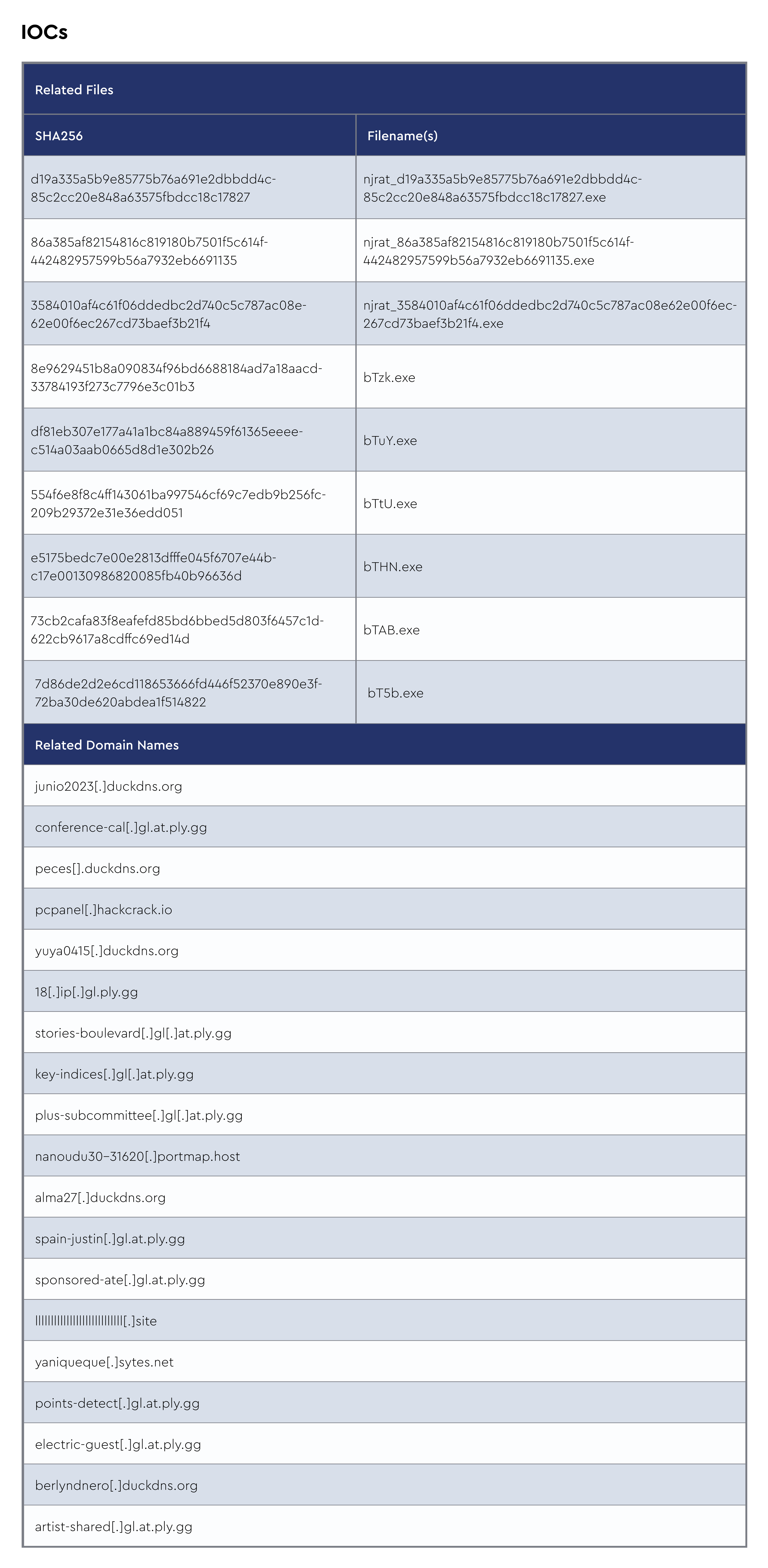
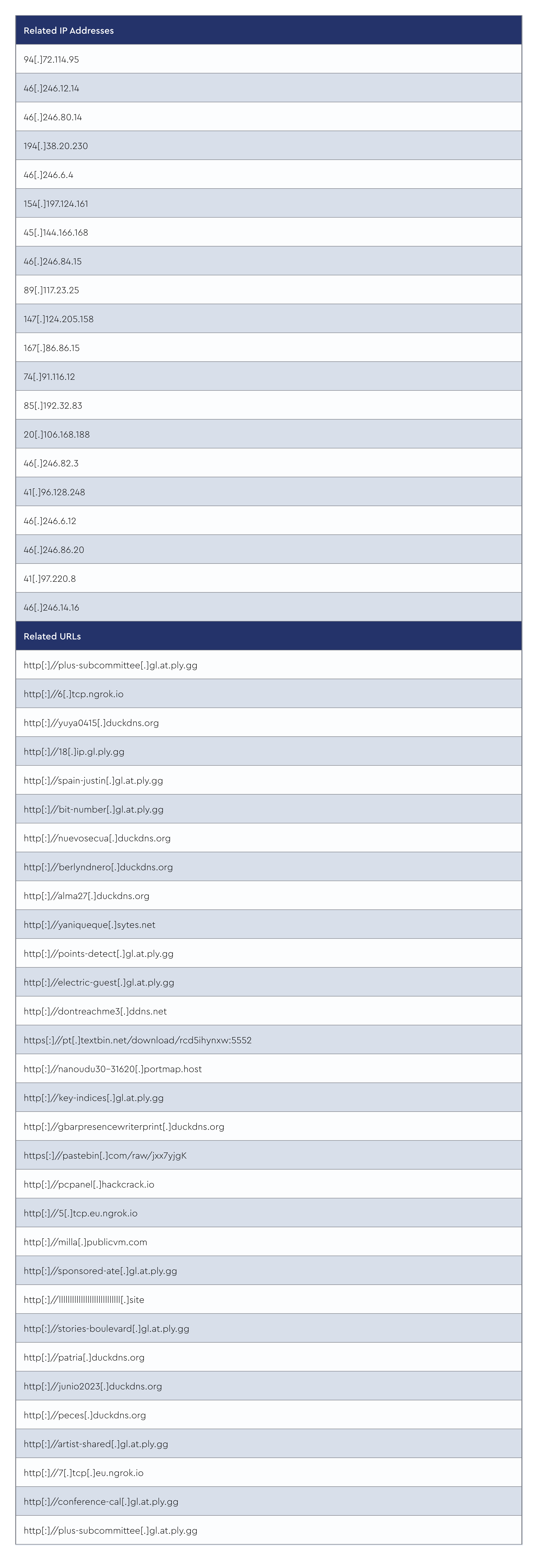
New ConnectWise SIEM signatures
Several new ConnectWise SIEM detection signatures were added in January 2024. These include:
- [CRU][Windows] XMRig Cryptominer Activity
Technique detected: [T1496] Resource Hijacking
Description: This alert triggers when a process with the default xmrig.exe process name is executed. XMRig is a crypto-mining software that can be deployed by threat actors to mine cryptocurrency. This activity should be verified for authorization with the partner.
- [CRU][Windows] AutoIt Executing From Atypical Directory
Technique detected: [T1059] Command and Scripting Interpreter
Description: AutoIt is a scripting language that has been observed in use by various malware families. It requires the interpreter binary Autoit3.exe, which in typical malicious cases will be dropped in a directory other than a program files directory where it would be expected.
New IDS signatures added in February 2024
[ConnectWise CRU] Ivanti Pulse Connect Secure SSRF (CVE-2024-21893) M1
[ConnectWise CRU] Ivanti Pulse Connect Secure SSRF (CVE-2024-21893) M2
[ConnectWise CRU] Ivanti Pulse Connect Secure (CVE-2024-21893) M3
[ConnectWise CRU] Oracle Weblogic T3\IIO Protocol (flowbit set)
[ConnectWise CRU] Oracle WebLogic T3\IIOP Protocol JNDI Injection (CVE-2024-20931)
[ConnectWise CRU] libuv Library (uv_getaddrinfo) Server-Side Request Forgery (CVE-2024-24806)
[ConnectWise CRU] SCAN QNAP NAS QTS OS Command Injection (CVE-2023-50358)
[ConnectWise CRU] ScreenConnect SetupWizard Authentication Bypass
[ConnectWise CRU] DICOM PACS Management Platform Unauthenticated RCE (CVE-2023-40150)
[ConnectWise CRU] AutoIt Script Files (au3/a3x) Download
[ConnectWise CRU] Microsoft Outlook Remote Code Execution (CVE-2024-21413)
[ConnectWise CRU] Pikabot C2 JA3S Hash (ec74a5c51106f0419184d0dd08fb05bc)
[ConnectWise CRU] Vulnerable ScreenConnect SetupWizard.aspx Authentication Bypass
[ConnectWise CRU] ScreenConnect App Extension Installation
[ConnectWise CRU] ScreenConnect App Extension Activity
[ConnectWise CRU] Bricks Builder Exploitation Attempt (CVE-2024-25600)
[ConnectWise CRU] Hidden AutoIt Script Files (au3/a3x) Download
[ConnectWise CRU] Apache Druid RCE (CVE-2021-25646)
[ConnectWise CRU] CLI Python Code Execution M1
[ConnectWise CRU] CLI Python Code Execution M2
[ConnectWise CRU] MALWARE PrivateLoader C2 Activity
[ConnectWise CRU] Impacket Default SMB Server GUID Detected


