
Cybersecurity training to build a savvy workforce
Your cybersecurity team isn't just a line of defense—it's the cornerstone of your business. And the stakes are sky-high. According to Stanford Research, 88% of data breaches are caused by human error. In this rapidly evolving cyberthreat landscape, an untrained team isn't just a risk—it's a glaring vulnerability.
Poor decision-making during critical incidents, delayed response times, and dwindling client trust not only damage your operations, but also can lead to the devastating loss of data or financial assets.
The solution here is comprehensive cybersecurity training for employees. This isn't just about ticking off a box; it's about building a continuous learning and awareness culture and empowering your team with the skills they need to tackle the ever-changing landscape of cyberthreats.
This chapter will guide you through the essential elements of effective cybersecurity training programs. It will cover the technical, soft, and compliance skills your team needs to excel, and show you how to weave in incident response strategies, an overlooked critical component.
Building your cybersecurity training program
Establishing rigorous cybersecurity training for employees extends beyond mere compliance requirements. It serves as a foundational pillar for an organization that can withstand cyberthreats effectively.
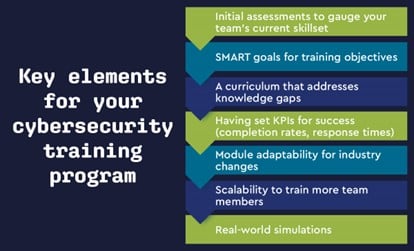
A well-crafted training program targets your organization's distinct needs—whether they are client-driven, compliance-based, or a blend of both. It all starts by identifying gaps in skillsets and knowledge.
Conduct an initial assessment through surveys, interviews, or even simulated cyberattacks to gauge your team's current level of cybersecurity awareness.
Based on the assessment outcomes, refine your training objectives. For example, if your team falls short in responding to simulated zero-day attacks, that’s an advanced focal point to prioritize.
Training objectives should be SMART—Specific, Measurable, Achievable, Relevant, and Time-bound. Why?
- Specific: In cybersecurity, ambiguity is your enemy. Objectives must be laser-focused, whether about fortifying firewalls or enhancing phishing awareness.
- Measurable: Metrics matter. Whether it's the reduction in security incidents or improvement in response times, quantifiable metrics enable you to gauge the effectiveness of your training.
- Achievable: Goals should stretch your team but remain within possibility. Overambitious objectives can lead to burnout and decreased morale.
- Relevant: Every training objective should align with your broader cybersecurity strategy and business goals. Irrelevant objectives dilute focus and waste resources.
- Time-bound: Cyberthreats evolve rapidly. Setting a timeline ensures that your team is always prepared for the most current risks rather than lagging behind.
Your training objectives might include high-level targets like "Achieving a 90% success rate in simulated advanced persistent threat (APT) exercises within six months" or "Certifying 80% of team members in incident response protocols by the end of the quarter."
These objectives will guide the curriculum and help measure the program's effectiveness later. You ensure a data-driven approach to assessing training outcomes by aligning these objectives with key performance indicators. This not only quantifies success, but also aids in making informed adjustments for future training cycles.
Once you've identified the gaps and set your objectives, it's time to build the curriculum. Tailor it to address the specific gaps you've identified. For instance, if your team needs to improve on data protection, modules on encryption and secure data handling could be beneficial.
Tailoring modules like these to address specific vulnerabilities elevates your team's skill set and aligns with real-world scenarios you're likely to encounter. This targeted approach ensures that the training is theoretical and immediately applicable.
For MSPs looking to avoid the heavy lift of developing in-house training programs, partners like ConnectWise offers cybersecurity certifications and MSP-specific training programs. These resources can help your team brush up on cybersecurity fundamentals, adopt industry and best practices, and become more proficient in addressing both routine and sophisticated cyberthreats.
While the identified gaps will dictate the focus areas, here are some common areas that you should consider:
- Social engineering exercises: These can range from simulated phishing attacks to more complex scenarios involving pretexting or baiting. The goal is to teach your team to recognize and respond to manipulative tactics used to gain unauthorized access to information.
- Cybersecurity awareness training: This is the bedrock of cybersecurity training programs. It should cover the basics, like password management, secure browsing practices, and how to identify phishing scams.
- Incident response training: Knowing how to respond when a security incident occurs is crucial. This training should include steps to contain the incident, communicate with the relevant parties, and restore and validate system functionality for business operations to resume.
Keeping your training program updated and consistently assessing its efficacy are crucial steps in maintaining a strong cybersecurity posture. Given the fluid nature of cyber risks, continual refinement is essential. Are you prepared to elevate your cybersecurity training? Your clients rely on your vigilance.
KPIs for training success
Wondering if your cybersecurity training is effective? Key Performance Indicators (KPIs) can offer valuable insights. These metrics serve as a mirror, reflecting the true impact of your training initiatives.
- Completion rates: Begin your KPI analysis with completion rates. A high rate signals an engaged and benefiting team. Low rates necessitate content reassessment for better engagement. For mandatory modules, scrutinize low rates for potential bottlenecks in the training process that may require attention.
- Practical application: Another crucial KPI is the practical application of the training. You'll want to track metrics like the number of security incidents and response times. Are there fewer breaches since the training? Is your team responding to threats more efficiently? These are tangible signs that your training is paying off.
- Behavioral changes: Don't underestimate the power of behavioral changes as a KPI. After the training, are employees adhering to best practices? Are they more cautious about potential threats? Sometimes, these subtle shifts in behavior can be more revealing than test scores alone.
KPIs serve as barometers for your team's skill development and the effectiveness of your cybersecurity training. By keeping a close eye on these metrics, you can transform your training initiatives from mere formalities into impactful elements of your organizational resilience.
Adapting your training program for the future
Adaptability is a key facet of any training program. Follow these notes on how to make your training program resilient and future-proof.
- Regular updates: The first step in future-proofing your training program is to keep it updated. Cyberthreats are not static; they evolve. So, update your content regularly to reflect the latest threats and best practices. Certifications can offer a structured, up-to-date curriculum that ensures your team is always ahead of the curve.
- Regulatory awareness: Regulations in the cybersecurity domain are also in a state of flux. Being aware of these changes is crucial. Incorporate the latest regulatory guidelines into your training modules to ensure ongoing compliance. This safeguards your organization and protects client data, enhancing your reputation as a trustworthy entity.
- Built-in flexibility: A rigid training program is a recipe for obsolescence. Design your program with built-in flexibility, allowing you to add or modify modules. This adaptability ensures you can quickly pivot your training focus to address emerging threats or updated regulations.
- Scalability: As your organization grows, your training program should scale. Design your training modules to accommodate an increasing number of participants without compromising quality.
- Real-world simulations: Cyberthreats are not confined to textbooks. Incorporate real-world simulations in your training to prepare your team for scenarios they might face. This hands-on approach enhances skill retention and application.
- Feedback loop: Establish a feedback mechanism. Collect data on the effectiveness of your training and use it to make informed adjustments. This keeps your program aligned with both current needs and future trends.
By integrating these elements, you're building a dynamic learning ecosystem within your cybersecurity training program.
Practical resources for cybersecurity training
Regarding training, a multi-faceted approach is essential for comprehensive education. This means combining theoretical knowledge with hands-on exercises and integrating real-world incident response scenarios to build a well-rounded skill set.
By doing so, you're not just imparting information but cultivating the adaptability needed to navigate an ever-evolving threat landscape.
Here’s how you can leverage various resources to build a robust training program for your team:
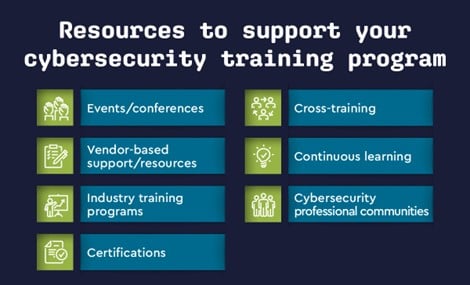
- Events and conferences: Sending your team to specialized cybersecurity training events can provide invaluable insights and networking opportunities. These events often feature industry experts and offer hands-on workshops that can’t be replicated in a traditional training setting.
- Vendor support/resources: Many vendors offer training resources specifically designed for their products. Using these can help your team get the most out of the tools you already use, increasing efficiency and security.
- Common programs/certifications: Key certifications like CompTIA Security+, CISSP, and CEH offer a strong foundation and industry recognition. Additionally, frameworks such as the NIST Cybersecurity Framework provide MSPs with best practices to focus on, making them valuable models for essential security protocols.
- Cross-training and continuous learning: The cybersecurity landscape is in constant flux. Bolster resilience by cross-training team members, such as having network engineers learn about phishing detection. Continuous learning through online courses or internal workshops ensures your team stays ahead of emerging threats.
- Community support: Don’t underestimate the value of community in professional development. ConnectWise’s IT Nation community is a valuable resource for sharing best practices, learning from peers, and staying updated on industry trends.
This proactive approach elevates your team's capabilities, shifting the focus from mere compliance to a dynamic, ever-improving security posture.
Cybersecurity training vs outsourcing
Many MSPs are faced with a critical decision here. Should you invest in internal training or outsource to specialists like Managed Security Service Providers (MSSPs) or Security Operations Centers (SOCs)?
The answer isn't as straightforward as you might think. Both approaches have unique advantages and complement each other. And, ultimately, the solutions and technologies available to MSPs today make it possible to provide top-notch security protection without engaging an MSSP.
Training your internal team is a long-term investment, but it can foster a culture of cybersecurity awareness where each team member is a first line of defense. An in-house team also understands your specific operational needs, which may help them respond more quickly and effectively to incidents. Internal training is often the best route for tasks core to your business. For example, training your team on HIPAA compliance is invaluable if you specialize in healthcare IT.
On the flip side, outsourcing has its merits. It's ideal for tasks requiring specialized expertise or impractical resources to develop in-house. For instance, 24/7 security monitoring might require staffing levels that aren't feasible for smaller MSPs. In such cases, an MSSP or managed SOC services can fill this gap while increasing your capacity and diversity of expertise. Dedicated security experts may also have the most current knowledge and tools.
The key is synergy. A blend of internal training and outsourcing often yields the most effective cybersecurity posture. Your internal team could handle routine audits and basic incident response. Consider outsourcing more complex tasks like forensic analysis.
This hybrid approach streamlines resources and fosters adaptability in your cybersecurity strategy. By leveraging both internal talent and third-party MSSP or SOC expertise, you build a robust, scalable defense that's agile in responding to evolving threats.
For more tips on building a resilient cybersecurity practice, download our eBook, The Ultimate Operations Guide for MSP Cybersecurity.
Complement training with top cybersecurity solutions
Training is an ongoing, evolving necessity. Cyberthreats are dynamic, and your training approach should be, too. Continuous learning remains crucial, whether it's updated cybersecurity awareness or new software features.
But effective cybersecurity isn't solely about having the right tools in your security stack—it requires mastering their use. Embracing the latest developments in automation and giving your tech access to modern cybersecurity software and solutions can refine and refocus training needs, and ultimately reduce the amount of routine maintenance your techs are responsible for.
ConnectWise offers a suite of cybersecurity management software to help ensure your cybersecurity team and infrastructure are evolving at the speed of market demand. When combined with effective training practices, best-in-class security solutions can give your MSP an edge over the competition and help future-proof your practice.
Take a demo of our cybersecurity suite to see our solutions in action or visit the ConnectWise cybersecurity center for more tools and training resources for MSPs.
FAQs
Conduct a comprehensive skills assessment using performance reviews and cybersecurity programs to identify training gaps. This data-driven approach will highlight specific areas where your team is lacking.
After identifying the gaps, create targeted training modules focusing on these weaknesses. Incorporate real-world scenarios, particularly incident response-related ones, to make the training actionable and relevant.
Technical cybersecurity training should occur quarterly. This cadence aligns with the fast-paced changes in the cybersecurity landscape. By training quarterly, you ensure that your team is always up-to-date with the latest threats and solutions.
In addition to quarterly sessions, consider micro-training to address immediate concerns or updates. These bite-sized sessions can be easily integrated into your team's workflow. A commitment to continuous learning will equip your team to proactively counter emerging cybersecurity threats.
Key metrics for gauging the success of internal training include reduced incident response times, fewer security breaches, and high post-training assessment scores. A decline in response times indicates your team's improved ability to identify and address threats swiftly.
High assessment scores post-training validate the program's effectiveness. Fewer security breaches confirm that your team is applying what they've learned. These metrics collectively offer a comprehensive view of your training's impact, enabling you to make data-driven decisions for future training initiatives.
Critical ongoing training for internal security teams should emphasize threat detection, incident response, and compliance. Keeping courses updated is essential, given the ever-changing nature of cybersecurity threats.
Hands-on exercises and real-world simulations are non-negotiable components of effective training. These methods ensure your team gains practical experience, equipping them to adapt to the evolving cybersecurity landscape.



